Single Sign-On (SSO)
General Configuration
Scalr supports SSO providers that use SAML 2.0. When SSO is activated, it will move the authentication step outside of Scalr and hand it over to the SSO provider that you have configured. During the login to Scalr, the user will be transferred to a sign-in page provided by the SSO server. After signing in, the user will then be redirected back to Scalr which will subsequently treat the user as signed in.
To enable SSO, go to the integration tab at the account scope and click on SAML IDP. You will then be given information that will be needed in your SSO provider:
Go to your SSO provider and start the configuration (see below for examples). The Scalr setup can be finished upon completion of the SSO provider configuration.
Upload the metadata file or manually fill in the fields required by your SSO provider and verify the connection when prompted:
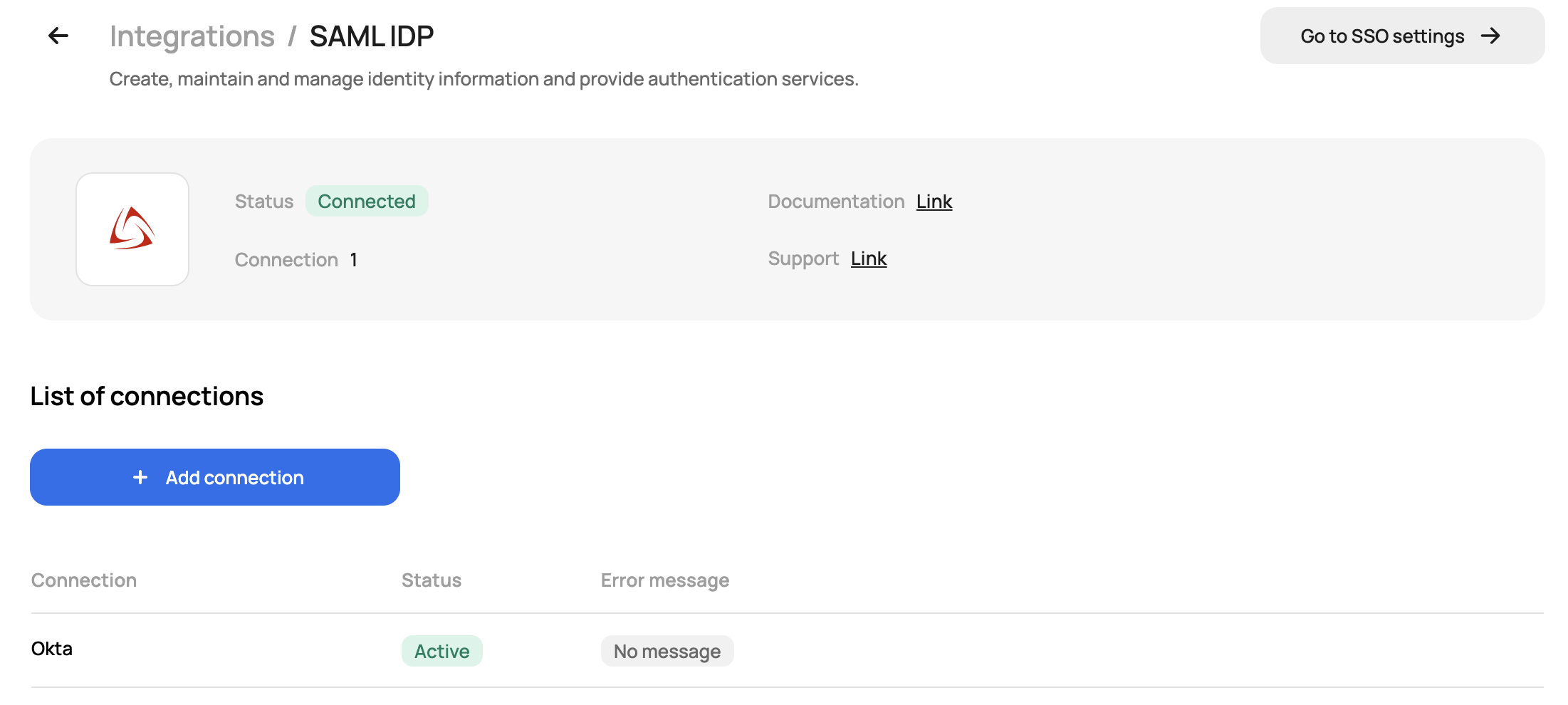
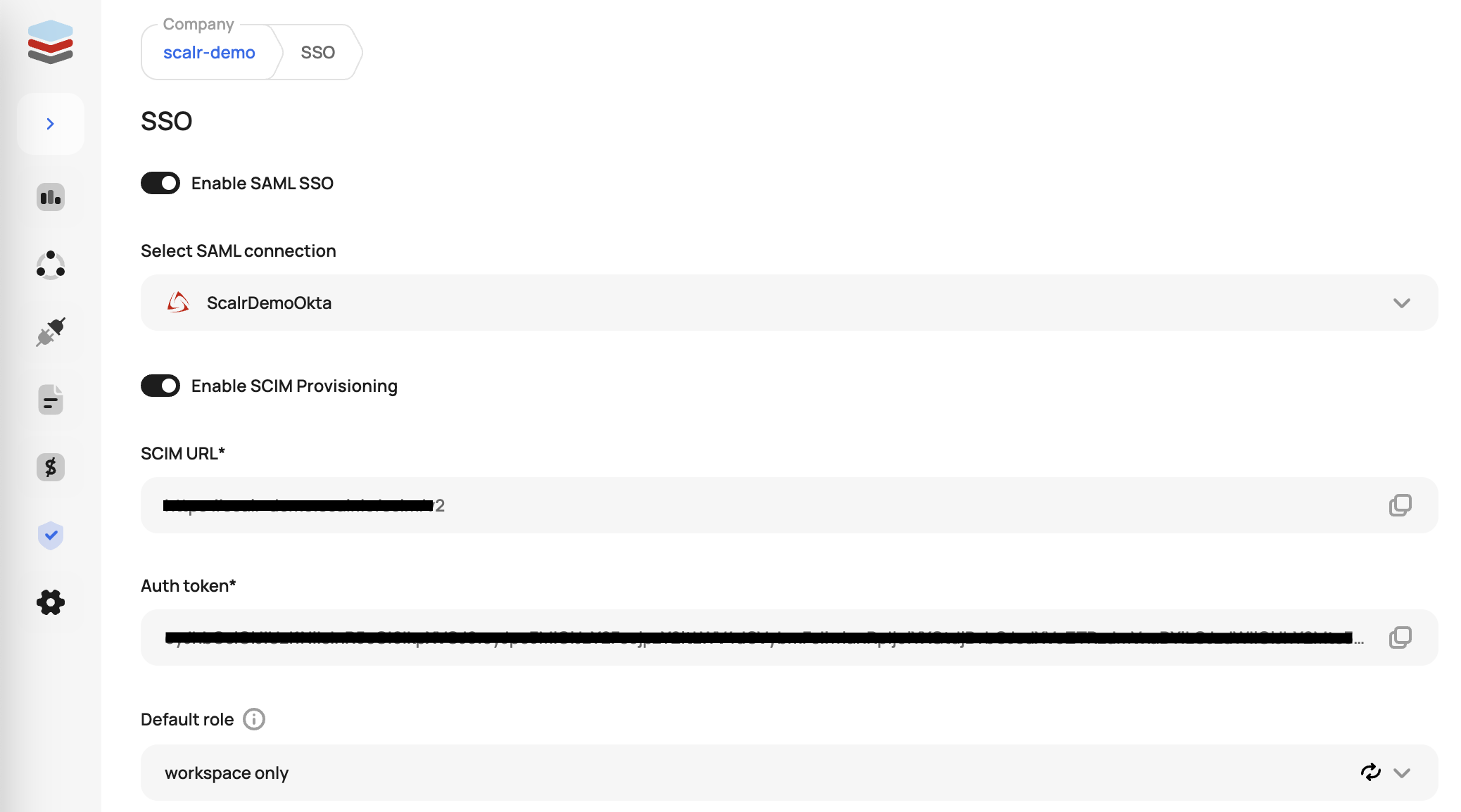
After you save the configuration, turn on the SSO authentication by going to the SSO settings under security:
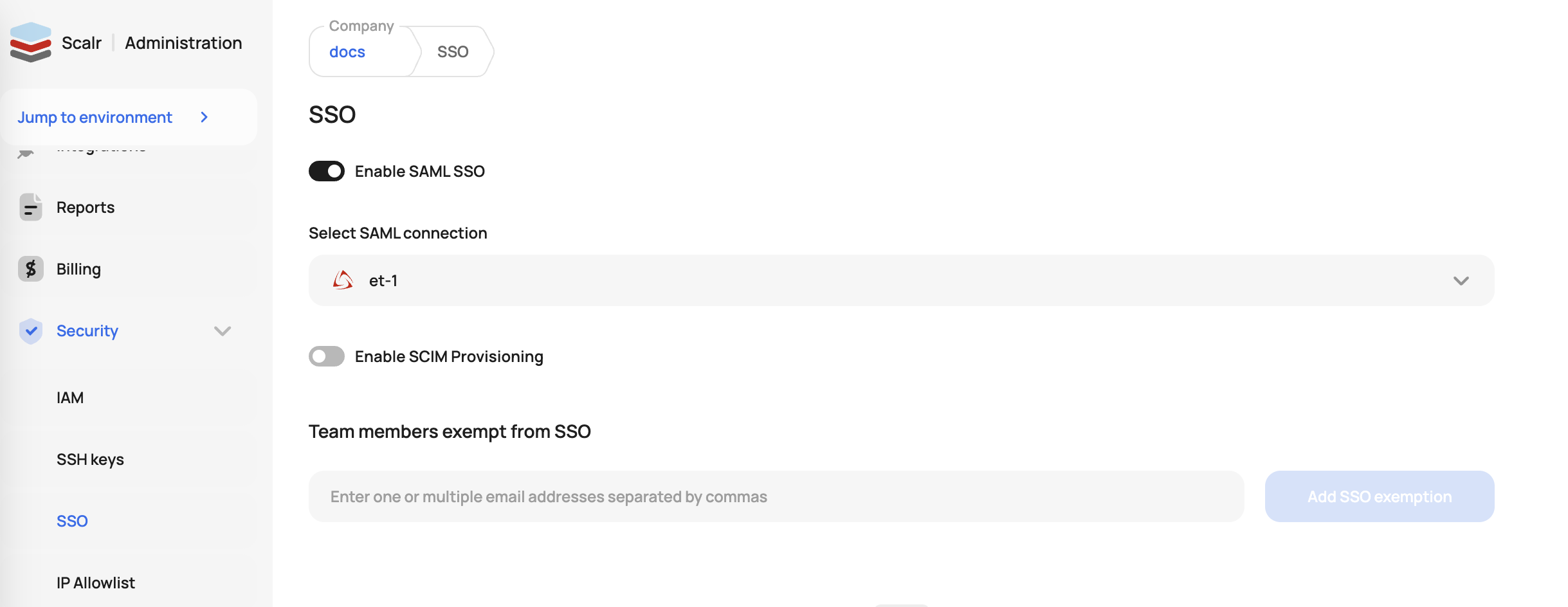
Users and Teams with SSO
After Scalr has been reconfigured for SSO, users and teams work as follows:
-
Teams map to SSO groups. Account admins have access to create teams in Scalr and the team name will be validated against the groups in SSO, so the team name must match the group name.
-
Teams must link to at least one environment and account.
-
Once a team has been linked and given the proper permissions, any member of the related SSO group can attempt to log in to Scalr. On the first login, a user record gets created in Scalr and set as SSO authenticated.
Read more on Scalr IAM here.
Break Glass Users
Incidents happen and it is likely that, at some point, your SSO provider will have an outage. If this happens, you can avoid being locked out of Scalr through the “break glass” feature. This feature allows you to specify a list of users who are exempt from SSO login the event of a SSO outage. These users can be specified by going to the SSO settings:
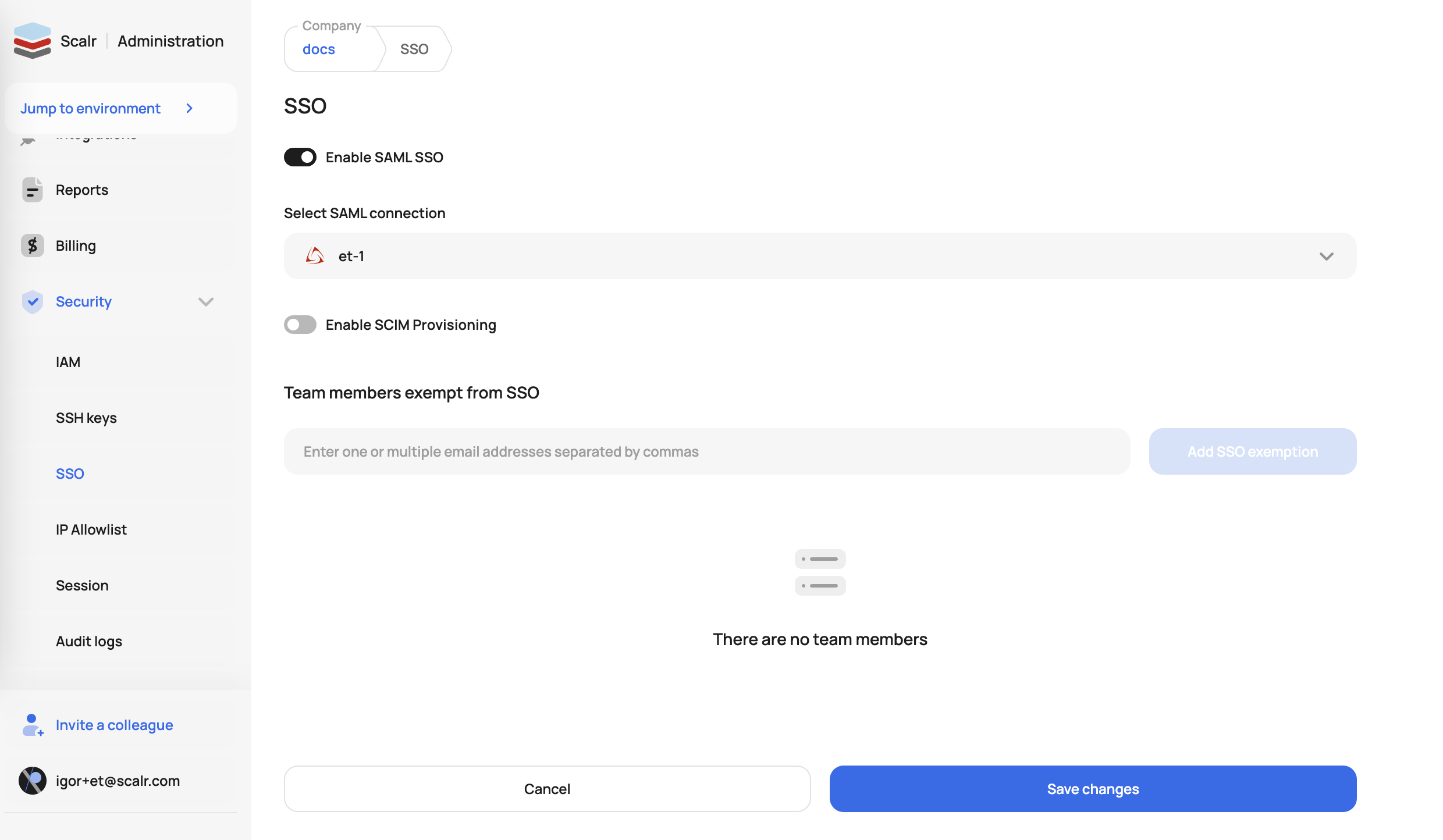
Bypass Login URLTo bypass SSO login, users should add the
?noLoginRedirectquery parameter to the account URL, e.g. https://account.scalr.io?noLoginRedirect
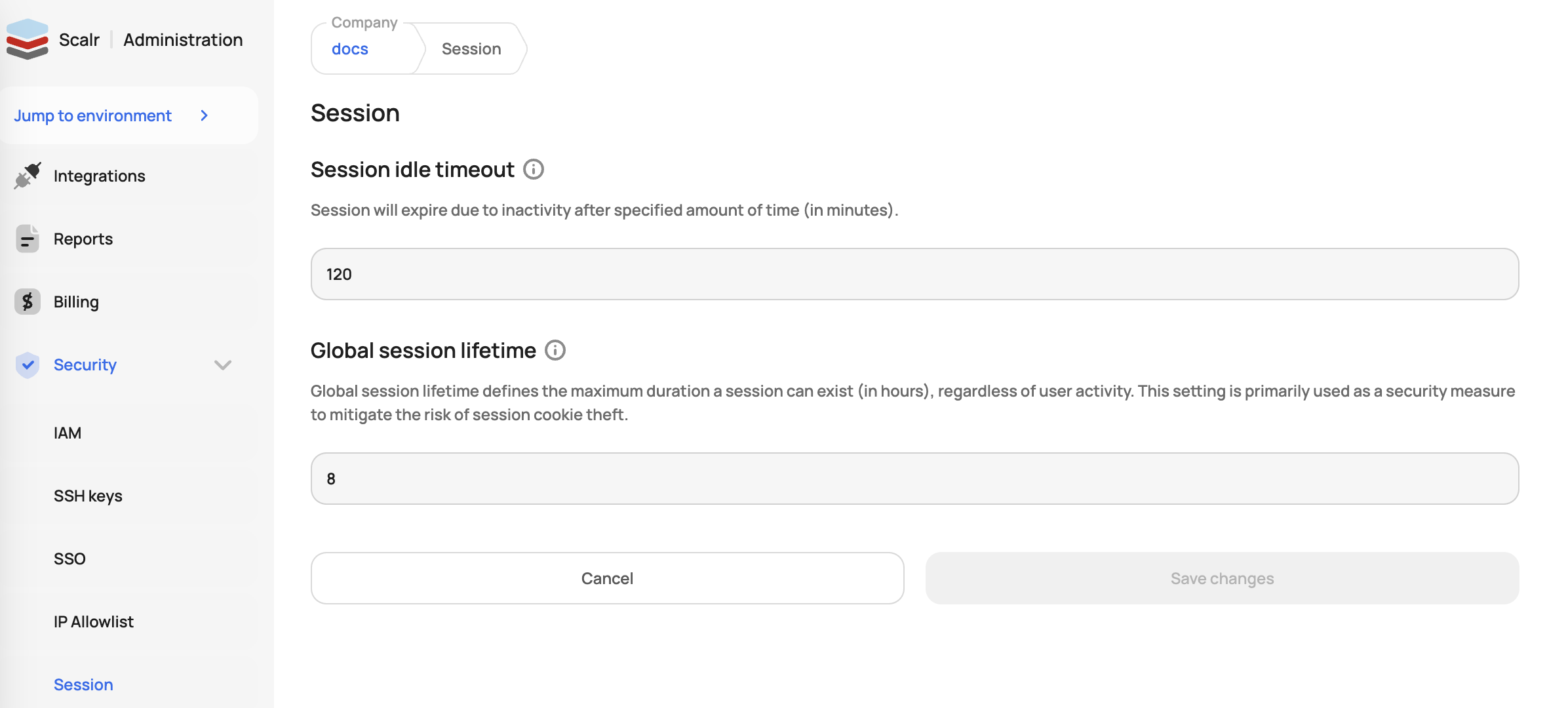
Session Timeout
The Session timeout can be configured by going to the session settings and updating the default timeout, which is 2 hours:
Default Role for SCIM Provisioning
Optionally, a default Scalr role can be set for all users provisioned through the SCIM integration, when supported by the SAML provider. If a role is not specified, the users will be assigned the account:read permission to give them access to Scalr, with minimal permissions.
Please note, that SCIM provisioning is currently only supported for Okta and Azure (EntraID) SSO.
Example Configurations
Scalr supports all SAML 2.0 SSO providers. Below is a list of common providers. If you do not see your provider in the list and have questions about how to integrate it, please open a support ticket.
Updated 6 months ago
