AWS EventBridge
The Scalr integration with EventBridge allows users to build event-driven Terraform and OpenTofu pipelines based on events that happen in Scalr. The events are streamed to EventBridge which can trigger actions in AWS, a partner integration source, or any other third party.
Prerequisites
- AWS Account: An active AWS account with permissions to create and manage EventBridge rules and other related resources.
- Scalr Account An active Scalr account with the necessary permissions to configure integrations and manage cloud environments.
Use cases
Automated Infrastructure Monitoring and Alerting
When Scalr is integrated with AWS EventBridge, users can stream run executed events to the event bus. This enables real-time monitoring of infrastructure changes initiated by Terraform runs. Users can set up EventBridge rules to trigger alerts or notifications based on specific criteria, such as infrastructure updates or failures in critical environments/workspaces.
Audit Logging
By streaming users’ activity from Scalr to EventBridge, organizations can maintain a comprehensive audit trail of all actions taken in an account. This includes tracking changes made to resources across different Scalr services. Users can leverage this audit logging capability for compliance purposes, troubleshooting, and historical analysis of Scalr changes.
Integration with Third-Party Systems for Workflow Automation
Leveraging the integration between Scalr and EventBridge, organizations can orchestrate workflow automation across their ecosystem. For example, users can create EventBridge rules to trigger actions in response to specific API events, such as provisioning additional resources in response to a Run Executed event. This integration streamlines processes, improves efficiency, and enables seamless collaboration between different teams and systems within the organization.
Configuration
-
Log in to your AWS account and obtain the AWS account ID
-
Log in to your Scalr account, go to Account scope, Integrations, and create a new AWS EventBridge connection:
-
Enter the connection name, AWS account ID, and AWS region. The combination of AWS account ID and region must be unique in your account.
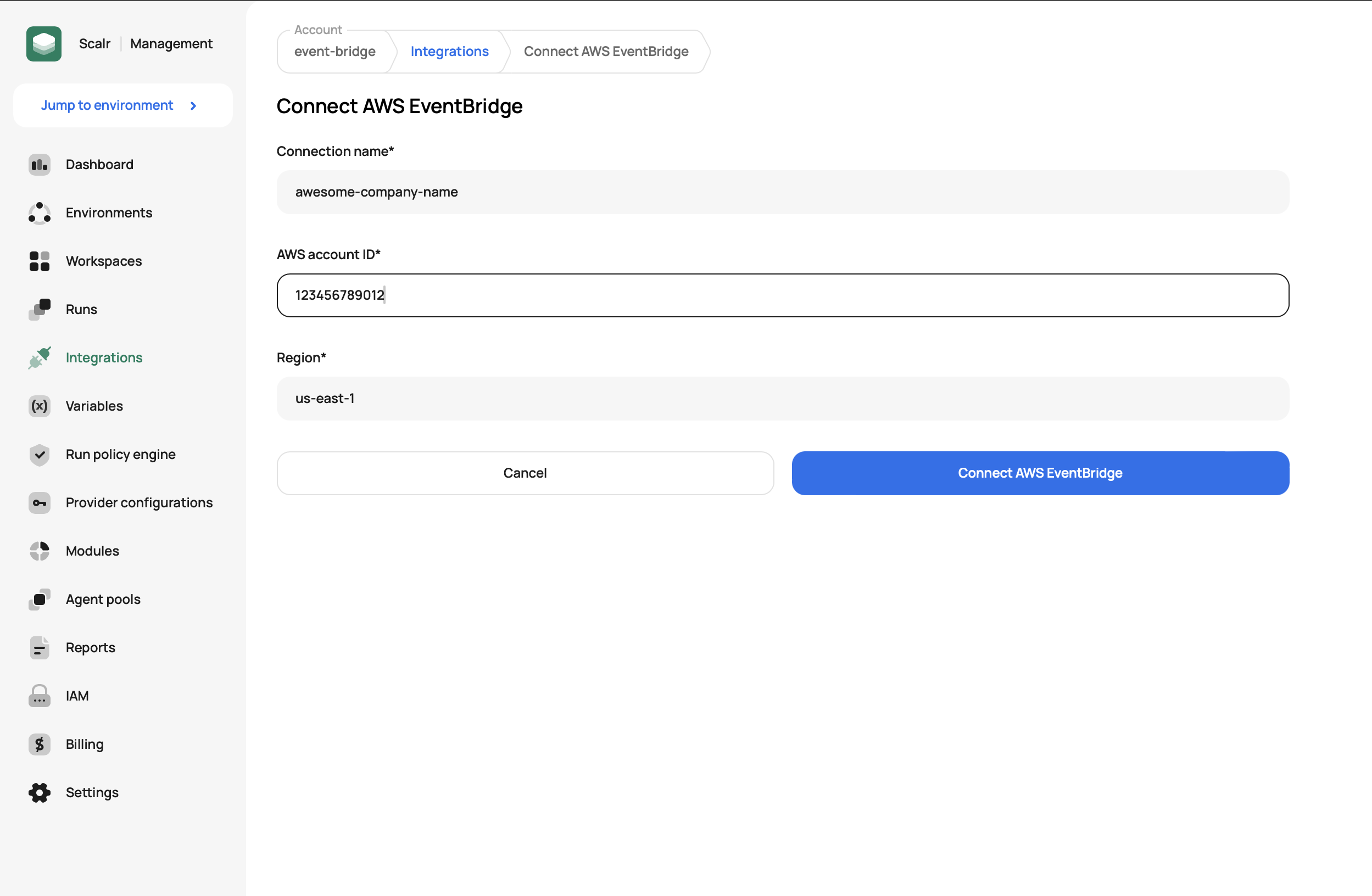
-
Once a connection is created, you must finalize an event source creation in the AWS console. To do that, click on the partner source link given in the banner on top of the created connection:
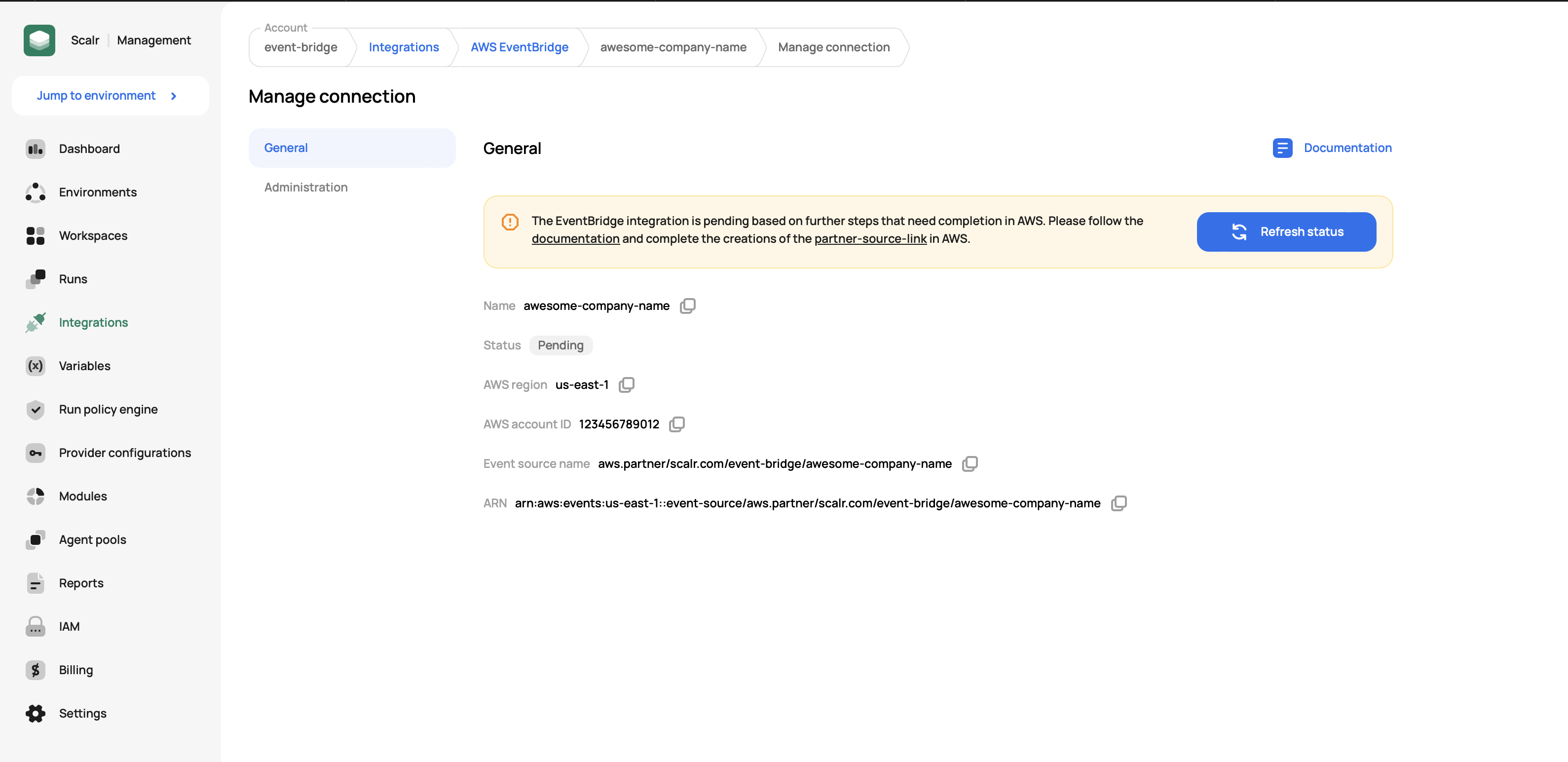
-
In the AWS console click on the Associate with event bus button and complete the action:
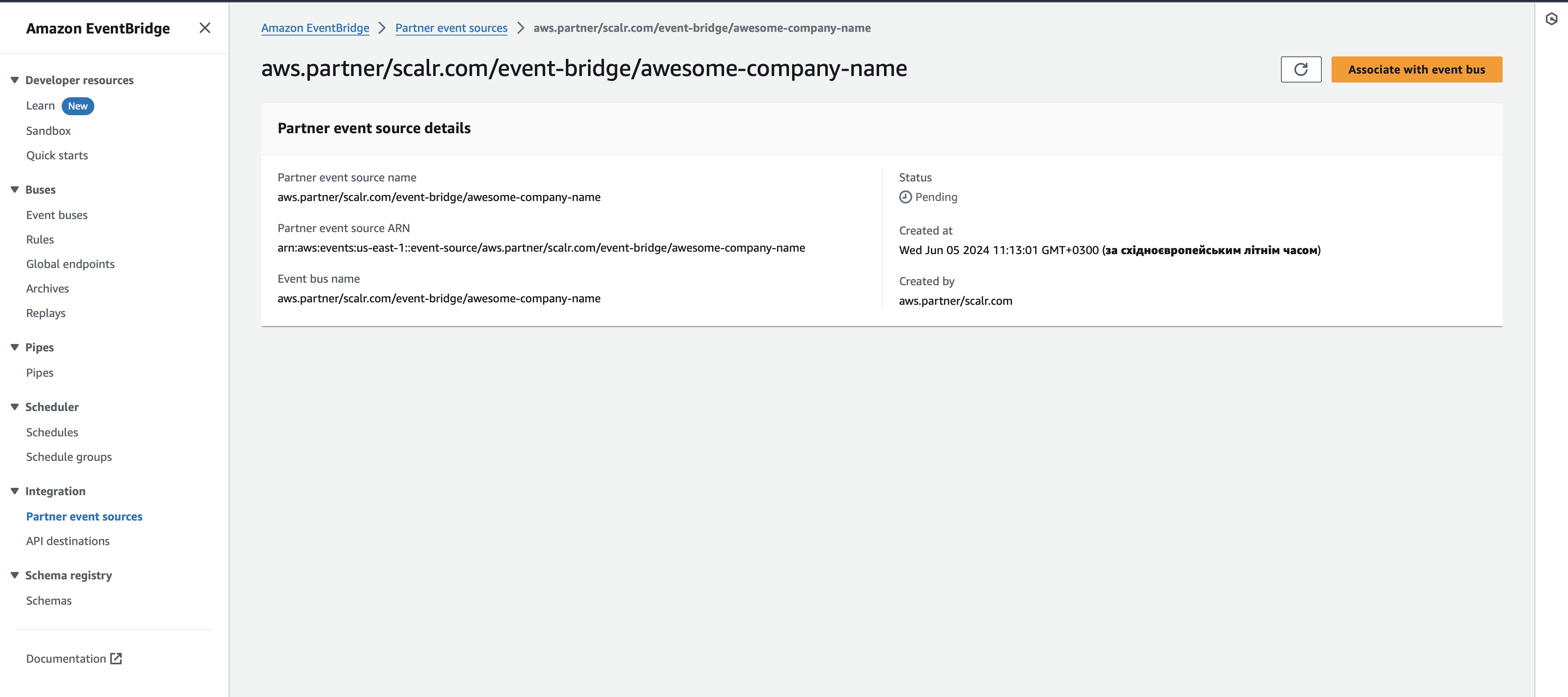
-
Once the event source is associated with the event bus, you must create an event rule to forward events from Scalr to the destination of your choice. In the following example, we'll configure forwarding of the Run Executed event to the AWS CloudWatch service.
-
To complete rule creation, go to Event buses, select the recently created bus, and click on the Create rule button:
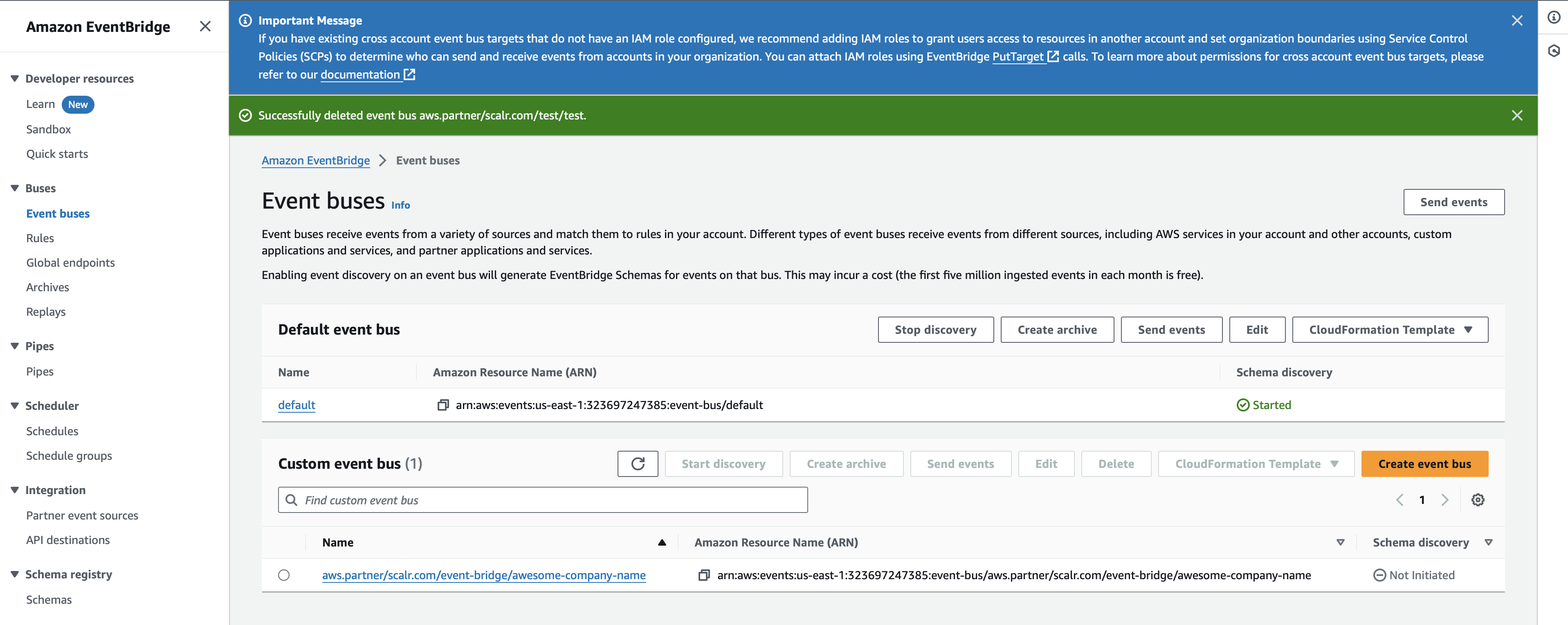
-
Enter a rule name, optionally its description, the event bus will be populated automatically and keep the Rule type as Rule with an event pattern and click the Next button:
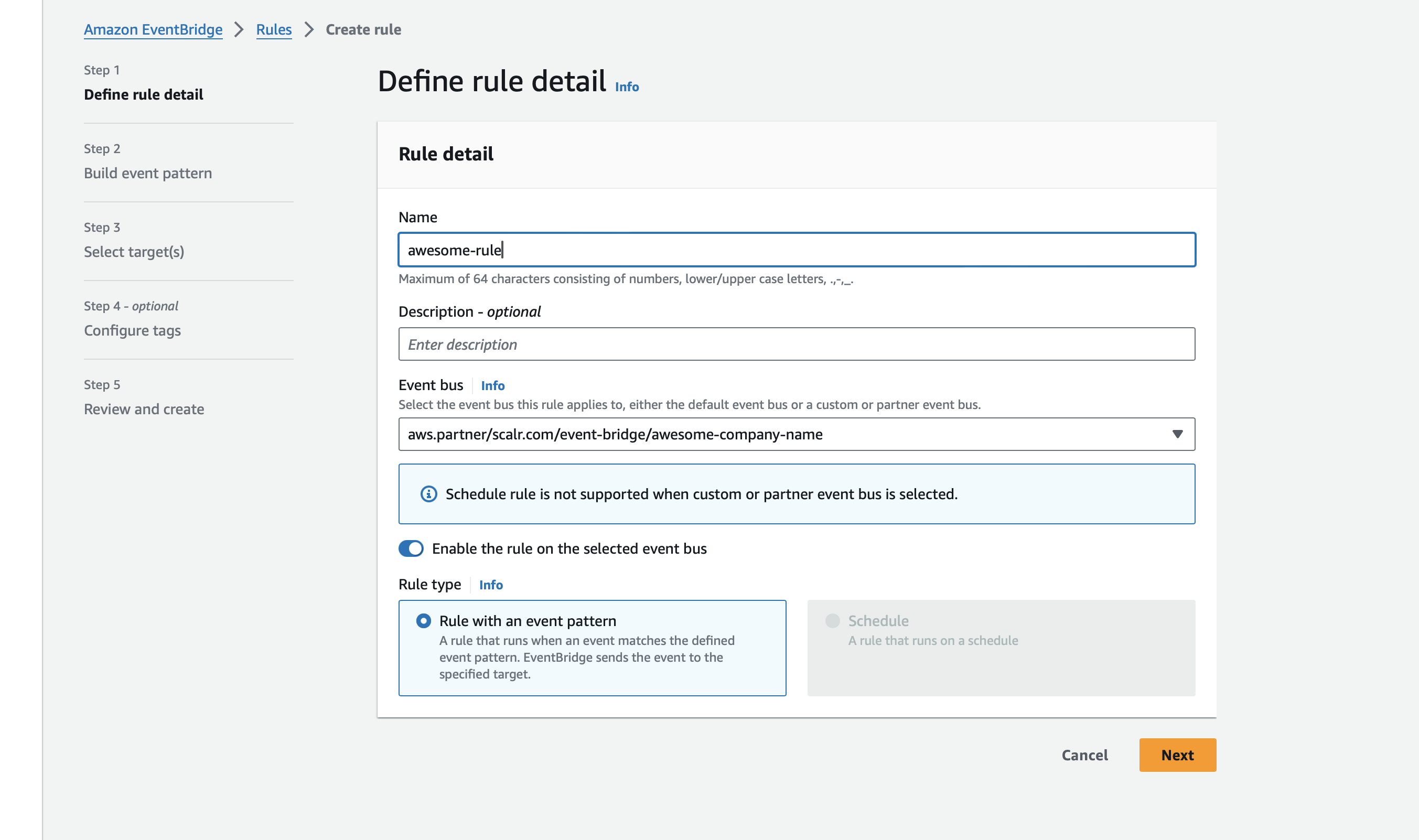
-
In the Event source keep the AWS events or EventBridge partner events value selected.
-
In the Sample event click on the Enter my own option and paste the following JSON snippet:
-
{ "id": "run-1234567890", "account": "test", "version": 1, "time": "2024-04-19T13:44:02Z", "source": "aws.partner/scalr.com/account-name/integration-name", "resources": [], "region": "us-east-1", "detail-type": "RunExecuted", "detail": { "title": "Scalr run execution completed on workspace 'workspace-name' (environment-name). Run ID: run-1234567890.", "event": { "run-id": "run-1234567890", "source": "vcs", "is-dry": false, "is-destroy": false, "is-agent": false, "is-postponed": false, "result": "applied", "duration": 137000000000.0, "account": "account-name", "workspace": "workspace-name", "environment": "environment-name", "user-email": "[email protected]", "run-url": "https://my_acc.scalr.io/v2/e/env-11111/workspaces/ws-111111/runs/run-111111", "vcs": { "repository": "my-org/my-repo", "branch": "main", "commit": { "sha": "deecfbbda1267982bc3a971a57e2eabda09452e", "message": "for_each_config", "html-url": "https://github.com/my-org/my-repo/commit/deecfbbda1267982bc3a971a57e2eabda09452e" } }, "provider-configurations": [ { "name": "scalr-auth", "provider-name": "scalr", "auth-type": "token" } ], "policy_failures": [ { "policy-group": "policy-group-name", "policy": "ws_name", "enforcement-level": "advisory", "messages": [ "Failure reason 1", "Failure reason 2" ] } ], "connection-name": "integration-name" }, "tags": [ "scalr-environment:env-1234567890", "scalr-workspace:ws-1234567890", "scalr-environment-name:environment-name", "scalr-workspace-name:workspace-name" ], "event_type": "success" } }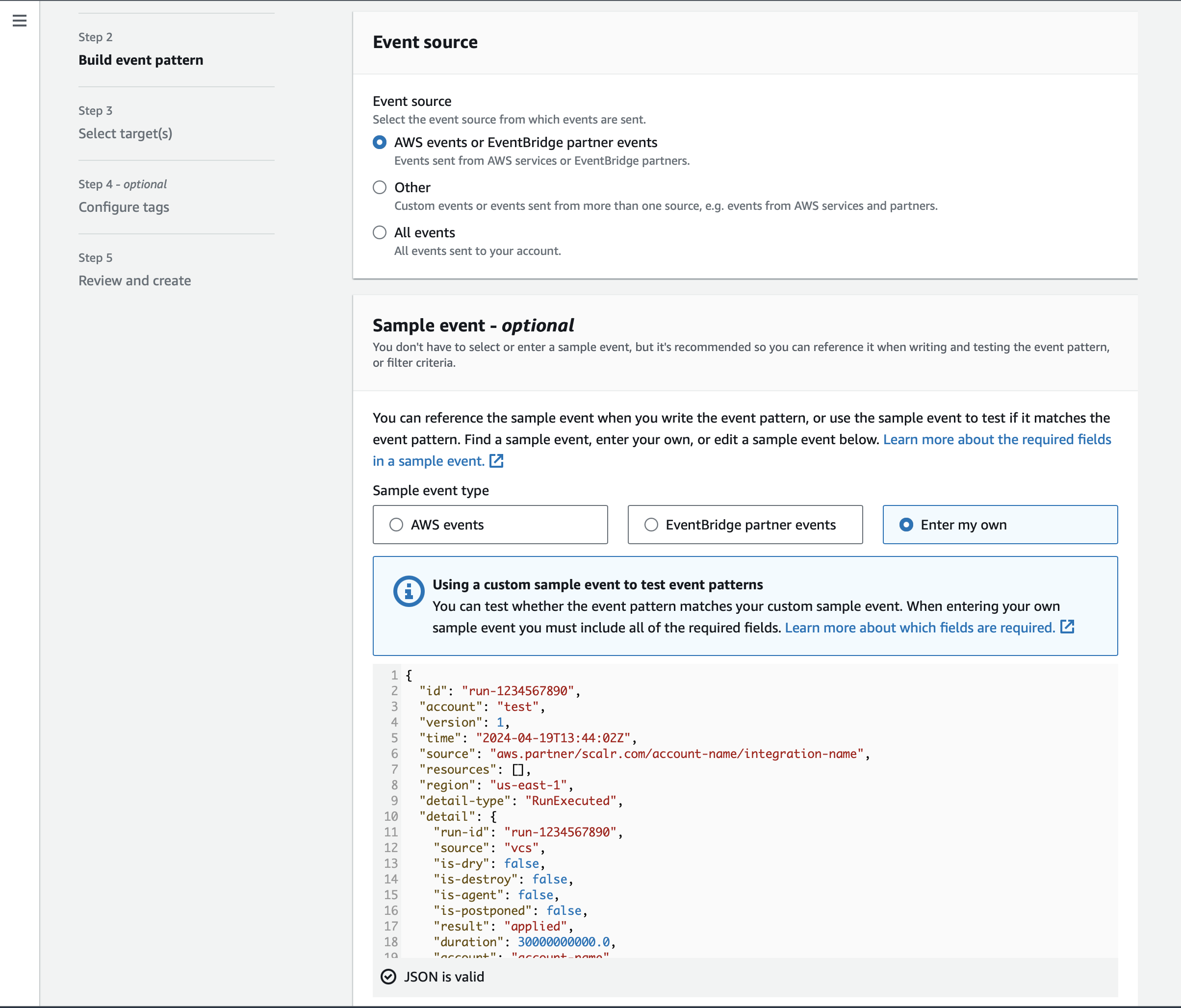
-
In the Creation method section select the Custom pattern option, and paste the following JSON snippet, and click on the Test pattern button:
-
{ "source": [{ "prefix": "aws.partner/scalr.com" }], "detail-type": ["RunExecuted"] } -
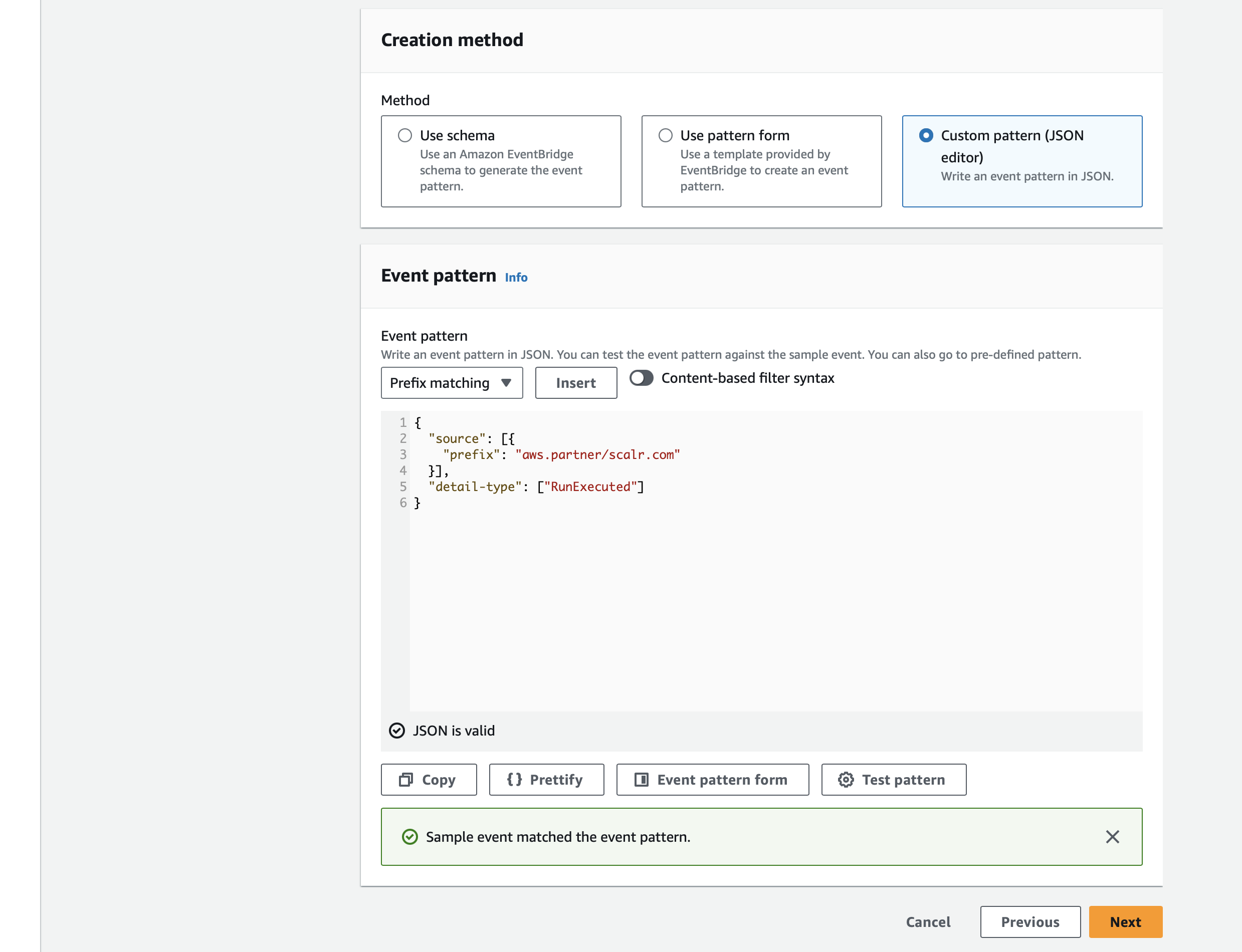
Then click on the Next button and start the configuration of the destination. In this case, it will be CloudWatch log group:
-
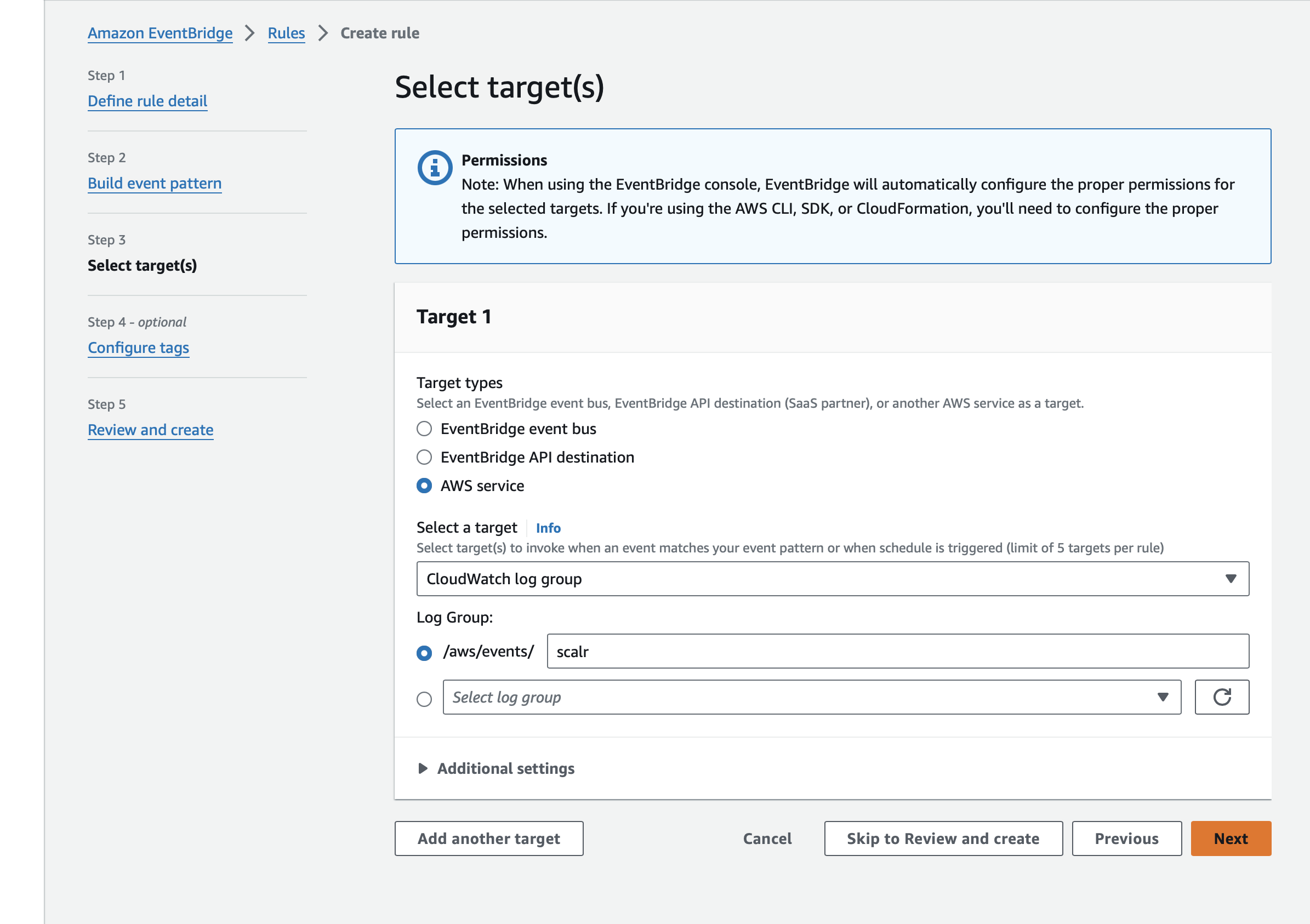
Optionally, you add tags to your rule, review it, and finalize the creation.
-
Once a rule is created, you need to refresh the Event source status to make a connection active. In the connection details, click on the Refresh status button:

-
Once a connection becomes active, check the RunExecuted events are streamed to the CloudWatch log group.
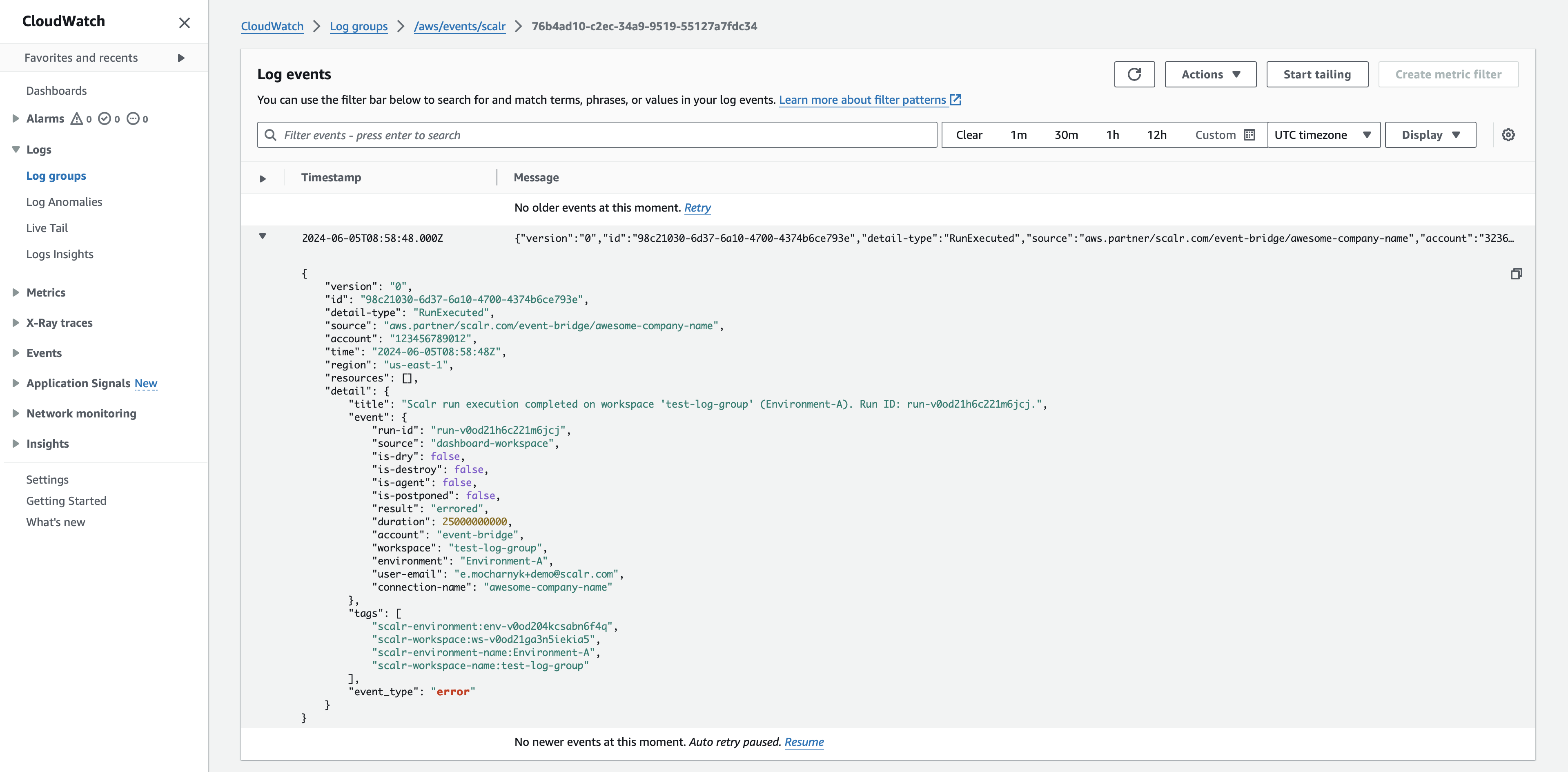
Event detail types
Scalr streams two types of events: RunExecuted and AuditLog.
Run Executed
The RunExecuted event is streamed automatically without additional configuration once a connection between Scalr and AWS EventBridge is established. The following event sample and pattern can be used while configuring the event bridge rule:
{
"id": "run-1234567890",
"account": "test",
"version": 1,
"time": "2024-04-19T13:44:02Z",
"source": "aws.partner/scalr.com/account-name/integration-name",
"resources": [],
"region": "us-east-1",
"detail-type": "RunExecuted",
"detail": {
"title": "Scalr run execution completed on workspace 'workspace-name' (environment-name). Run ID: run-1234567890.",
"event": {
"run-id": "run-1234567890",
"source": "vcs",
"is-dry": false,
"is-destroy": false,
"is-agent": false,
"is-postponed": false,
"result": "applied",
"duration": 137000000000.0,
"account": "account-name",
"workspace": "workspace-name",
"environment": "environment-name",
"user-email": "[email protected]",
"run-url": "https://my_acc.scalr.io/v2/e/env-11111/workspaces/ws-111111/runs/run-111111",
"vcs": {
"repository": "my-org/my-repo",
"branch": "main",
"commit": {
"sha": "deecfbbda1267982bc3a971a57e2eabda09452e",
"message": "for_each_config",
"html-url": "https://github.com/my-org/my-repo/commit/deecfbbda1267982bc3a971a57e2eabda09452e"
}
},
"provider-configurations": [
{
"name": "scalr-auth",
"provider-name": "scalr",
"auth-type": "token"
}
],
"policy_failures": [
{
"policy-group": "policy-group-name",
"policy": "ws_name",
"enforcement-level": "advisory",
"messages": [
"Failure reason 1",
"Failure reason 2"
]
}
],
"connection-name": "integration-name"
},
"tags": [
"scalr-environment:env-1234567890",
"scalr-workspace:ws-1234567890",
"scalr-environment-name:environment-name",
"scalr-workspace-name:workspace-name"
],
"event_type": "success"
}
}{
"source": [{
"prefix": "aws.partner/scalr.com"
}],
"detail-type": ["RunExecuted"]
}Note that the vcs, provider-configurations, and policy_failures event keys are optional and context-dependent; e.g., a CLI run will not include a vcs block.
Audit Log
The AuditLog event is streamed after the respective setting is enabled in the Account settings if the connection between Scalr and AWS EventBridge is established. To enable audit logs, go to Settings on the account scope, click on the Audit logs menu item, and select the created connection:
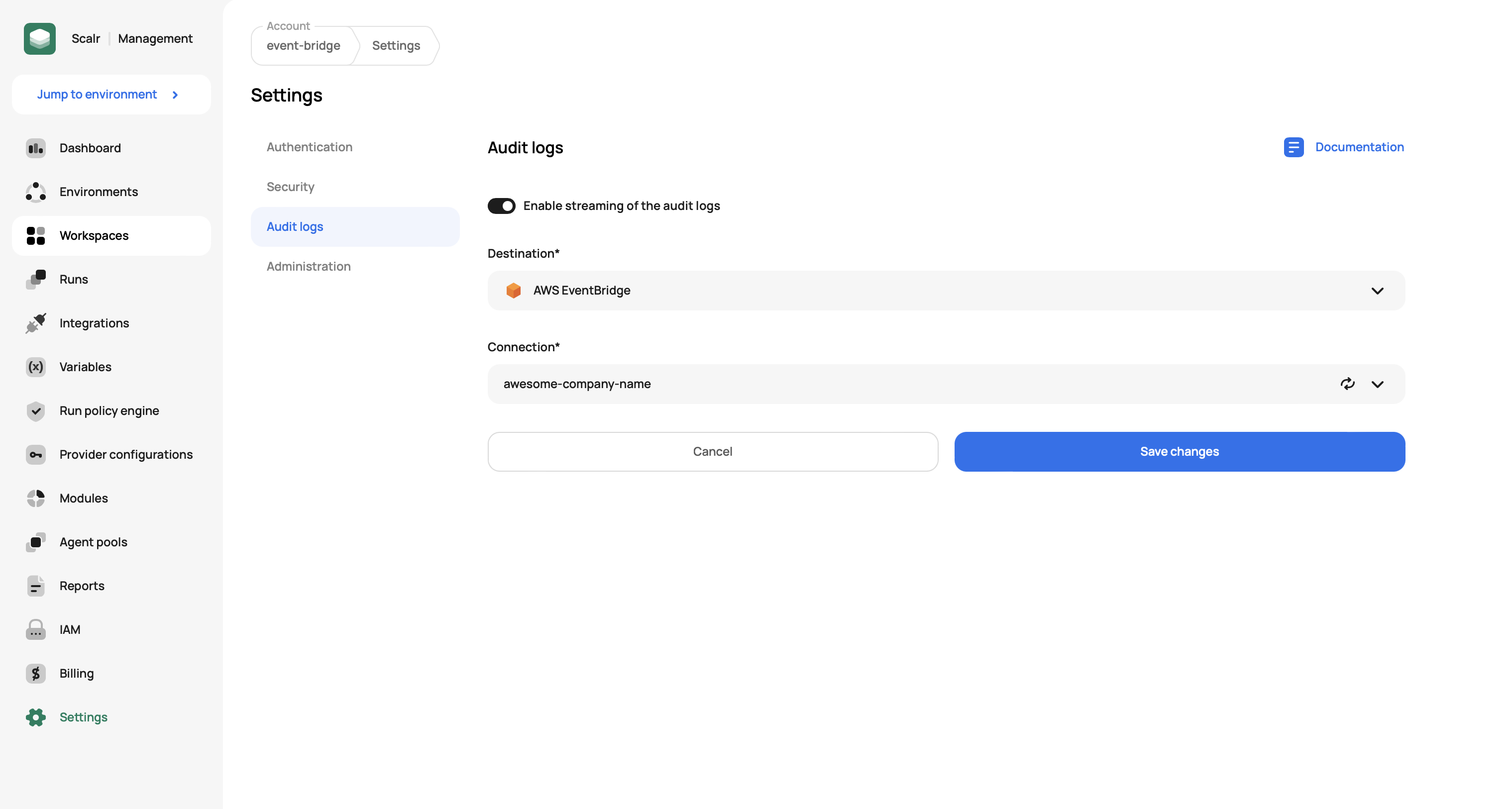
The following event sample and pattern can be used while configuring the event bridge rule:
{
"id": "63ddd008eced0487812b1005f06ddff4",
"version": 0,
"account": 123456789012,
"time": "2024-04-19T13:44:02Z",
"source": "aws.partner/scalr.com/account-name/integration-name",
"resources": [],
"region": "us-east-1",
"detail-type": "AuditLog",
"detail": {
"target": {
"id": "ws-1234567890",
"type": "workspaces",
"display-name": "workspace-name",
"context": {
"environment": {
"id": "env-1234567890",
"display-name": "environment-name"
},
"workspace": {
"id": "ws-1234567890",
"display-name": "workspace-name"
},
"account": {
"id": "acc-1234567890",
"display-name": "account-name"
}
}
},
"timestamp": "2024-04-19T13:44:02.335490",
"request": {
"id": "63ddd008eced0487812b1005f06ddff4",
"action": "create-workspace",
"ip-address": "10.21.0.30",
"source": "ui",
"user-agent": "Mozilla/5.0 (X11; Linux x86_64; rv:125.0) Gecko/20100101 Firefox/125.0"
},
"actor": {
"id": "user-1234567890",
"email": "[email protected]",
"type": "user",
"access-token": {
"id": null,
"type": "session",
"token": "...UlzZ-c"
}
},
"outcome": {
"result": "SUCCESS",
"status-code": 201
},
"tags": [
"scalr-action:create-workspace",
"scalr-user-email:[email protected]",
"scalr-environment:env-1234567890",
"scalr-environment-name:environment-name",
"scalr-workspace:ws-1234567890",
"scalr-workspace-name:workspace-name"
]
}
}{
"source": [{
"prefix": "aws.partner/scalr.com"
}],
"detail-type": ["AuditLog"]
}Audit Log Disabled Alerts
To maintain compliance and visibility, Scalr sends an AuditLogDisabled event when audit log streaming is disabled or switched to a different destination. This ensures admins are immediately notified of changes that may introduce security or compliance risks.
Example Event:
{
"version": "0",
"id": "6d475ada-25dd-2374-7b6b-ecc56a4c0eec",
"detail-type": "AuditLogDisabled",
"source": "aws.partner/company.com/account/test",
"account": "010438481993",
"time": "2025-04-17T15:25:55Z",
"region": "eu-north-1",
"resources": [],
"detail": {
"title": "Audit Log Disabled. ",
"timestamp": "2025-04-17T15:25:55.632471+00:00",
"user-id": 111,
"user-email": "[email protected]",
"disabled-integration": {
"id": "in-123456789",
"name": "test",
"type": "AWS EventBridge"
}
}
}Set Up an Alert in AWS EventBridge
Use the following pattern in your EventBridge rule to capture these events:
{
"source": [{
"prefix": "aws.partner/scalr.com"
}],
"detail-type": ["AuditLogDisabled"]
}Demo
Updated 24 days ago
