GitLab
Configuration
Integrating with a VCS provider unlocks the ability to use GitOps workflows, import modules, enable Open Policy Agent, and much more.
Before working through the authentication flow, the user who does the authentication needs at least the maintainer role in Gitlab to be able to pull back the repositories into Scalr.
To enable GitLab, go to the "Integrations" page at the account scope and select GitLab or Gitlab Enterprise (on-prem). Enter the provider name and, for Enterprise, the URL.
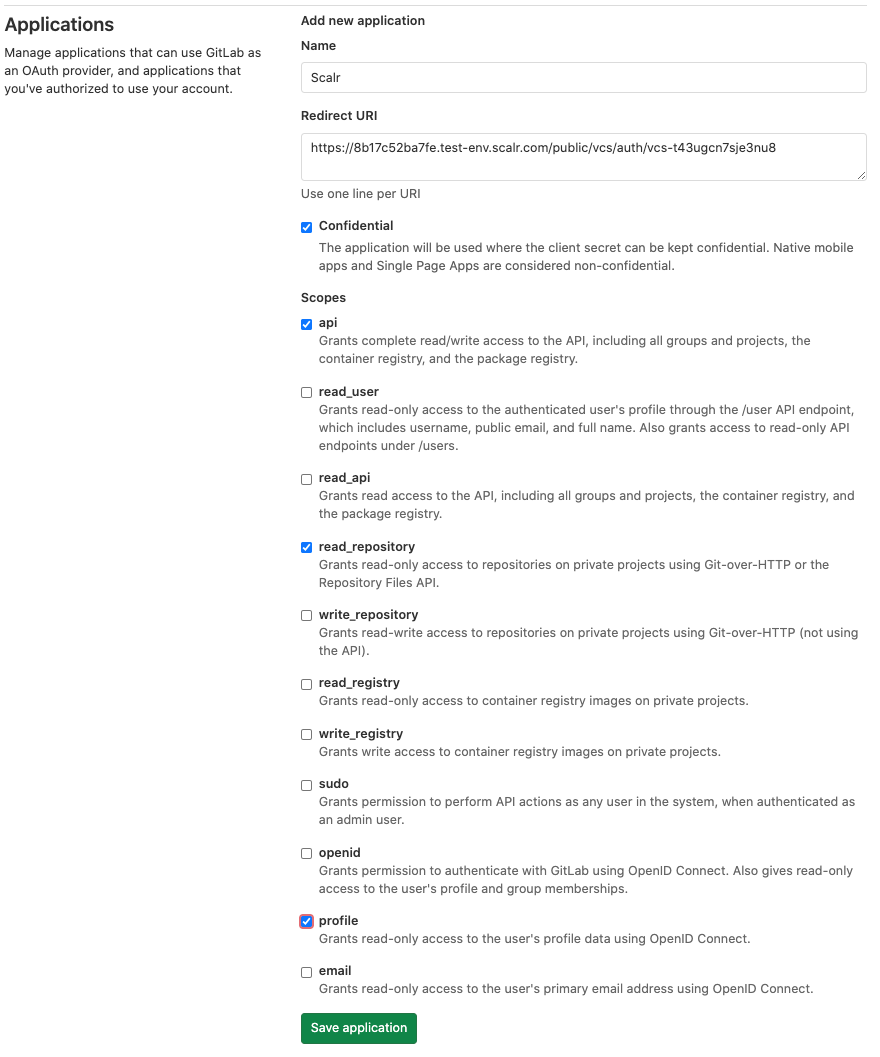
Copy the callback URL, click the “register a new OAuth application” link, and register a new OAuth app in Gitlab. Enable the following permissions in the application configuration:
- Confidential
- api
- read_repository
- profile
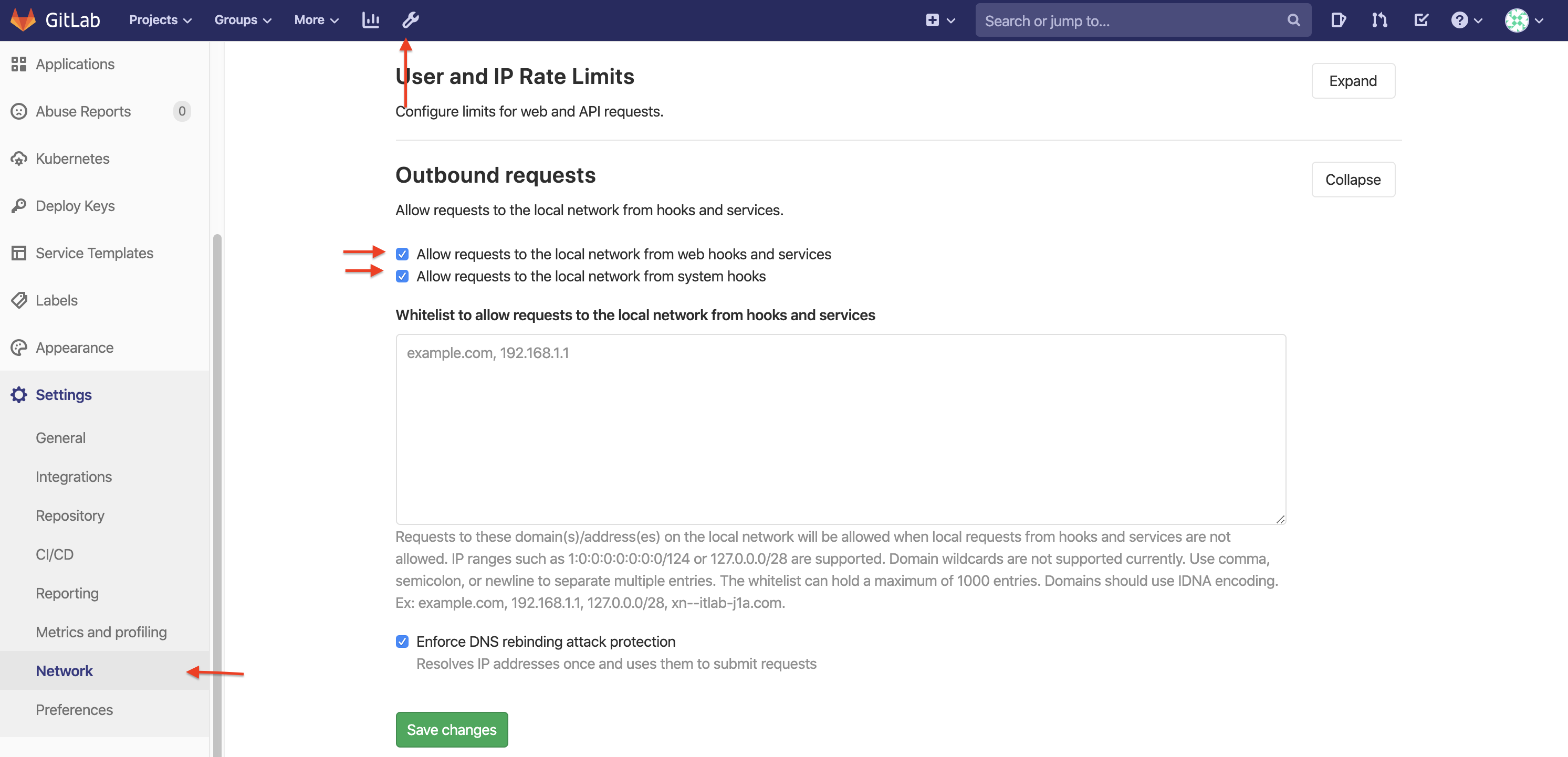
For Gitlab Enterprise check these options in the network settings (Admin Area):
- Allow requests to the local network from webhooks and services
- Allow requests to the local network from system hooks
Save and then copy the Application ID and Secret:
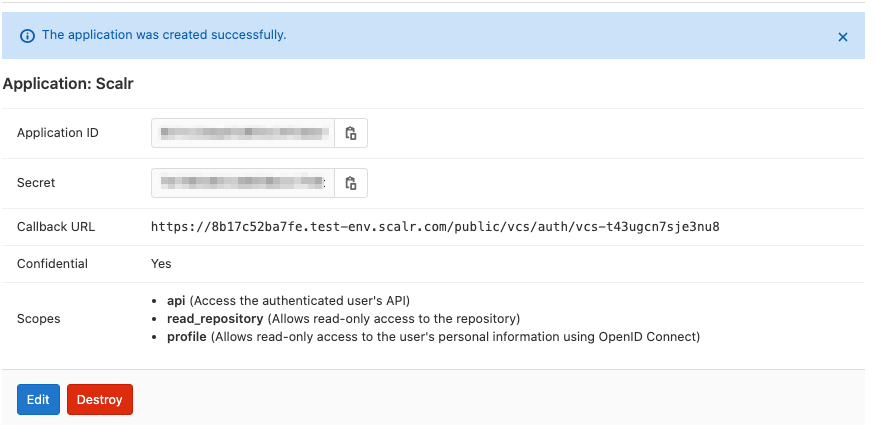
Go back to Scalr, enter the Id and secret. Upon clicking “create” a redirection back to Gitlab occurs to complete the authorization.
Commit Strategy
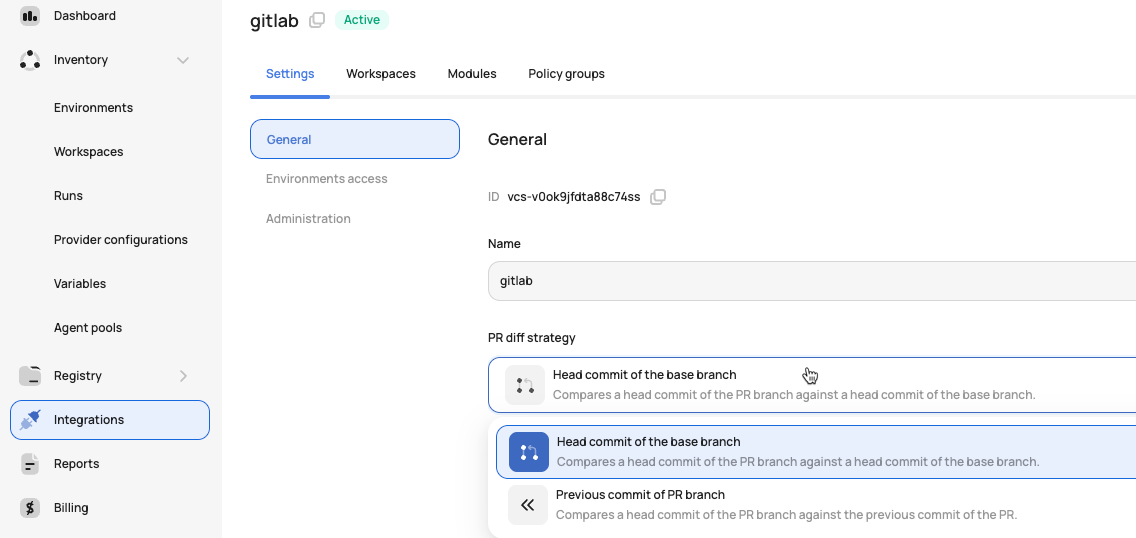
Admins can choose between the following two commit strategies when adding a VCS provider connection. All workspaces that use this VCS connection will inherit this setting:
Head Commit of the Base Branch: The default base commit strategy compares the latest head commit with the base branch commit
Previous Commit of the PR Branch: The commit compares the latest head commit with the previous head commit
The head commit strategy compares ALL commits in the PR every time a commit is pushed, while the previous commit strategy only compares the new commit to the previous commit that was made.
Pull Request Comments
Scalr provides the option to display run results in the GitLab pull request. The result will be an overall summary of the pull request as well as a per-workspace report showing what resources have been created, updated, or deleted. The cost and OPA results will also be displayed:
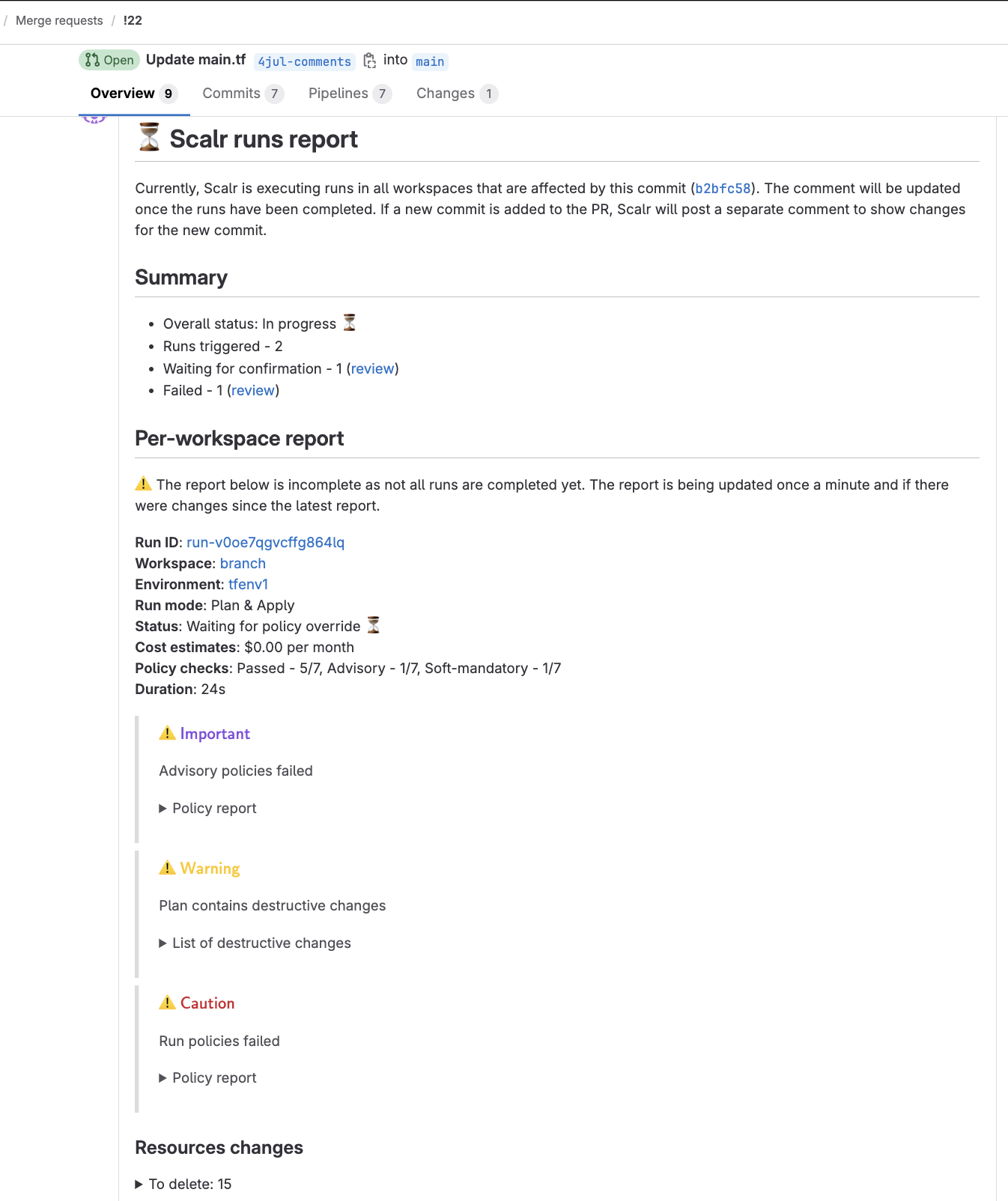
Enabling Comments
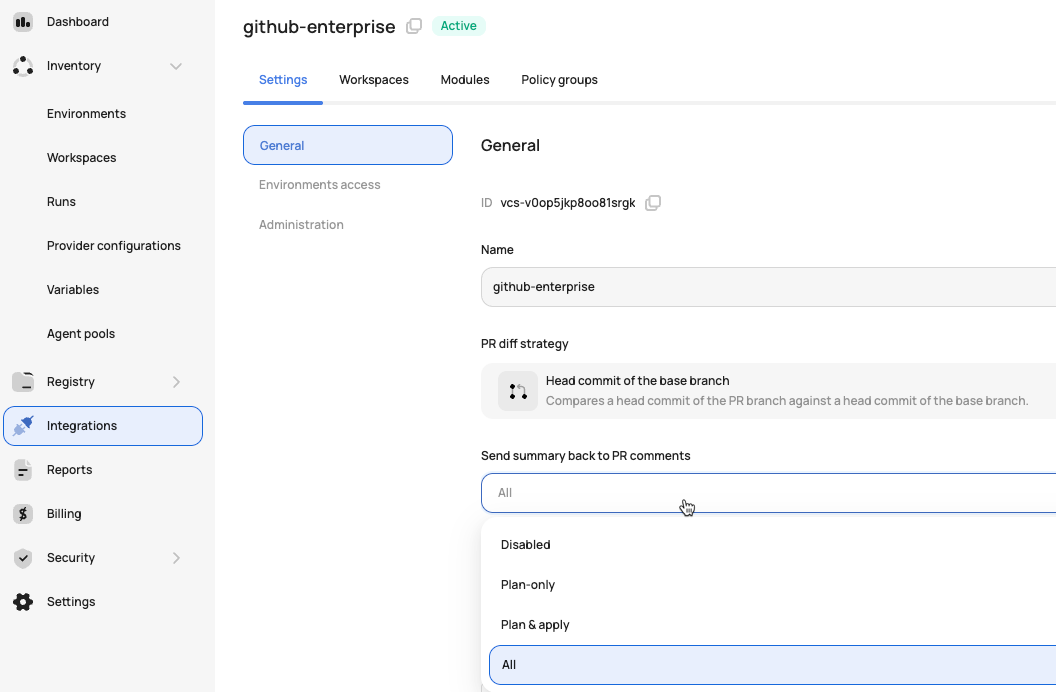
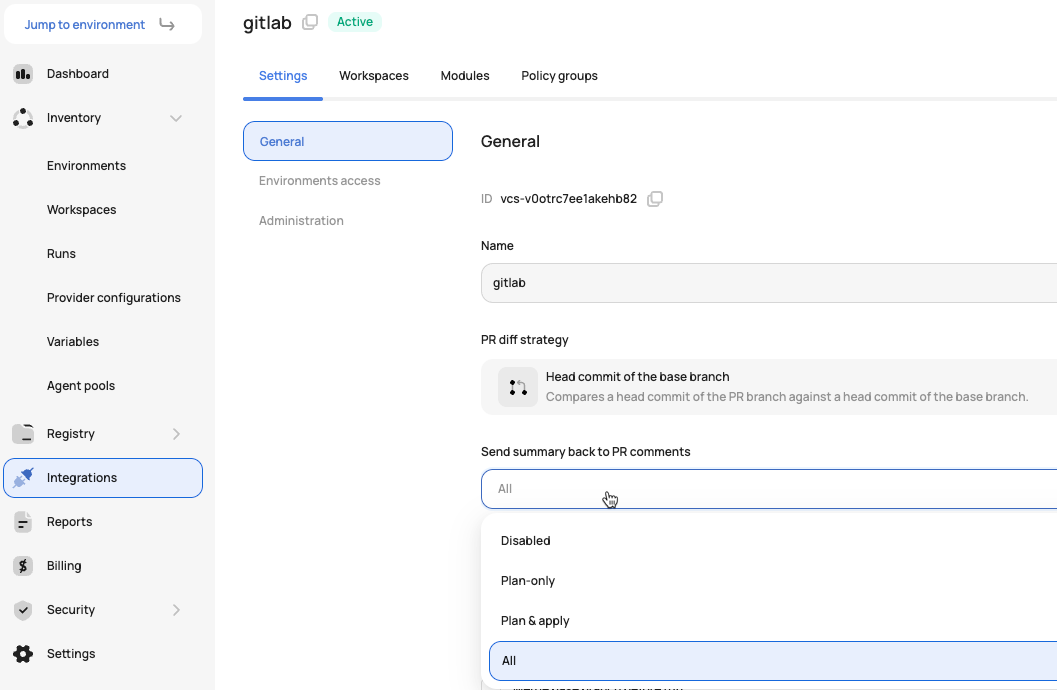
To be able to see the run summary in a GitLab comment before merging the PR, you must enable this in the GitLab integration:
Execute Runs from Pull Request Comments
To enable the ability to execute runs from pull request comments, you must enable it at the VCS provider integration level:
- Allow triggering plan-only runs from the PR comments: Any user who can comment on the PR can execute a
plan-onlyrun in Scalr. - Allow triggering plan & apply runs from the PR comments: Any user who can comment on the PR can execute an
applyrun in Scalr.
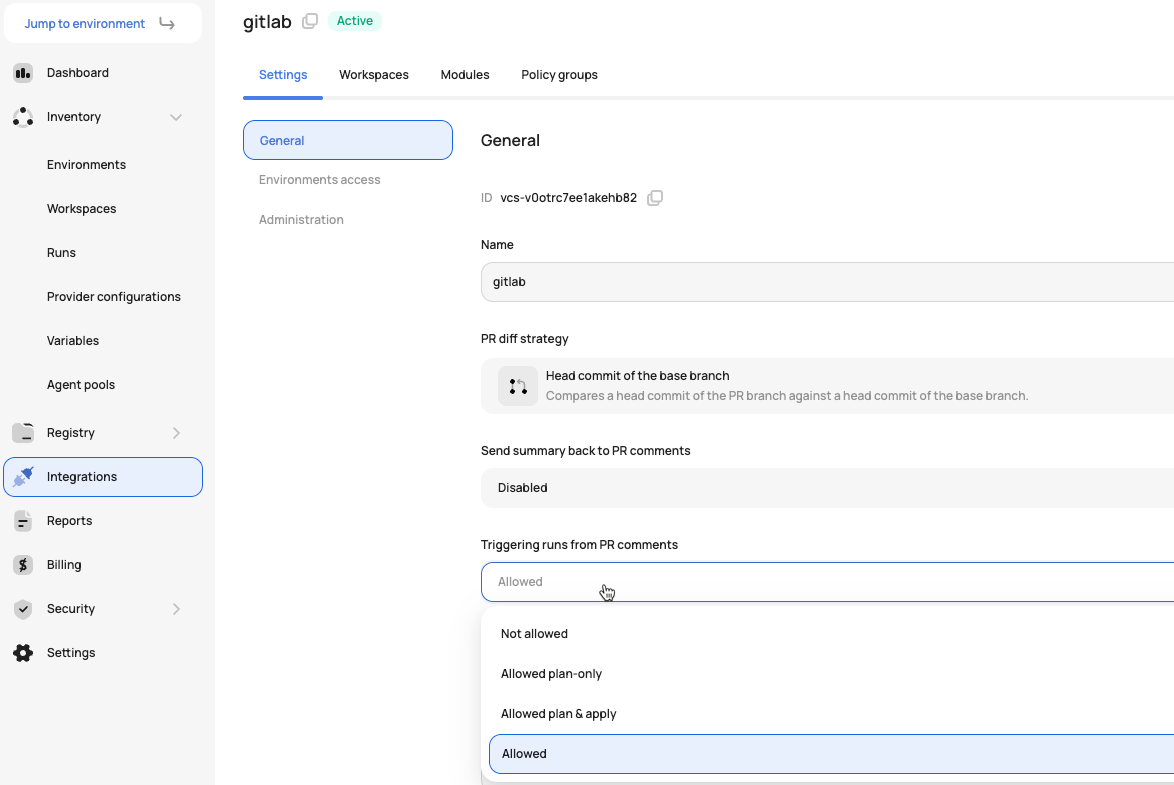
When enabled, all users who have access to the pull request comment can execute a run. The workspace must have "Enabled VCS-driven dry runs" enabled in the settings for this feature to work.
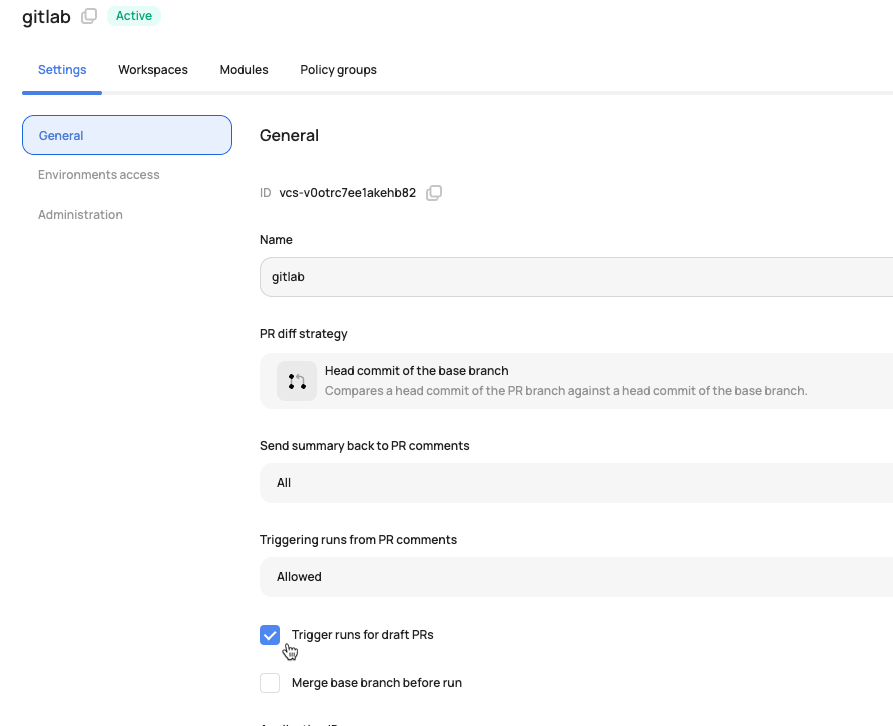
Draft PRs
Draft pull requests are commonly used during the early development cycles to note when a pull request is in a draft state. Since draft pull requests are so early on in the development cycle, it's possible that you don't want a Scalr plan to execute when pull requests are opened. Scalr gives you the option to ignore draft pull requests by unchecking "Trigger runs for draft pull requests". As of right now, this will apply to any workspace that is linked to the VCS provider.
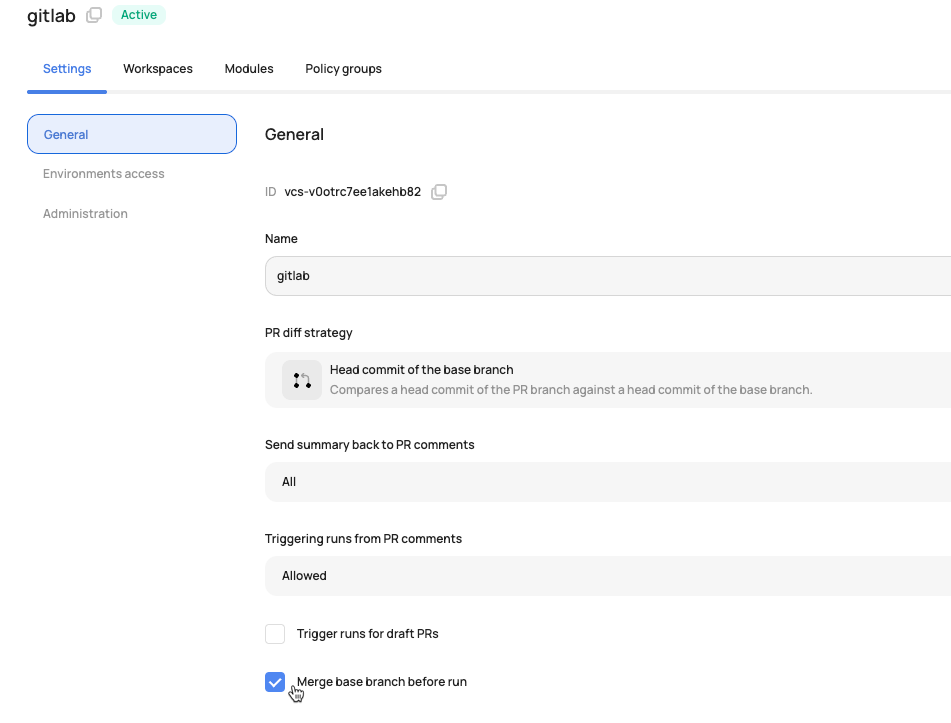
Automatic Base Branch Merge Before Run Execution
VCS-driven workspaces can automatically merge the base branch into the head branch before triggering a run. This ensures that runs are always executed against the latest code in the base branch, providing more accurate and reliable results. This helps a common pain point where runs could be executed against outdated head branches, potentially leading to false-positive results or failed applies after merging.
To implement this feature, enable the auto-merge option when configuring the VCS provider:
Updated 6 months ago
