Microsoft Entra
NoteScalr supports all SAML 2.0 providers; this is just an example of a commonly used one.
Overview
Go to Microsoft Entra ID, click on Enterprise applications, then Create your own Application:

Name the application and select “Integrate any other application you don’t find in the gallery”:
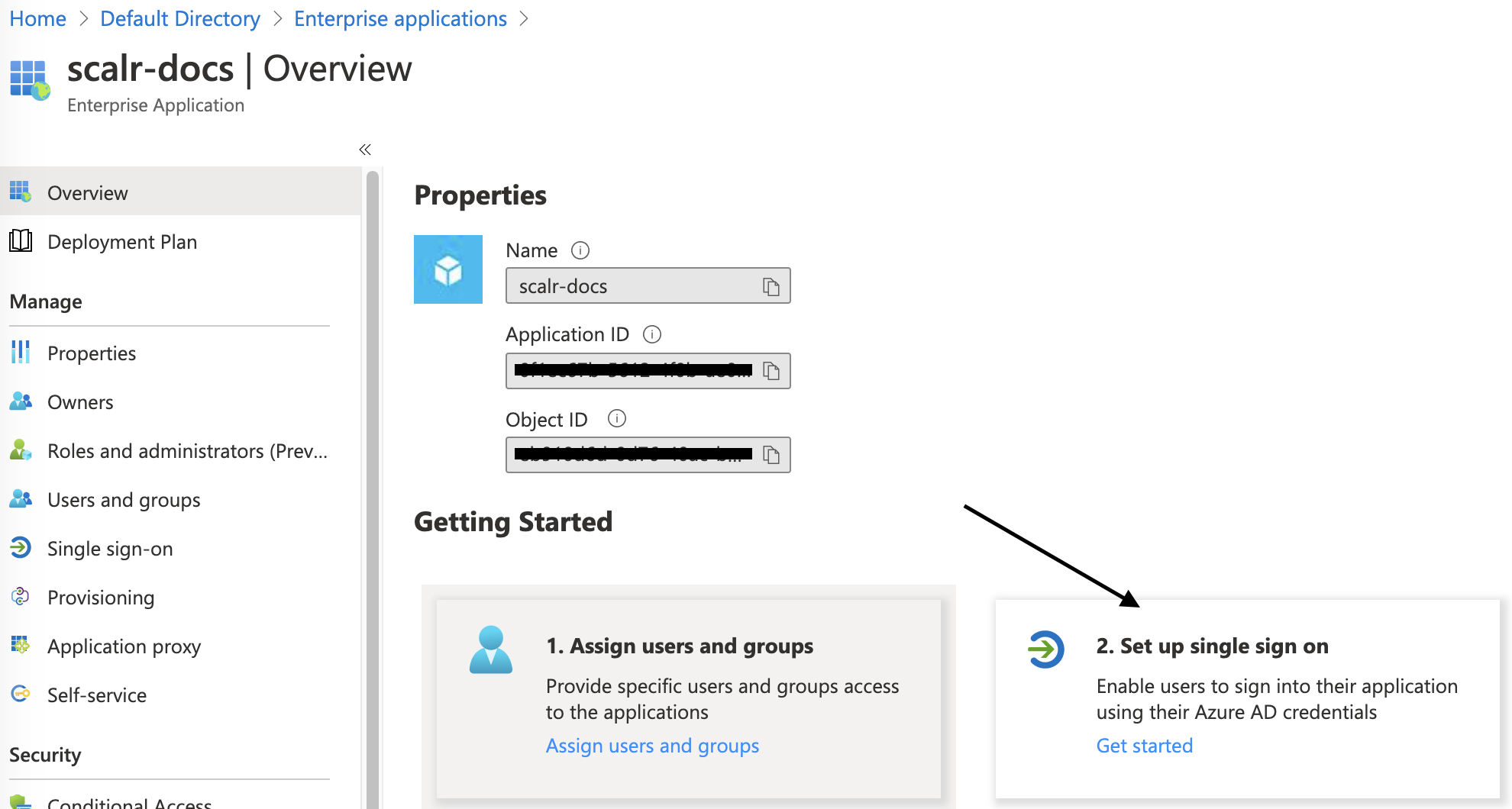
Select “Set up single sign-on”:
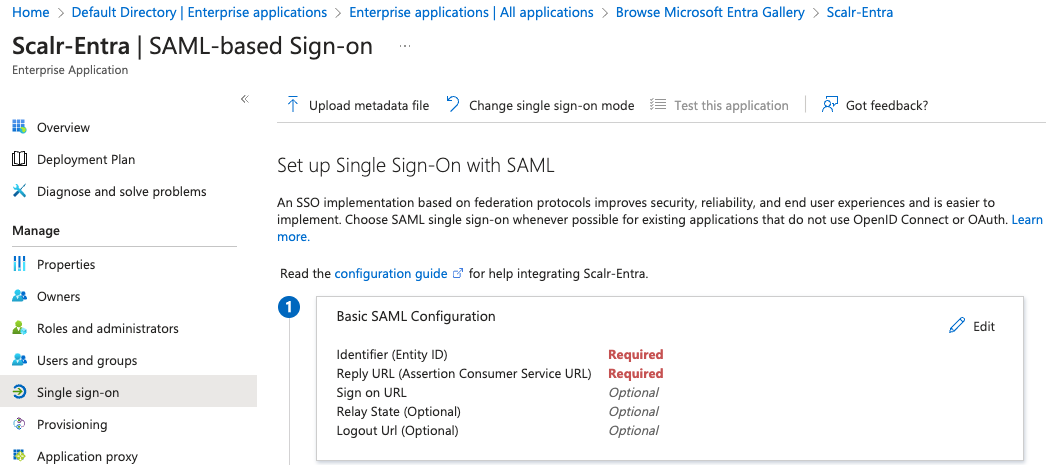
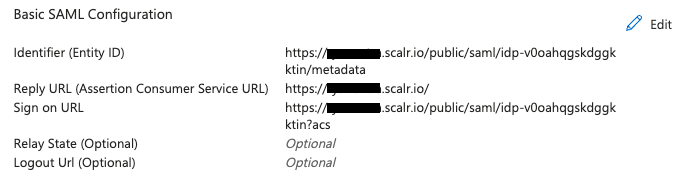
Select the SAML option and click edit on the "Basic SAML Configuration" option.:
You'll now need to log into Scalr to gather some information. Go to the Scalr account scope, click on integrations, and then click "Connect" on the SAML integration:
In there, you will find the SP endpoint, Sign on URL, and Reply URL, which are need in Azure. Enter the following information into Azure:
| Azure Field | Corresponding Scalr Field |
|---|---|
| Identifier (Entity ID) | SP Endpoint |
| Reply URL (Assertion Consumer Service URL) | FQDN of the Scalr endpoint |
| Sign on URL | Single sign on URL |
Click save. You should now have something similar to the screenshot below:
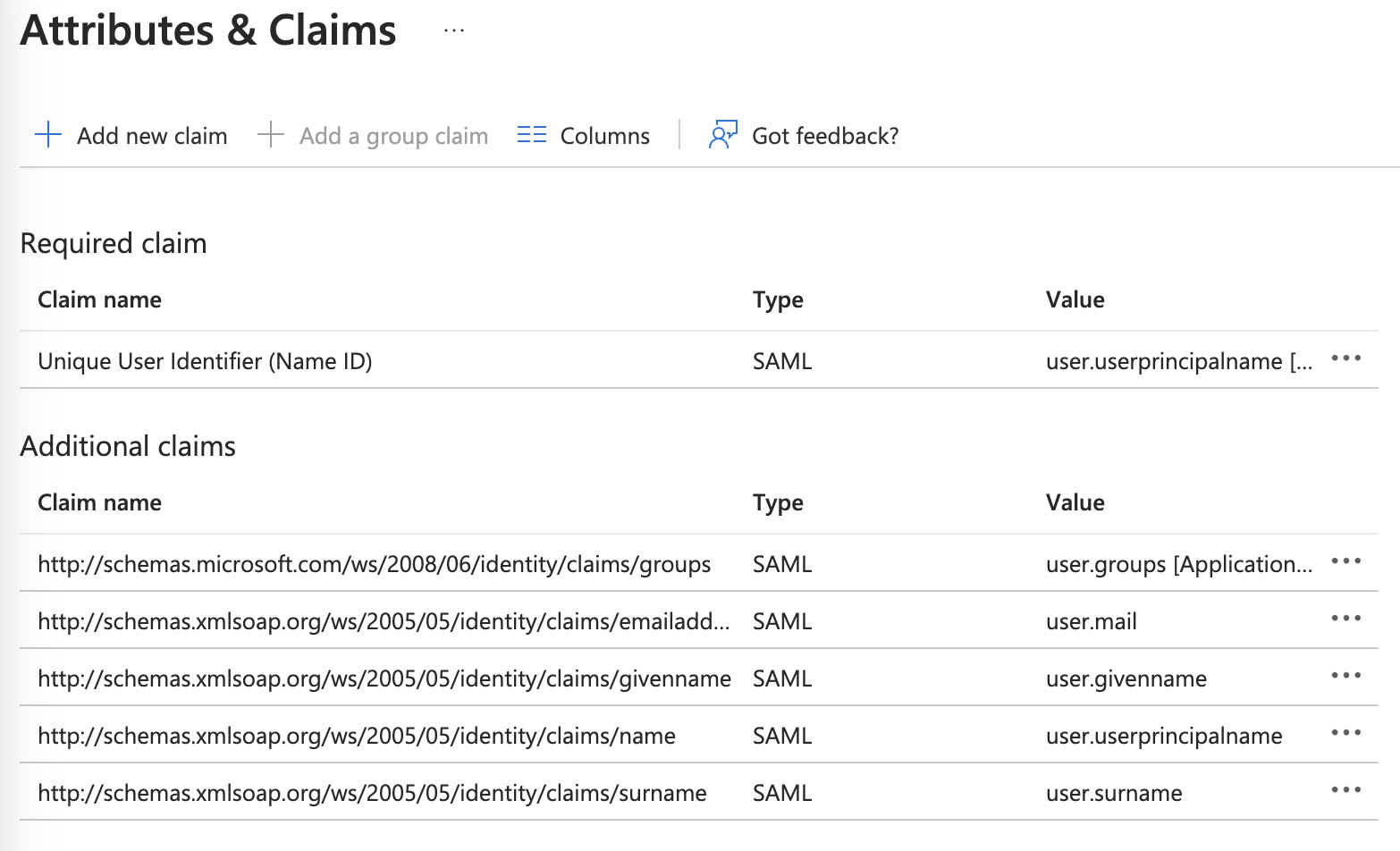
Open the Attributes & Claims, click add a group claim, select “Groups assigned to this application”, select "cloud-only group display names" as the source attribute, and save. The values should be similar to the below:
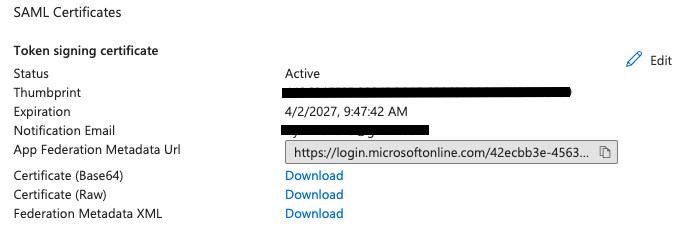
Back on the "SAML-based Sign-on" page in Azure, go to the SAML Certificate section and download the Certificate (Base64). Flip back to Scalr. If you haven't given a name to the SAML connection in Scalr yet, do that now. Next, click on the "manual" configuration method in Scalr.
Now paste the certificate into the IDP x509cert section in Scalr:
Azure:
Scalr:
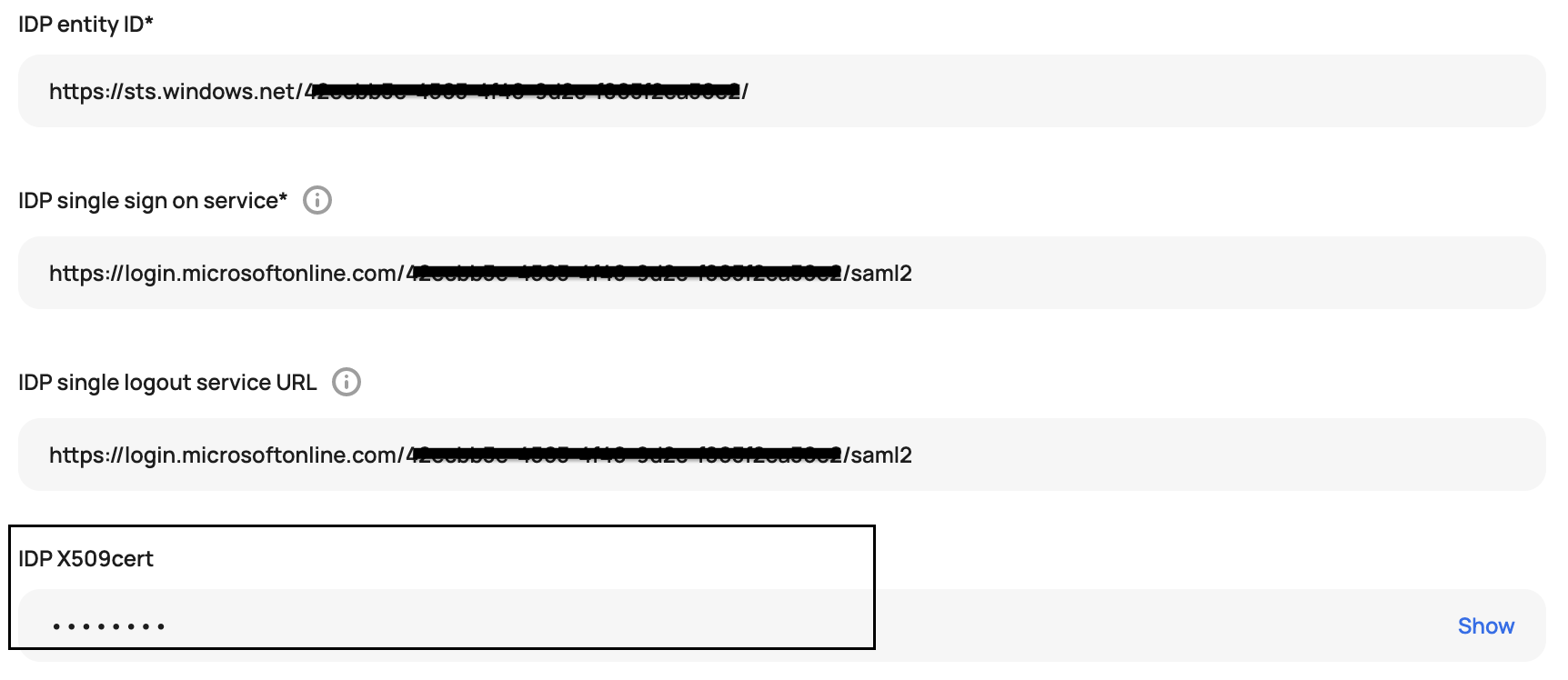
Back on the "SAML-based Sign-on" page in Azure, go to the Set up section. Copy the following values from Azure and paste in the corresponding field in Scalr:
| Azure | Scalr |
|---|---|
| Login URL | IDP single sign-on service |
| Microsoft Entra Identifier | IDP entity ID in Scalr |
| Logout URL | IDP single logout service URL |
Azure:
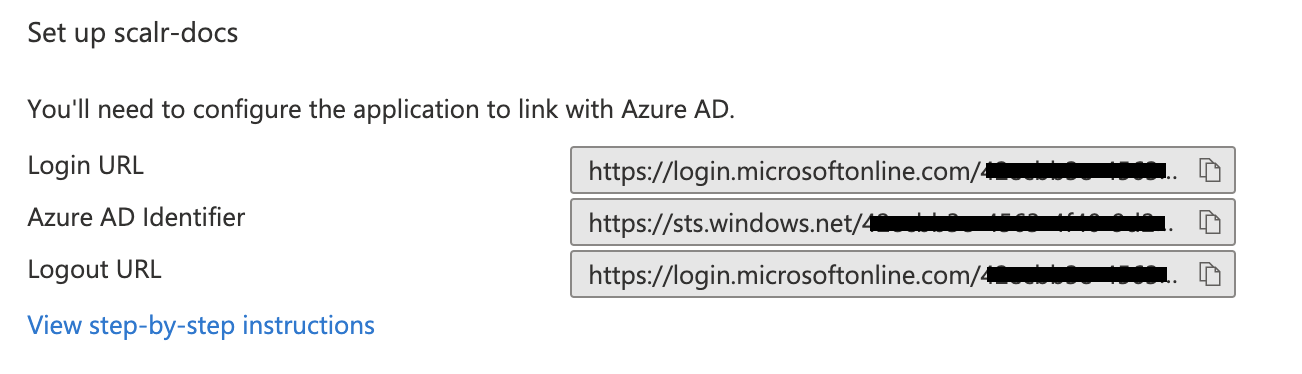
Scalr:

NoteThe "Use Azure Active Directory" option no longer needs to be checked in Scalr.
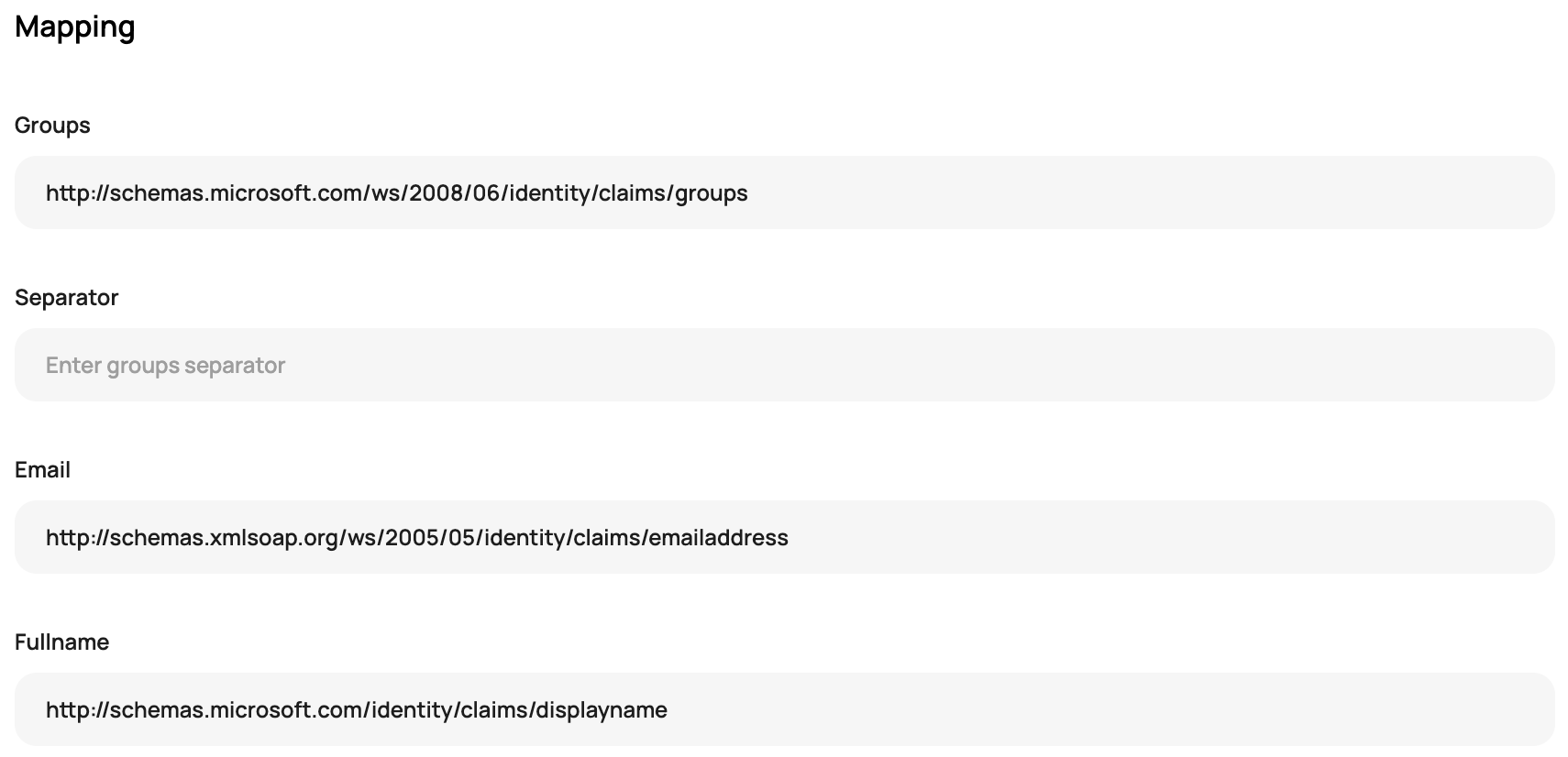
While in Scalr, finish off the Scalr set up by going to the mapping section and adding the following:
- Groups = http://schemas.microsoft.com/ws/2008/06/identity/claims/groups
- Email = http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
- Fullname = http://schemas.microsoft.com/identity/claims/displayname
You Scalr mapping section should looks the same as the following:
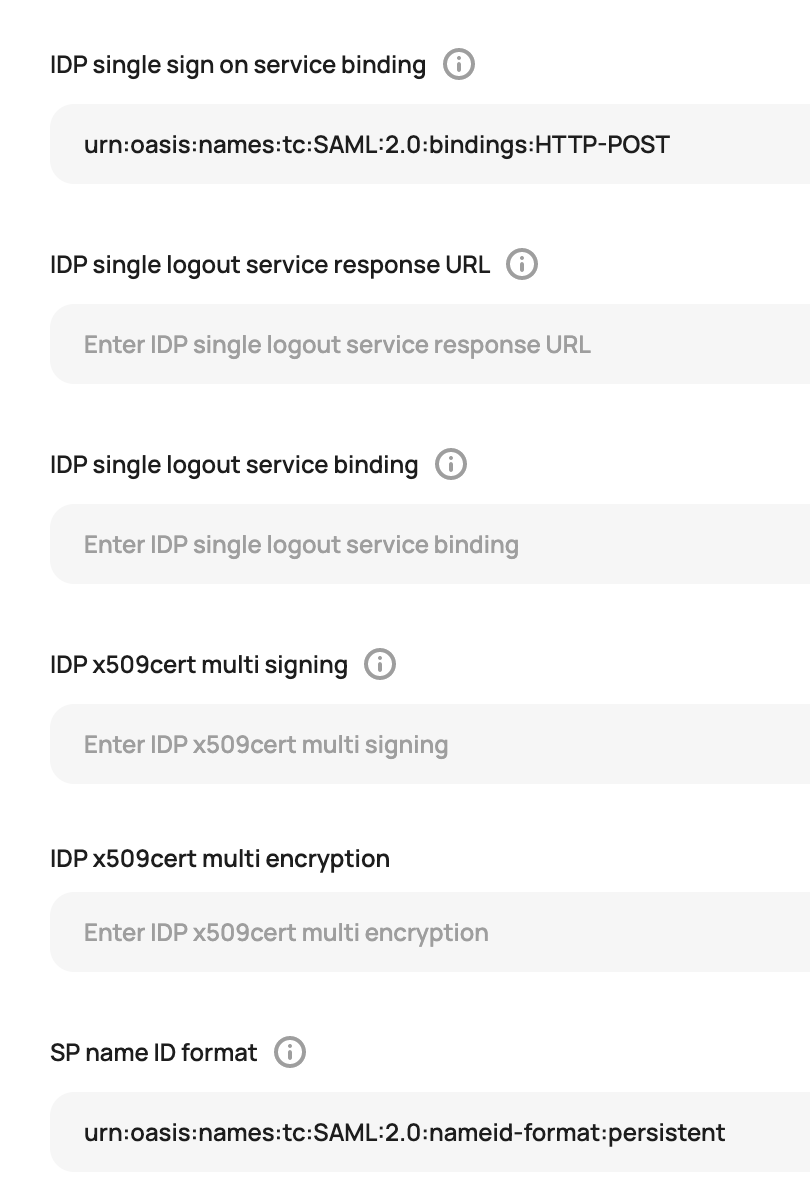
Still in Scalr, click on the advanced section and update the following fields:
- IDP single sign on service binding = urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST
- SP name id format = urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
Finally, in Azure, you'll now need to go to the "App registrations" page, which can be found by clicking on "permissions" and then "app registration":
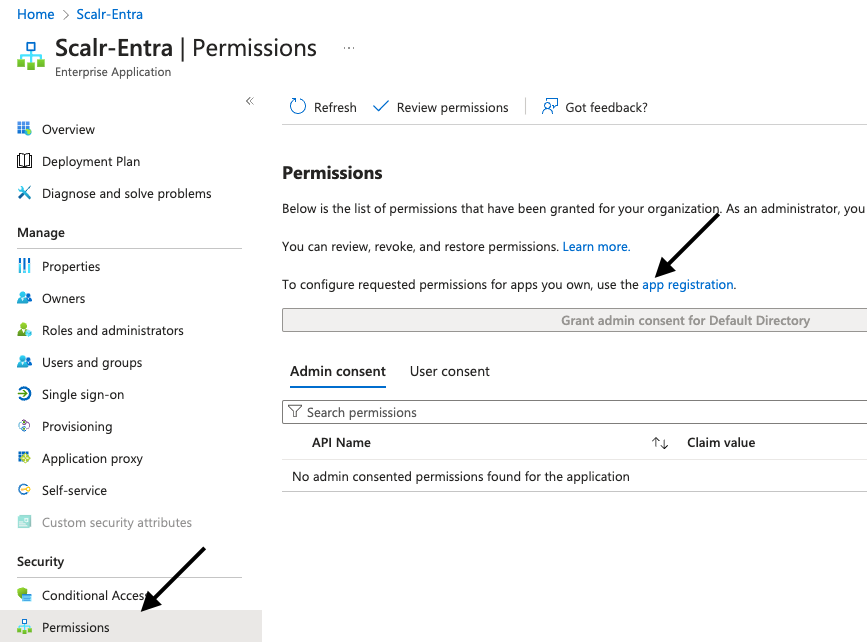
Click "Add a permission", select "Microsoft Graph", then "Application permissions", and add "Directory.Read.All". Ensure that “admin consent” is set to yes and the permission type is “application”.
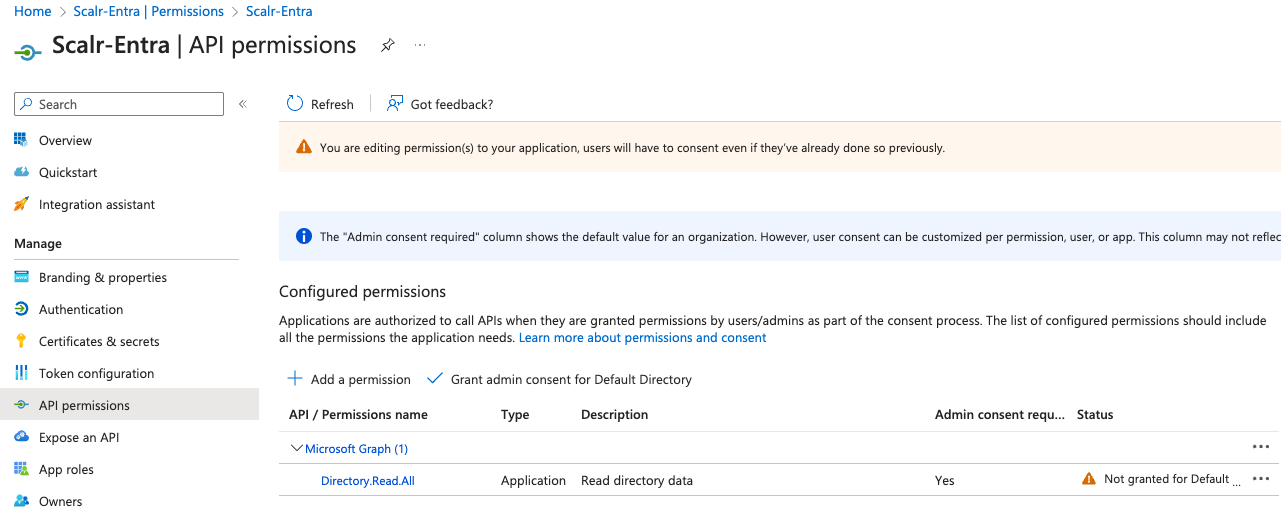
In Azure, you'll want to verify the permission has been given consent, which can be verified by going back to the Entra Enterprise Applications page, finding your application, then clicking permissions and granting:
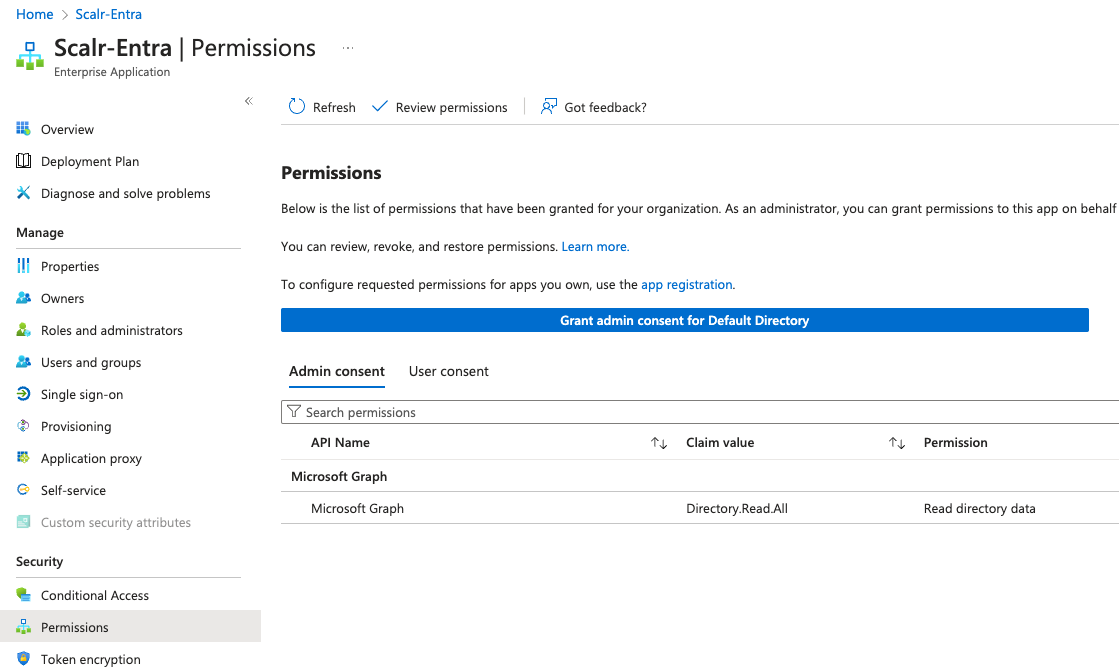
In Scalr, click Connect SAML IDP and then verify the connection on the main SAML page in Scalr.
Azure SCIM
Note: This is included in the enterprise plan. Contact support if you have any questions.
Scalr supports the SCIM (System for Cross-domain Identity Management) protocol to automatically add and remove users from Scalr.
To enable the SCIM protocol for Azure AD, go to the Azure application that you already provisioned above and follow the steps below:
Go to Provisioning, click Get Started:
- Select Automatic for Provisioning mode
- For Tenant URL insert SCIM server URL (
https://<account>.scalr.io/scim/v2) - For Secret Token insert the SCIM auth token, which can be obtained in Scalr in the SCIM Protocol section of the SSO settings page.
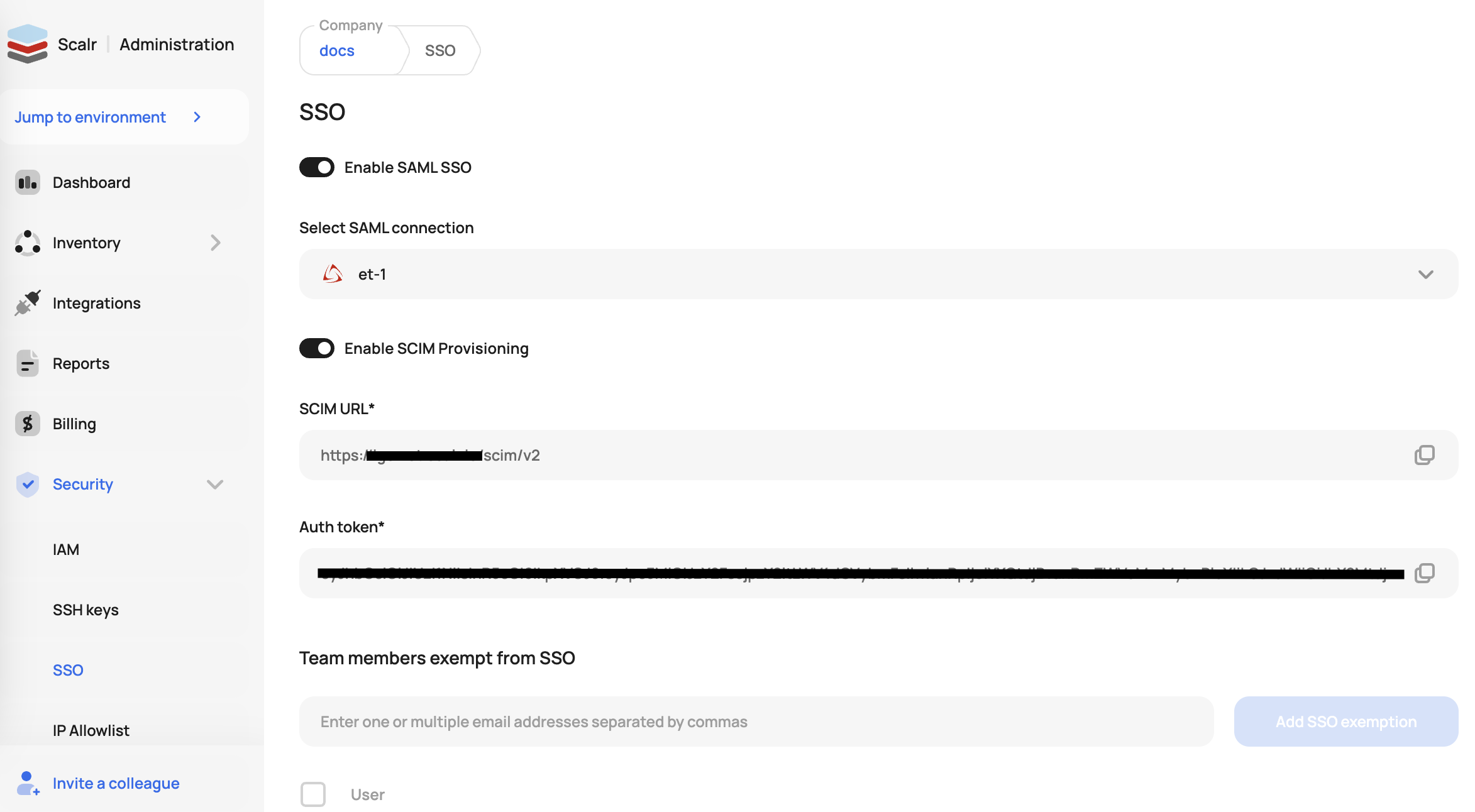
- In Azure, verify the connection by clicking Test Connection
- Click Save
- In Azure, configure the following Attribute Mappings for Provision Azure Active Directory Users in Mappings section:
userPrincipalName->userName(Matching precedence 1)Switch([IsSoftDeleted], , "False", "True", "True", "False")->activegivenName->name.givenNamesurname->name.familyNameobjectId->externalId
- Configure the following Attribute Mappings for Provision Azure Active Directory Groups in Mappings section:
displayName->displayName(Matching precedence 1)members->members
Passwordless Auth
If your organization uses passwordless auth with Entra, update the file Requested authn context to false in Scalr. If users attempt to log in without this updated the following error will occur:
“AADSTS75011: Authentication method 'MultiFactor, PasswordlessPhoneSignIn' by which the user authenticated with the service doesn't match requested authentication method 'Password, ProtectedTransport.“
Updated 18 days ago
