Azure Provider Configuration
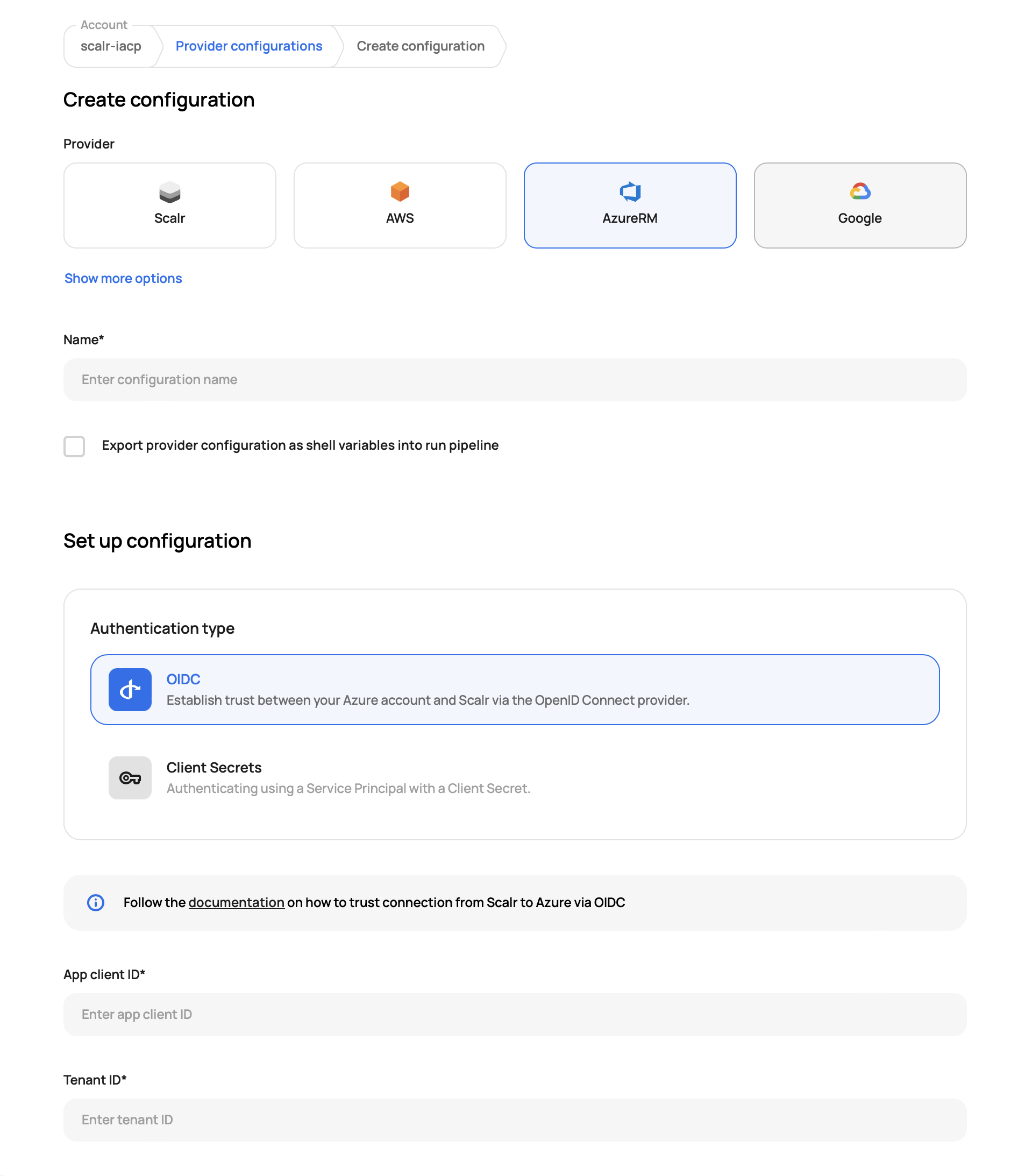
The AzureRM provider configuration supports two methods to authorize the Terraform and OpenTofu provider in the run pipeline: OIDC and Client secrets. The OIDC method allows you to use temporary tokens generated before each run phase (plan & apply), while the Client secrets - static principal credentials.
OIDC
Azure steps
First, you need to create a new Azure AD application and give it the role assignments required by workspaces in the environment(s). Alternatively, you can use an existing application. Once you have the application created, complete the following steps:
- Open the application in the Azure AD and select the "Certificates & Secrets" menu item.
- Select the "Federated credentials" tab and click the "Add credential" button.
- In the creation form, select the "Other issuer" option of the "Federated credential scenario" dropdown.
- Enter the "Issuer". It should match the exact value https://scalr.io.
- Enter the "Subject" which must match the following format:
account:<account-name>:environment:<env-name>, e.g.account:my-corp:environment:team-a-production. Unfortunately, the subject doesn't support wildcards*, so for each environment in Scalr, you need to create its own federated credential. - Enter the "Name" of the credential, e.g.
scalr-io-team-a-production. - Enter the "Audience", e.g.
team-a-production. - Save the Federated credential.
Scalr steps
To complete the creation of the OIDC AzureRM provider configuration, you need to enter:
- App client ID - the
Application (client) IDof the Azure AD application. - Tenant ID - the
Directory (tenant) IDof the Azure AD application. - Subscription ID - The id of the subscription (can be found here
- Audience - has to match the audience from the Azure steps, e.g.
team-a-production. - Save and share it with the environments for which you have created federated credentials.
IMPORTANT: before sharing the existing provider configuration with a new environment, you have to create a federated credential first, and its subject must match the following pattern: account:<account-name>:environment:<env-name>, e.g. account:my-corp:environment:team-b-production.
For the sake of simplicity, Scalr doesn't pass the workspace id as a part of the subject, because otherwise, you would need to create a federated credential for each workspace before linking it. Also, keep in mind that Azure allows the creation of only 20 federated credentials per single application.
Scalr provider example
resource "scalr_environment" "a_prod" {
name = "team-a-production"
}
resource "scalr_provider_configuration" "azurerm_oidc" {
name = "azurerm-oidc-example"
environments = [scalr_environment.a_prod.id]
azurerm {
auth_type = "oidc"
client_id = "111aaabb-cccc-2222-dddd-1234adcd0000"
subscription_id = "222bbbcc-dddd-3333-eeee-2345bcde0123"
tenant_id = "333cdbde-ef01-4567-ef98-3455cdef9876"
audience = "team-a-production"
}
}Client Secrets
Azure steps
For Azure, a service principal is required which can be created by following the steps in the provider documentation.
- Azurerm Creating a Service Principal
- In the "Add Credentials" dialogue select Azure
- Enter the Client ID (appId), Secret Key (password), and Tenant ID
(tenant) from the output ofcreate-for-rbac. Click Save
Example output from create-for-rbac
{
"appId": "c5f583b2-xxxx-xxxx-xxxx-baa93d369f1b",
"displayName": "azure-cli-2020-04-21-07-39-09",
"name": "http://azure-cli-2020-04-21-07-39-09",
"password": "2458ffd6-xxxx-xxxx-xxxx-3b9f3964ab67",
"tenant": "8ad9e98e-xxxx-xxxx-xxxx-7969b23753d4"
}Scalr steps
To complete the creation of the Client Secrets AzureRM provider configuration, you need to enter:
- App client ID - the
appIdfrom the snippet above. - App secret key - the
passwordfrom the example above. - Tenant ID - the
tenantfrom the example above. - Subscription ID - The id of the subscription (can be found here
Provider example
resource "scalr_environment" "a_prod" {
name = "team-a-production"
}
resource "scalr_provider_configuration" "azurerm" {
name = "azurerm"
account_id = "acc-xxxxxxxxx"
environments = [scalr_environment.a_prod.id]
azurerm {
client_id = "my-client-id"
client_secret = "my-client-secret"
subscription_id = "my-subscription-id"
tenant_id = "my-tenant-id"
}
}The above is an example, follow the full provider documentation here.
The provider configuration will auto populate the majority of the information in the Azure provider block, but you will continue to have to add thefeatures {}block even if it is empty. Scalr does not add this to ensure any existing configuration does not break.
Review the full provider configuration documents on how to link the provider configuration to an environment and workspace here
Azure CLI Errors
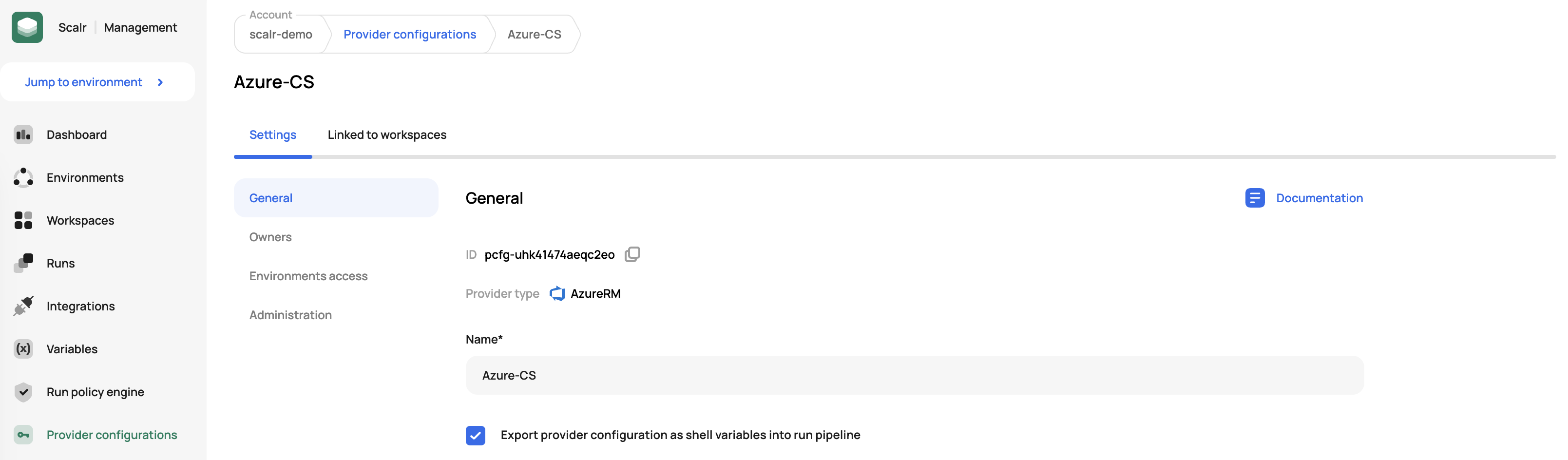
If you are receiving the following error code, it means that you are likely not exporting the provider configuration as a shell variable:
could not configure AzureCli Authorizer: obtaining tenant ID: running Azure CLI: exit status 1: ERROR: Please run 'az
login' to setup account.To fix this, click the "Export provider configurations as shell variables into the run pipeline" checkbox in the provider configuration that is associated with the environment and workspace:
AzureAD Provider
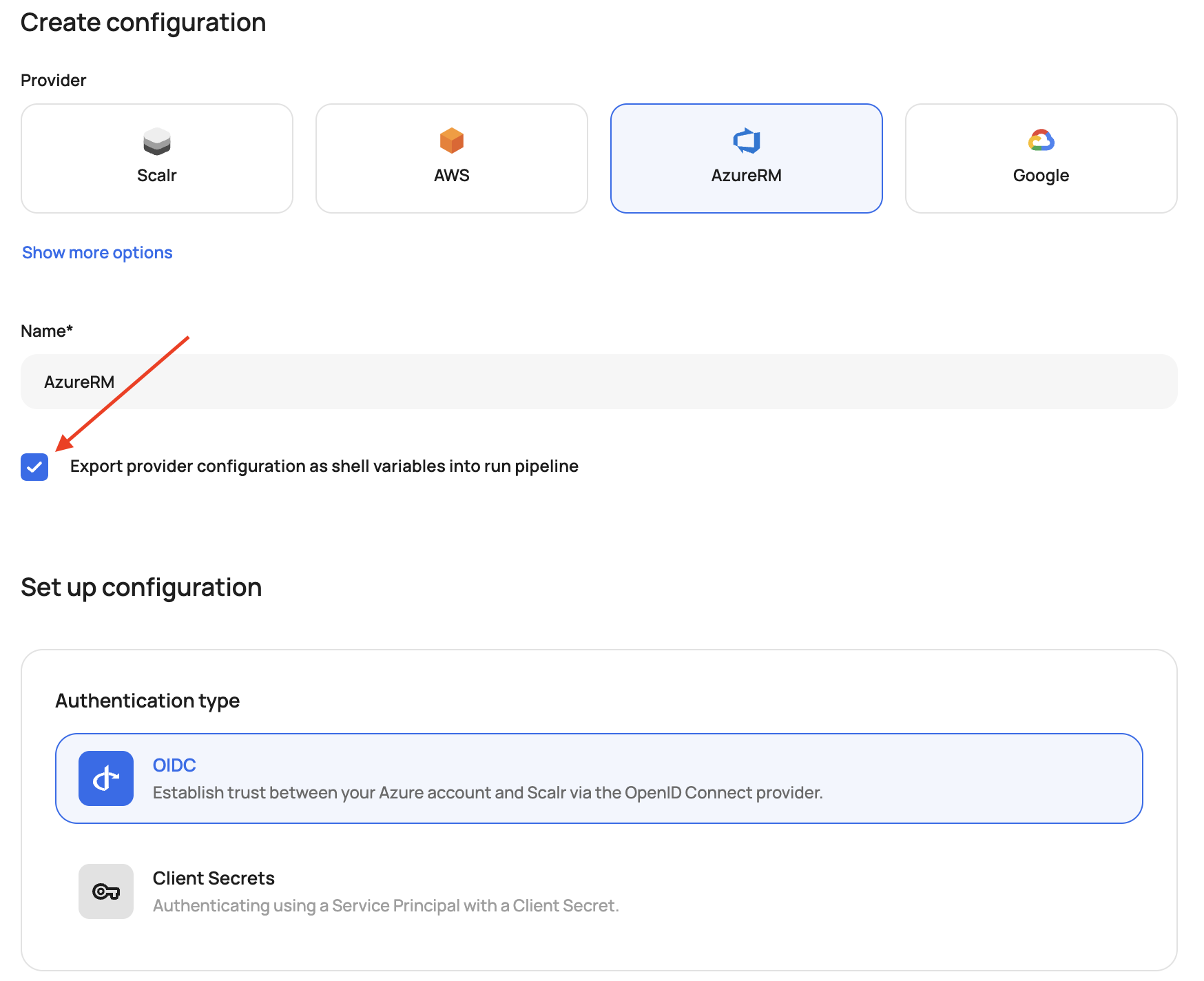
The AzureRM provider configuration can also be used for the AzureAD provider configuration if the "Export provider configurations as shell variables into the run pipeline" option is checked:
Updated 7 months ago
