GitHub
Github.com
Integrating with a VCS provider unlocks the ability to use GitOps workflows, import modules, enable Open Policy Agent, and much more.
The GitHub VCS Provider is authenticated by using the GitHub App feature. To enable the integration, go to "Integrations" and select GitHub. Enter the provider name prompted for and follow the flow:
Select the GitHub organization:

Then select the repositories that Scalr will need access to:
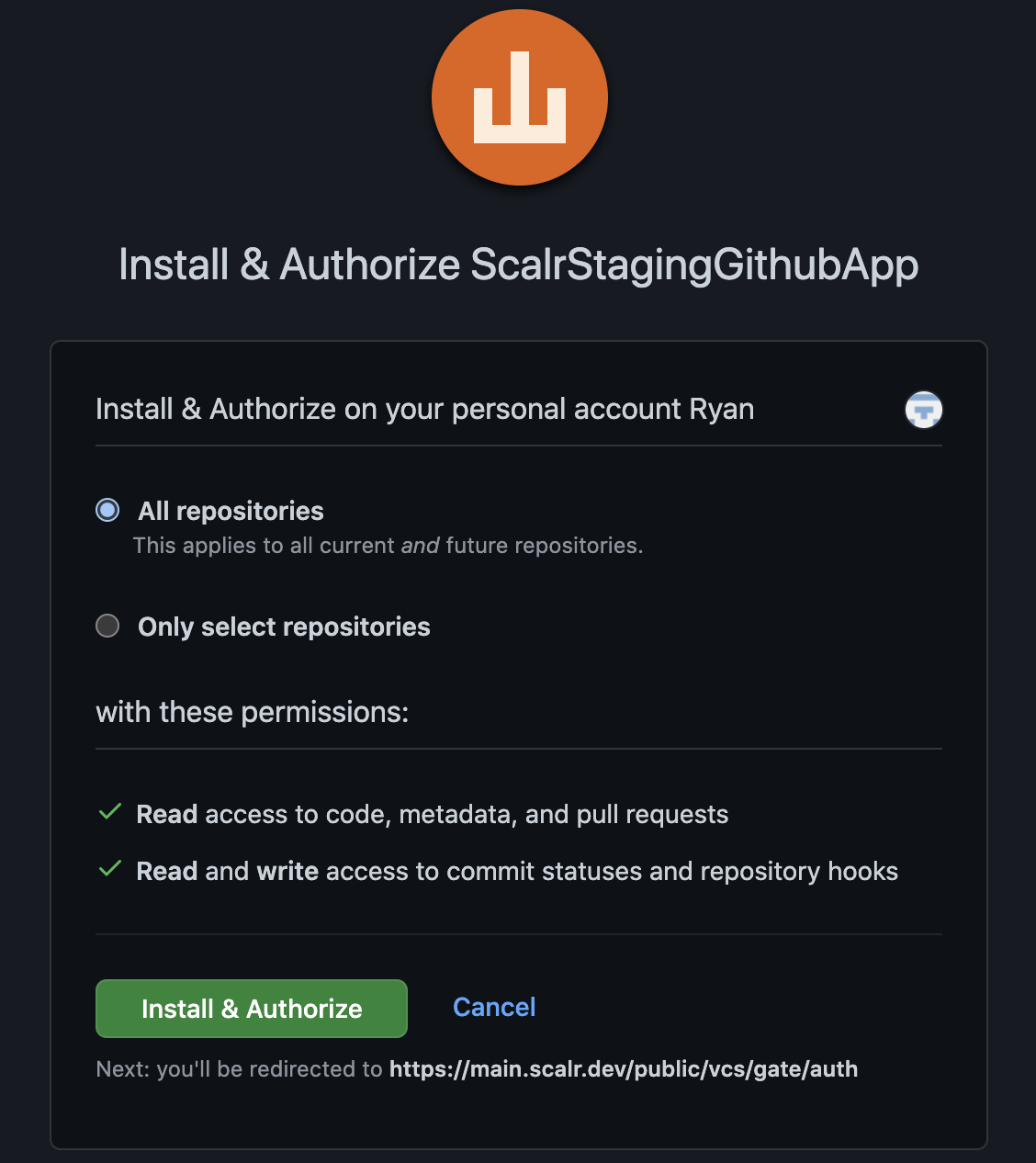
After clicking Install and Authorize, you will be redirected back to Scalr.
Github Enterprise
GitHub Enterprise is a GitHub instance that is installed within your own network. If you are using GitHub.com, please follow the instructions above.
To enable GitHub Enterprise:
- Go to “Integrations” and select GitHub
- Copy the callback URL
- Enter your GitHub Enterprise URL
- Click the “Register a new OAuth application” link, and register a new OAuth app in GitHub.
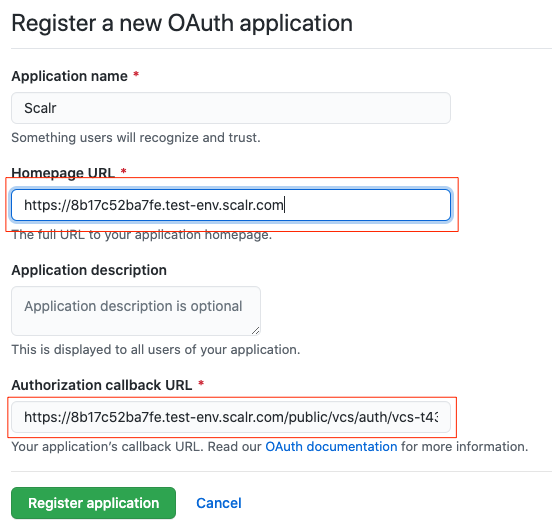
- Click on “Generate a new client secret" and copy the client ID and client secret:
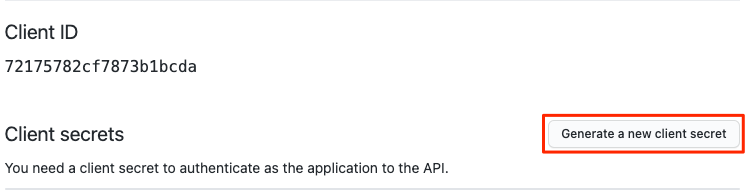
- Go back to Scalr and paste the values into the fields:
- Client ID
- Client Secret
- Upon clicking “Create” a redirection back to GitHub occurs to complete the authorization.
Pull Request Comments vs Checks
Scalr gives two options for displaying run results in the GitHub pull request, both of which can be used simultaneously:
Comments
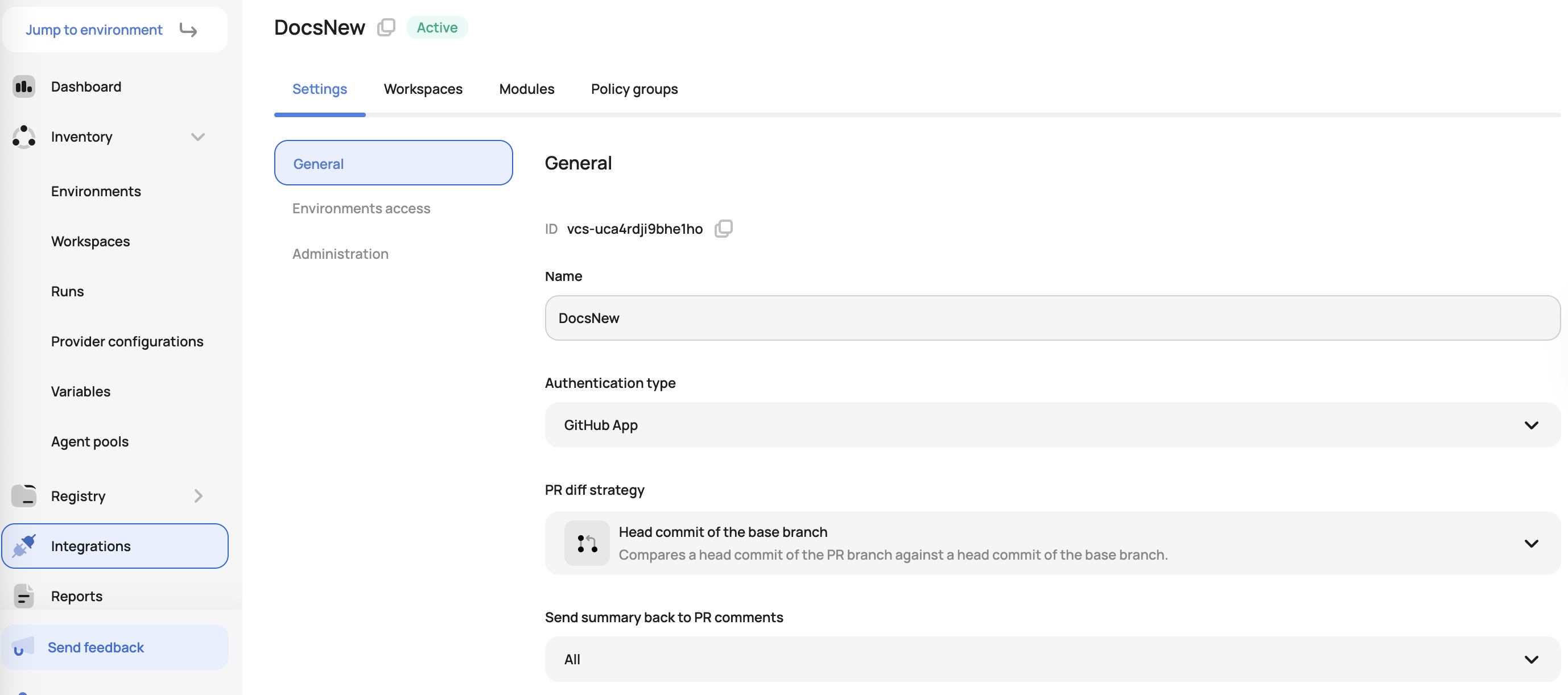
Pull request comments: The result will be an overall summary of the pull request as well as a per-workspace report showing what resources have been created, updated, or deleted. The cost and OPA results will also be displayed:
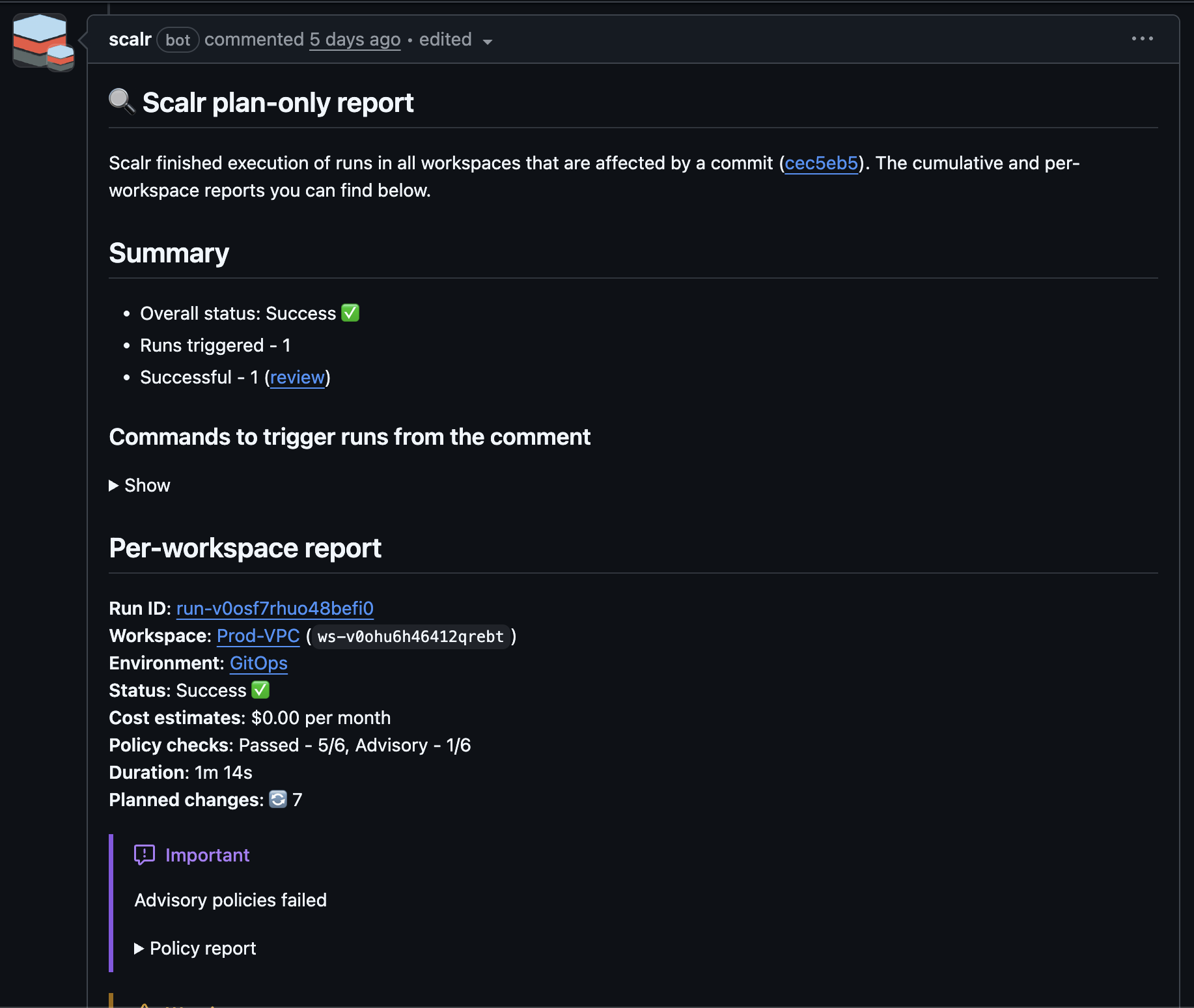
To be able to see the run summary in a GitHub comment before merging the PR, you must enable this in the GitHub integration at the account scope:
Execute Runs from Pull Request Comments
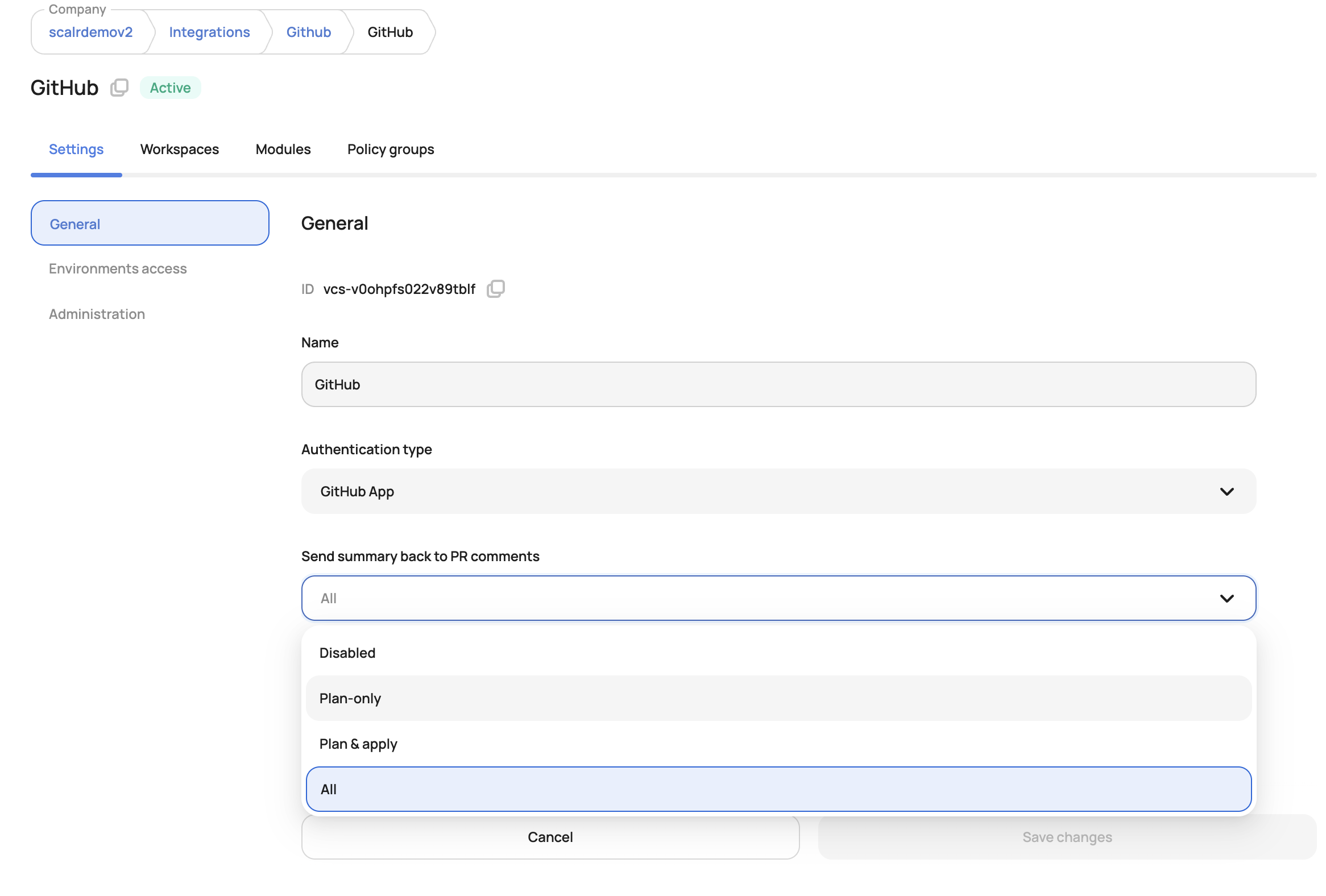
To enable the ability to execute runs from pull request comments, you must enable it at the VCS provider integration level:
- Allow triggering plan-only runs from the PR comments: Any user who can comment on the PR can execute a
plan-onlyrun in Scalr. - Allow triggering plan & apply runs from the PR comments: Any user who can comment on the PR can execute an
applyrun in Scalr.
When enabled, all users who have access to the pull request comment can execute a run. The workspace must have "Enabled VCS-driven dry runs" enabled in the settings for this feature to work.
Run Approvals from Pull Request Comments
Runs that are waiting for approval can be approved directly from pull request comments.
For a user to be able to approve or decline a run, the following must apply:
- Users must have the same email address in both GitHub and Scalr.
- Users must have the runs:apply permission otherwise, the approve or decline commands will not be permitted.
Checks
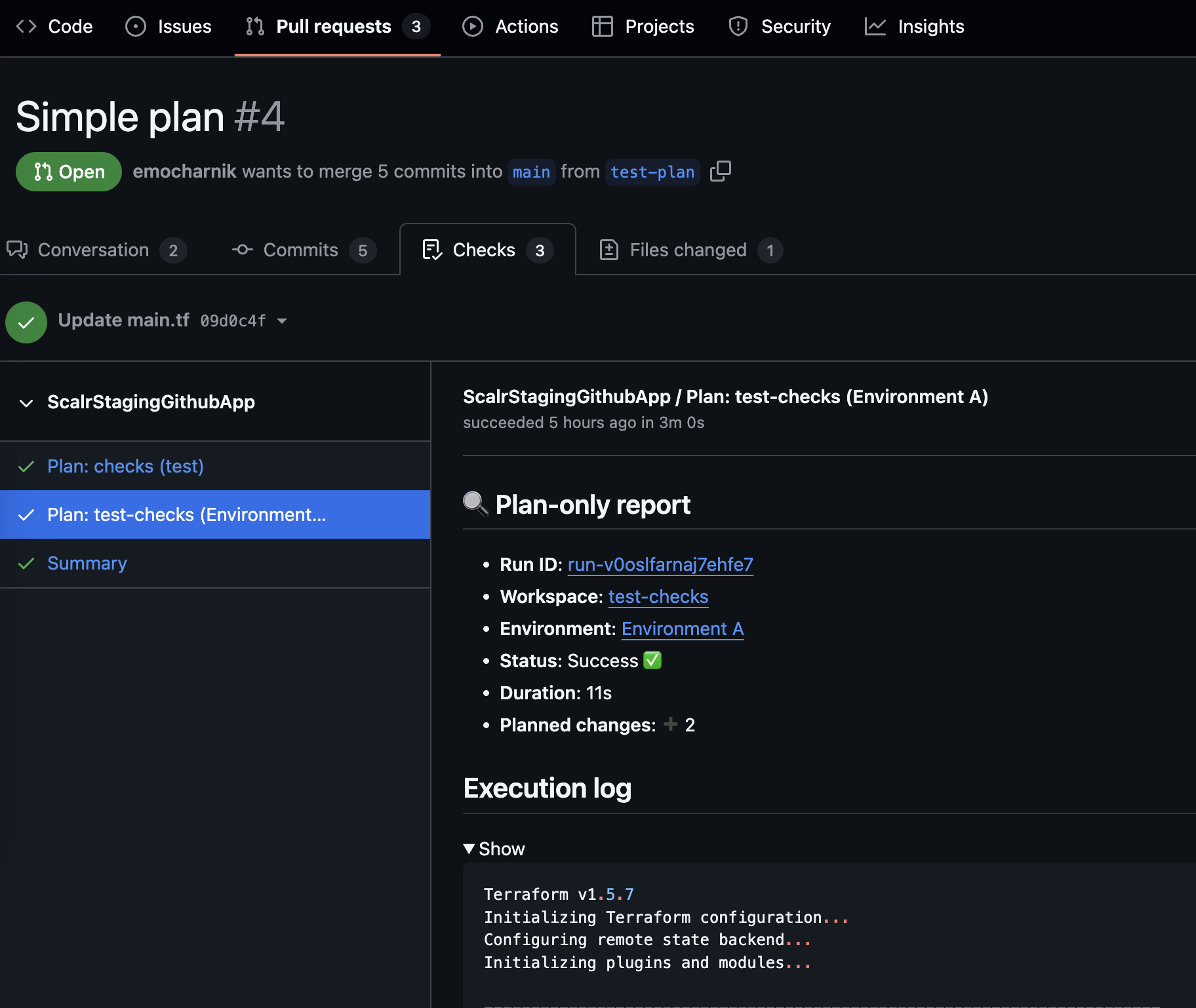
Pull request checks: The result will be the output of the plan and apply run logs posted as a check with a general summary. All runs triggered by the commit will have the output displayed.:
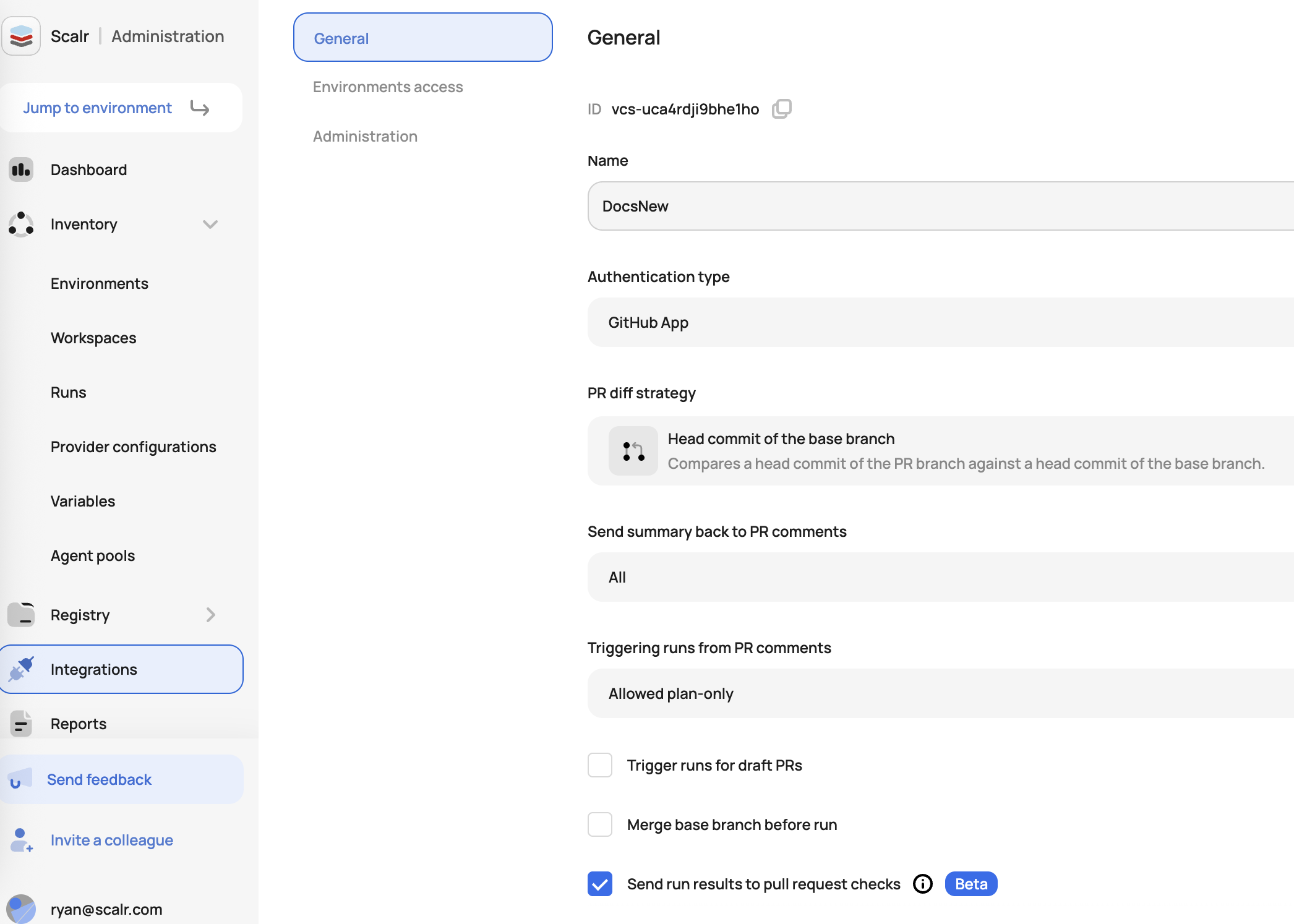
To be able to see the run results in a GitHub check before merging the PR, you must enable this in the GitHub integration at the account scope by checking "Send run results to pull request checks":
Execute Runs from Checks
To enable the ability to execute runs from checks, you must enable it at the VCS provider integration level:
- Allow triggering plan-only runs from the check: Any user who can comment on the PR can execute a
plan-onlyrun in Scalr. The workspace must have "Enabled VCS-driven dry runs" enabled in the settings for this feature to work. - Allow triggering plan & apply runs from the check: Any user who can comment on the PR can execute an
applyrun in Scalr, if the user email in Github matches the user in Scalr.

Run Approvals from Pull Request Checks
Runs that are waiting for approval can be approved directly from pull request checks.
For a user to be able to approve or decline a run, the following must apply:
- Users must have the same email address in both GitHub and Scalr.
- Users must have the
runs:applypermission otherwise, the approve or decline commands will not be permitted.
Draft PRs
Draft pull requests are commonly used during the early development cycles to note when a pull request is in a draft state. Since draft pull requests are so early on in the development cycle, it's possible that you don't want a Scalr plan to execute when pull requests are opened. Scalr gives you the option to ignore draft pull requests by unchecking "Trigger runs for draft pull requests". As of right now, this will apply to any workspace that is linked to the VCS provider.
Automatic Base Branch Merge Before Run Execution
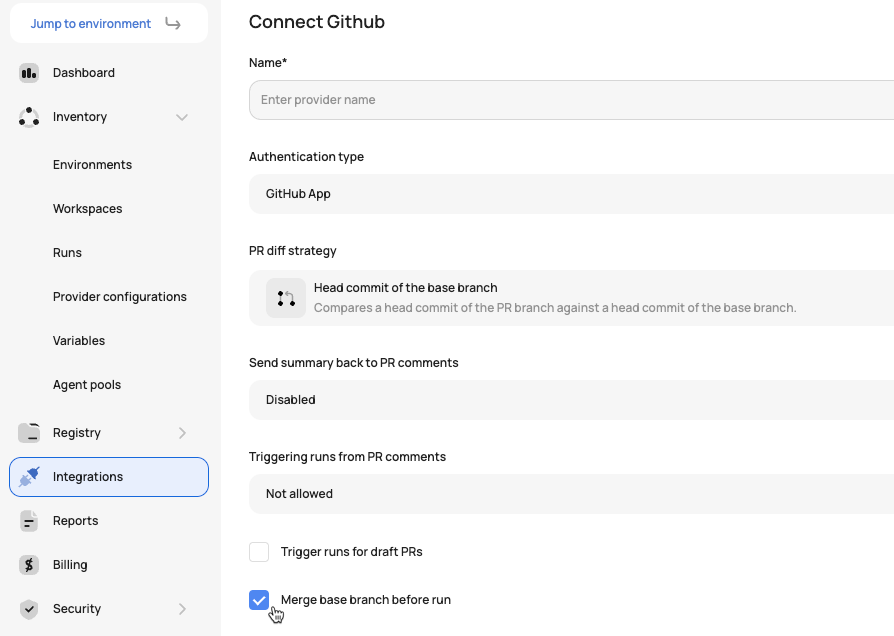
VCS-driven workspaces can automatically merge the base branch into the head branch before triggering a run. This ensures that runs are always executed against the latest code in the base branch, providing more accurate and reliable results. This helps a common pain point where runs could be executed against outdated head branches, potentially leading to false-positive results or failed applies after merging.
To implement this feature, enable the auto-merge option when configuring the VCS provider:
Github Actions
Scalr has a supported Github action that can be found here. The action uses the Terraform and Scalr CLI to kickoff Terraform workflows with Scalr set as the remote backend where the run is executed and state is stored.
Secret Scanning
Scalr supports the ability to do Github Secret Scanning to ensure Scalr API tokens do not end up visible in code stored in Github. To enable this, go to your GitHub settings, specifically Code Security and then Global Settings. In there, click Scan for non-provider patterns and under Custom patterns, select New Pattern:
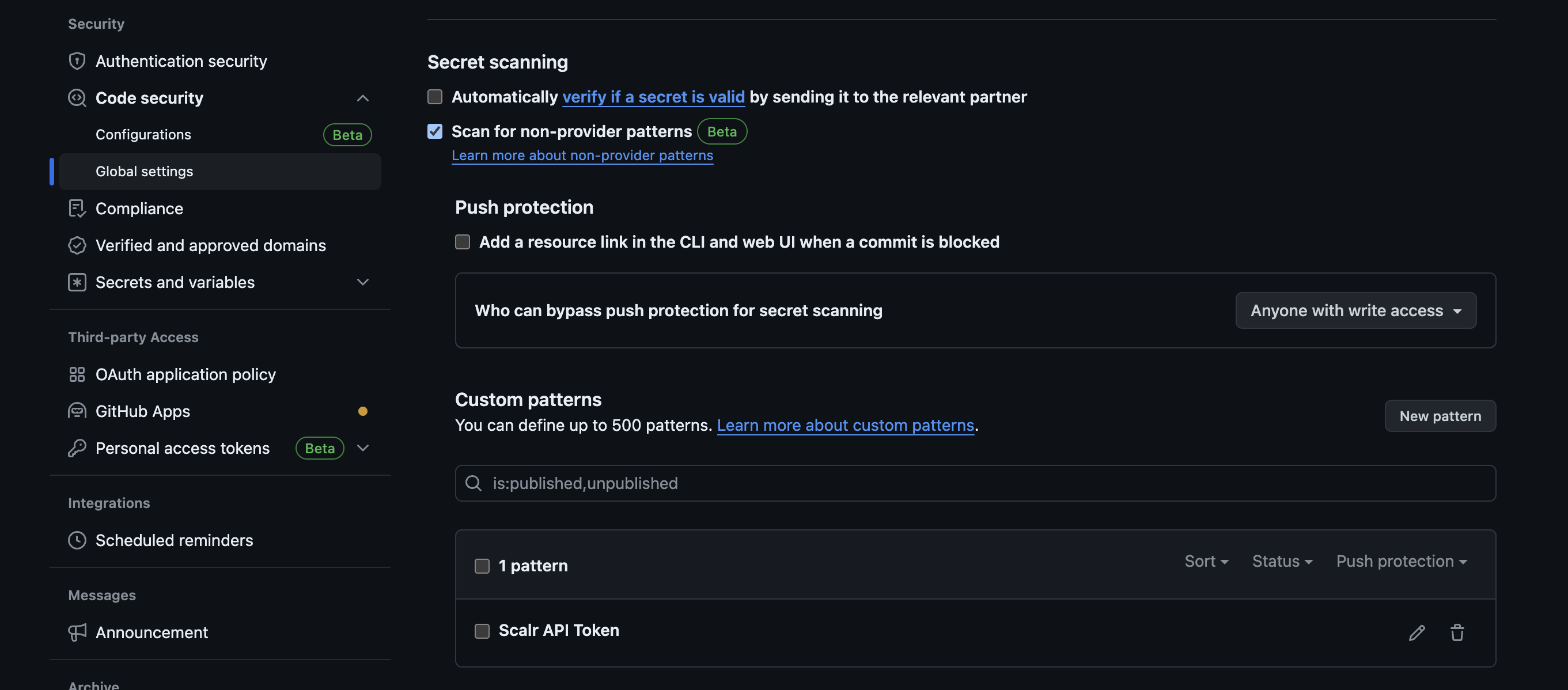
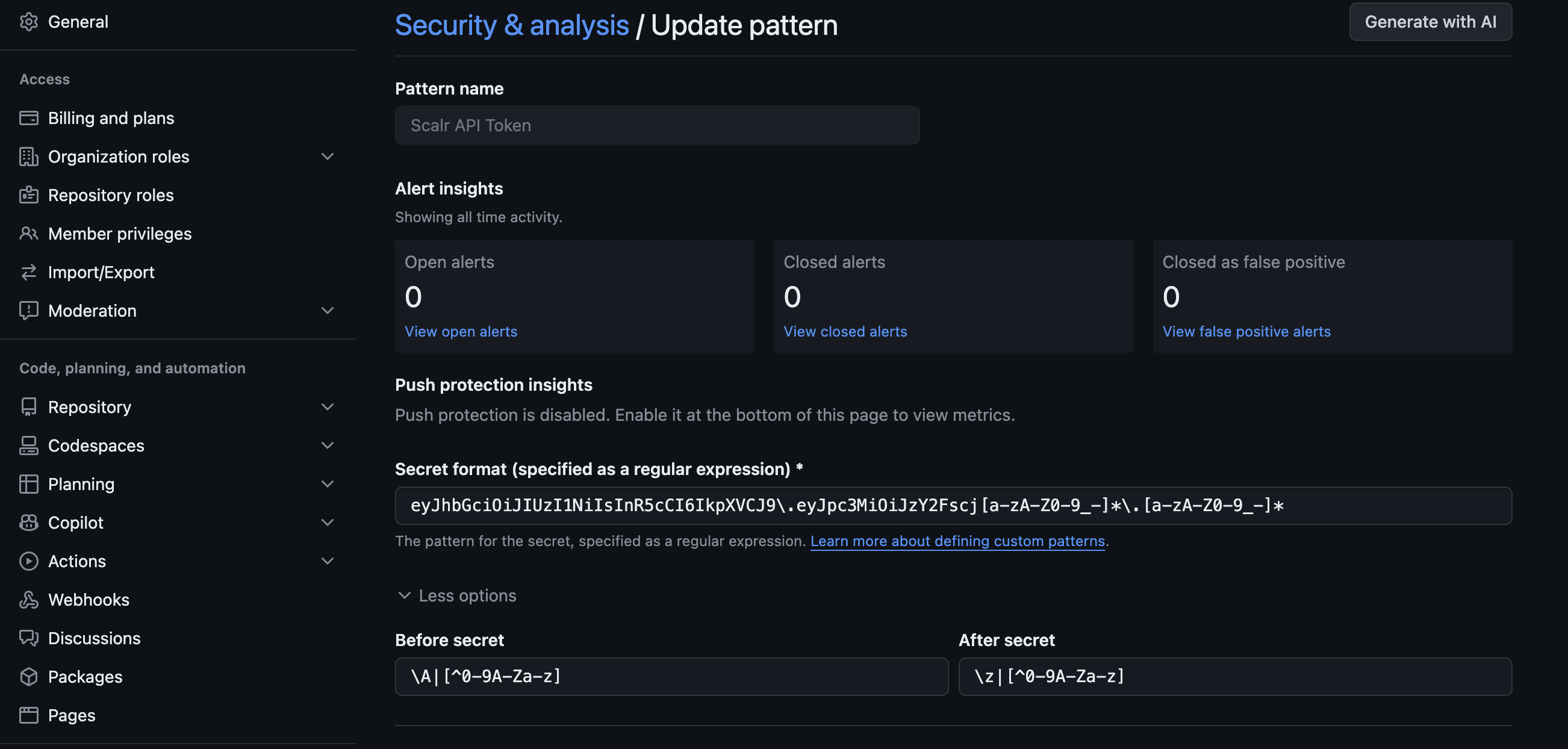
Once you are on the new pattern page, enter the following:
Secret Format: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9\.eyJpc3MiOiJzY2Fscj[a-zA-Z0-9_-]_\.[a-zA-Z0-9_-]_
Before Secret: \A|[^0-9A-Za-z]
After Secret: \z|[^0-9A-Za-z]
Upon saving the information above the secret scanning will be enabled and you will be notified if any Scalr API tokens make it into your code stored in GitHub.
The token must have been created on or after April, 11th 2024 for the secret scanning to work correctly.
Note: Scalr is currently awaiting approval from GitHub to join the secret scanning partner program.
Updated about 1 month ago
