Storage Profiles
Overview
Note: This is included in the enterprise plan. Contact support if you have any questions.
Storage profiles provide organizations with the ability to customize the storage location and method for their blobs. A blob consists of Terraform/OpenTofu state files, code, and run artifacts such as logs. You can configure profiles through the API or by navigating to Account → Security → Storage Profiles in the Scalr UI. Storage profiles can be configured at the account level or per environment.
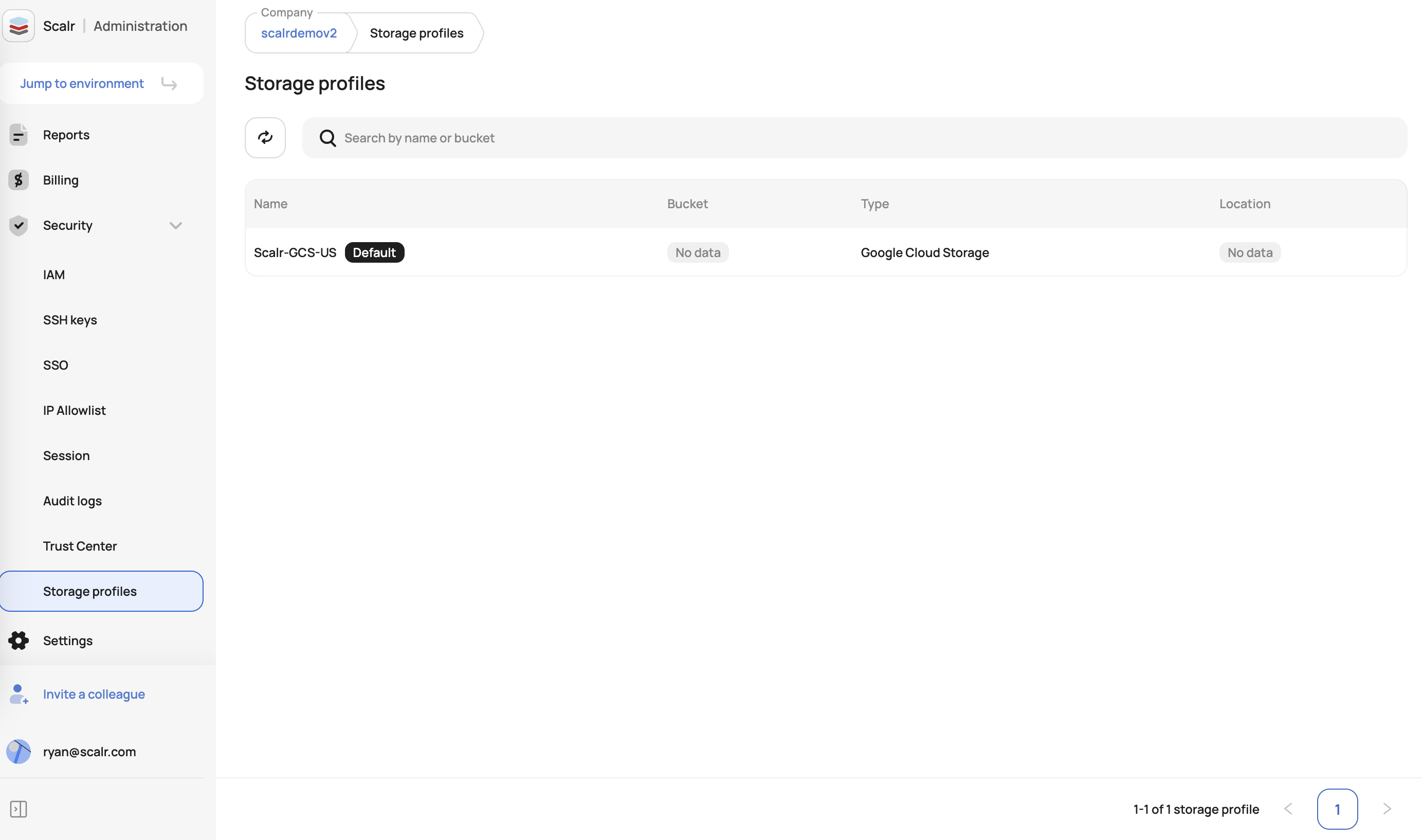
Storage Options
Scalr offers two primary storage models:
Scalr-Managed Storage (Default)
- Blobs are stored in a Scalr-managed bucket
- This is the default option for all accounts
- No additional configuration required
Customer-Managed Storage
Store your data in your own cloud storage:
- AWS S3 buckets
- GCP buckets
- Azure Storage accounts
This option is ideal when you require:
- Data storage within your own infrastructure
- Specific data residency requirements
What Gets Stored
When using customer-managed storage, the following objects are stored in your bucket:
- Terraform/OpenTofu state files
- Configuration file versions
- Plan JSON and binaries
- Terraform/OpenTofu logs
Configuration Guides
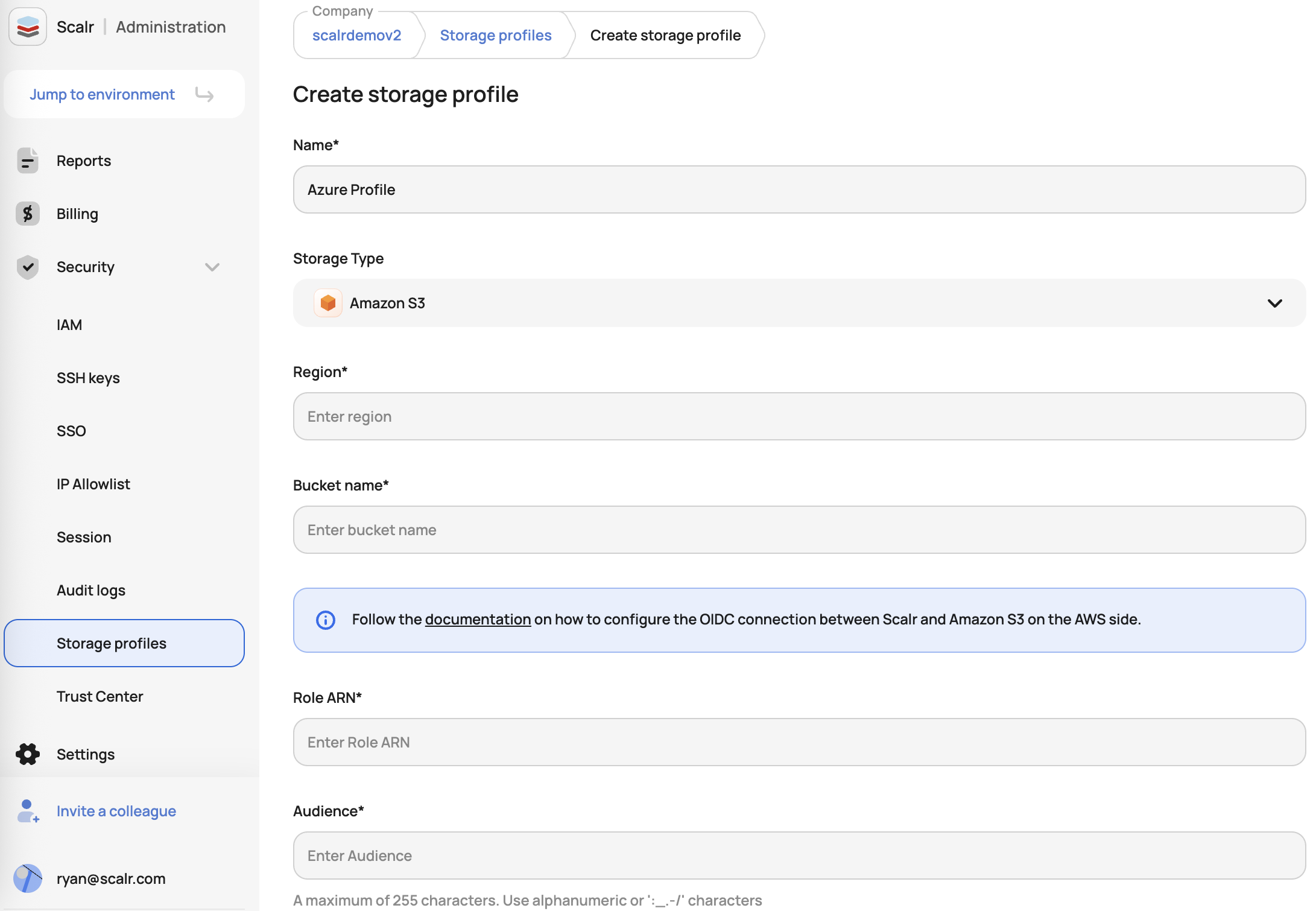
AWS S3 Storage Profile
Prerequisites
- An S3 bucket in AWS
- OIDC authentication setup
- IAM role with appropriate permissions
Setup Steps
-
Create S3 Bucket
- Create a bucket in AWS
- Ensure Scalr has access to the bucket
-
Configure OIDC Authentication
- In AWS IAM, add an identity provider:
- URL:
https://scalr.io - Create an appropriate audience value
- URL:
- In AWS IAM, add an identity provider:
-
Create IAM Role
- Select web identity and your OIDC provider
- Required permissions:
s3:ListBucket s3:GetObject s3:PutObject s3:DeleteObject - For KMS encryption, add:
kms:GenerateDataKey kms:Decrypt
-
Configure Trust Policy
Add the following to your role's trust policy. Make sure to updateyour-aws-account-id,your-audience, andscalr-account-namewith the real values.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowScalrOIDCAccess",
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<your-aws-account-id>:oidc-provider/scalr.io"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"scalr.io:aud": "<your-audience>"
},
"StringLike": {
"scalr.io:sub": "scalr:account:<scalr-account-name>"
}
}
}
]
}- Create Storage Profile
Use the Scalr UI or API to create the profile:
UI:
API:
POST {{host}}/api/iacp/v3/storage-profiles
{
"data": {
"type": "storage-profiles",
"attributes": {
"backend-type": "aws-s3",
"aws-s3-bucket-name": "example-aws-bucket",
"aws-s3-audience": "my-awesome-audience",
"aws-s3-region": "us-east-1",
"aws-s3-role-arn": "arn:aws:iam::123456789012:role/your-role-name",
"default": true,
"name": "aws-s3-storage-profile"
}
}
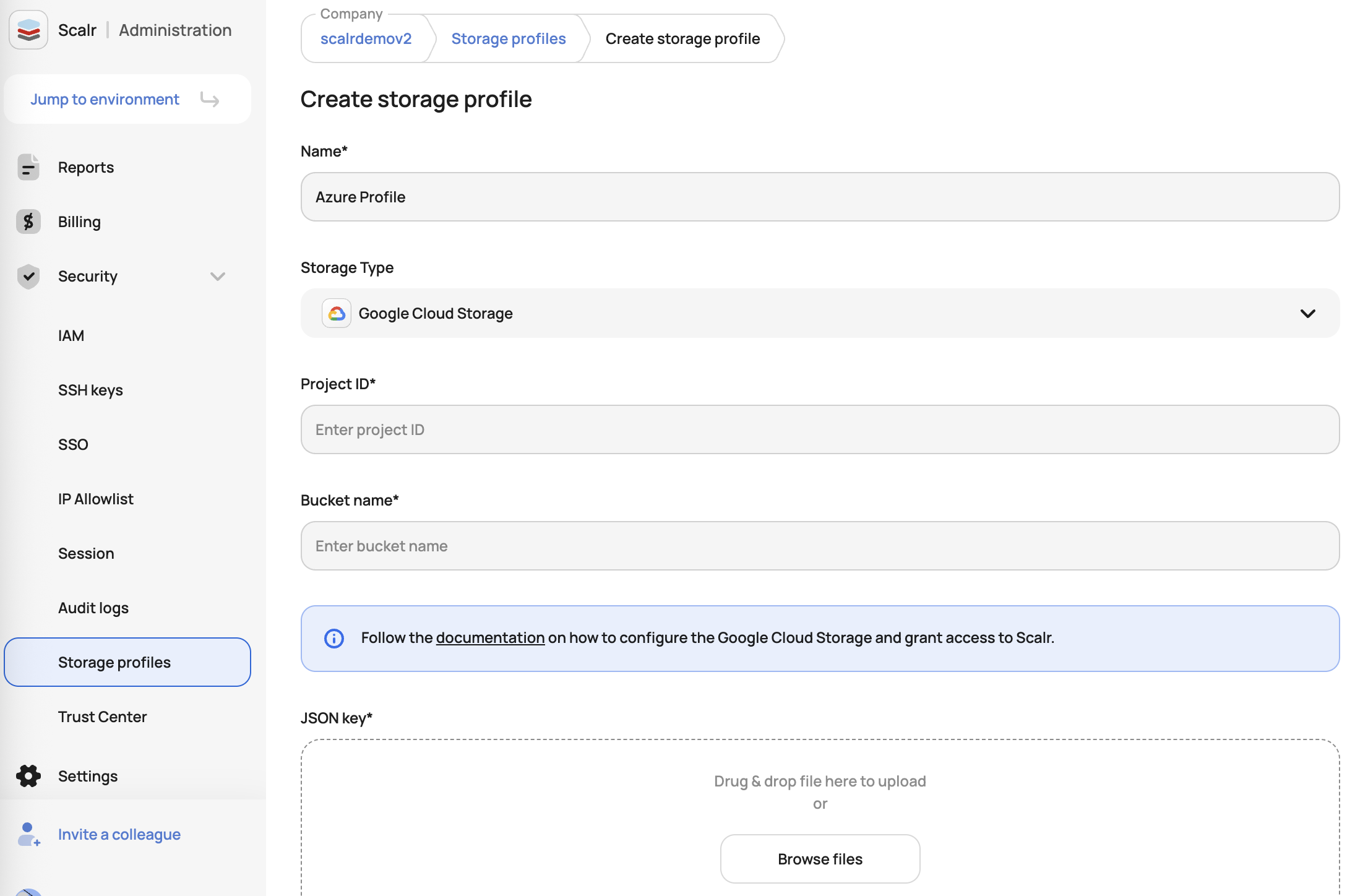
}GCP Storage Profile
Prerequisites
- GCP bucket
- Service account with Storage Admin role
- Appropriate IAM permissions
Setup Steps
-
Create GCP Bucket
Recommended configuration:Location type: Multi-region Default storage class: Standard Public access: Subject to object ACLs Access control: Fine-grained Protection: Soft Delete Bucket retention: None Lifecycle rules: None Encryption: Google-managed -
Create Storage Profile
Use the Scalr UI or API to create the profile:
UI:
API:
POST {{host}}/api/iacp/v3/storage-profiles
{
"data": {
"type": "storage-profiles",
"attributes": {
"backend-type": "google",
"default": true,
"name": "gcp-storage-profile",
"google-storage-bucket": "your-bucket-name",
"google-project": "your-project-id",
"google-credentials": {
// Your GCP service account JSON key
}
}
}
}AzureRM Storage Profile
Prerequisites
- Azure subscription with AzureRM permissions
- Azure AD application
- Federated credentials setup
Setup Steps
-
Create Azure AD Application
- Navigate to Azure Active Directory → App registrations
- Create new registration
- Note the Application (client) ID
-
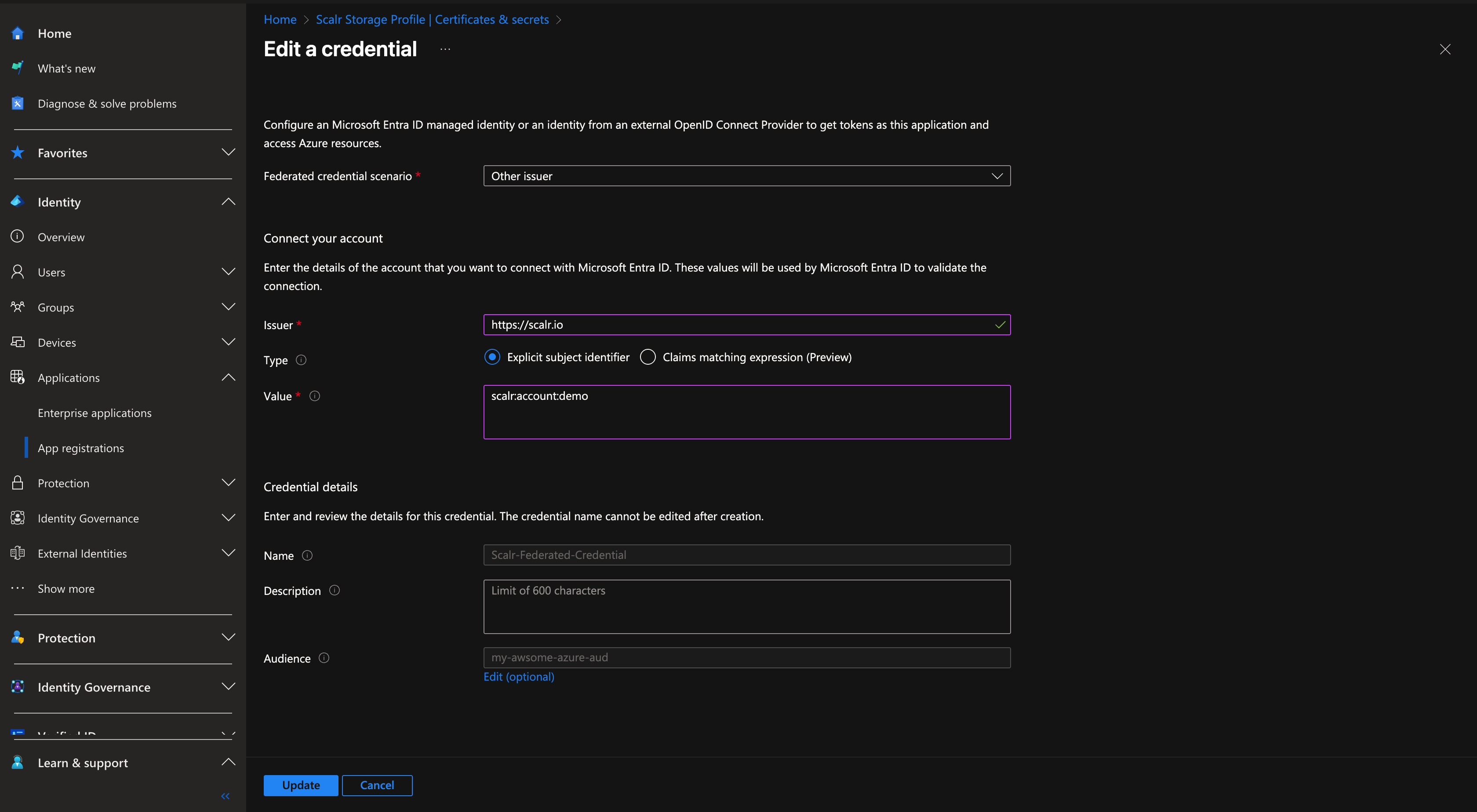
Configure Federated Credentials
- Go to Certificates & secrets → Federated credentials
- Add credential with:
- Issuer:
https://scalr.io - Subject identifier:
scalr:account:<your-account-name> - Audience: Your OIDC audience value
- Name: Descriptive name (e.g., "Scalr-Federated-Credential")
- Issuer:
-
Grant Storage Access
- Navigate to your Storage Account
- Go to Access Control (IAM)
- Add role assignment:
- Role: Storage Blob Data Contributor
- Assign to: Your Azure AD application
-
Create Storage Profile
Use the Scalr UI or API to create the profile:
UI:
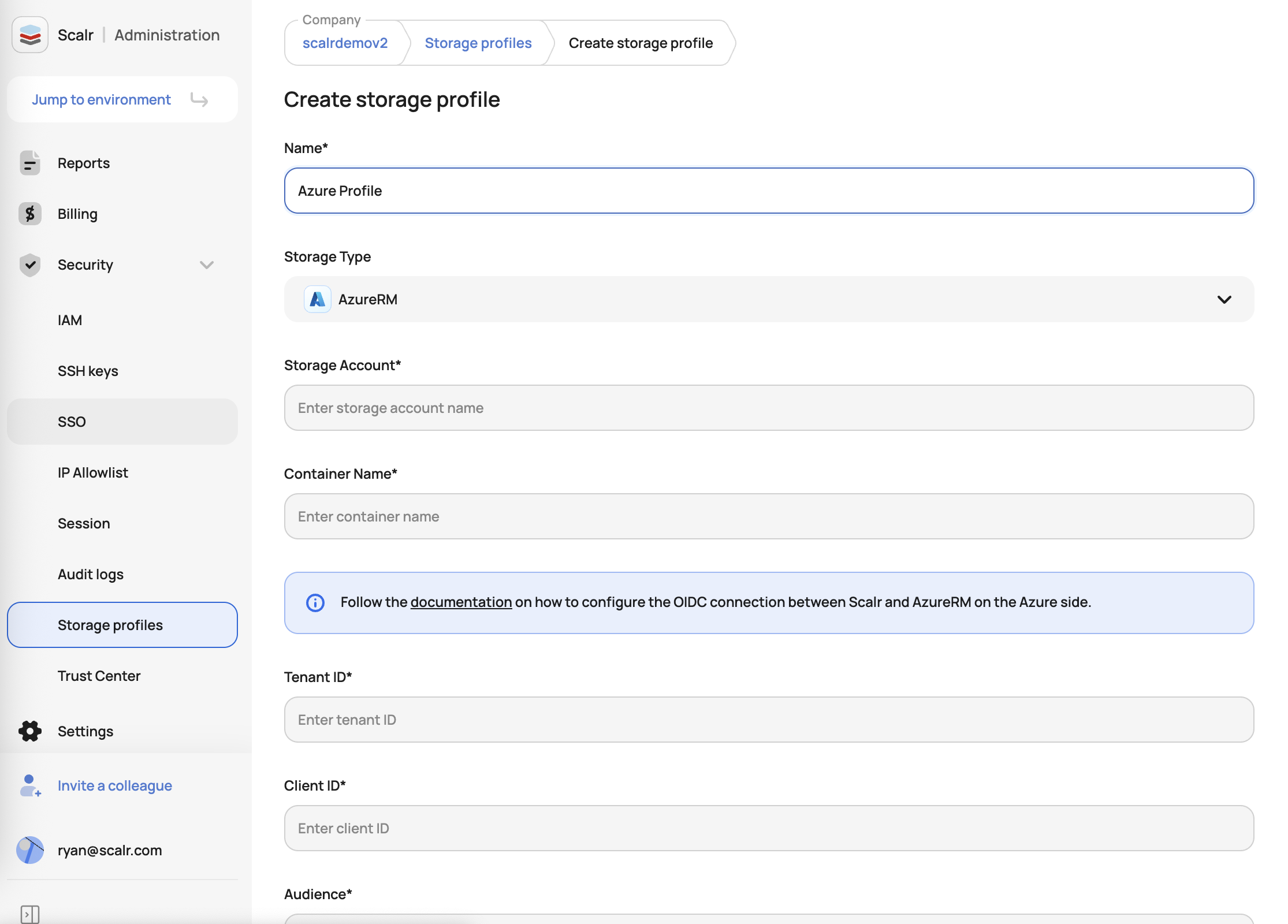
API:
POST {{host}}/api/iacp/v3/storage-profiles
{
"data": {
"type": "storage-profiles",
"attributes": {
"backend-type": "azurerm",
"name": "azure-storage-profile",
"default": true,
"azurerm-storage-account": "your-storage-account",
"azurerm-container-name": "your-container",
"azurerm-tenant-id": "your-tenant-id",
"azurerm-client-id": "your-client-id",
"azurerm-audience": "your-audience"
}
}
}Environment-Specific Configuration
Storage profiles can be assigned to environments through the UI or API. It can be done either when creating the environment or updating:
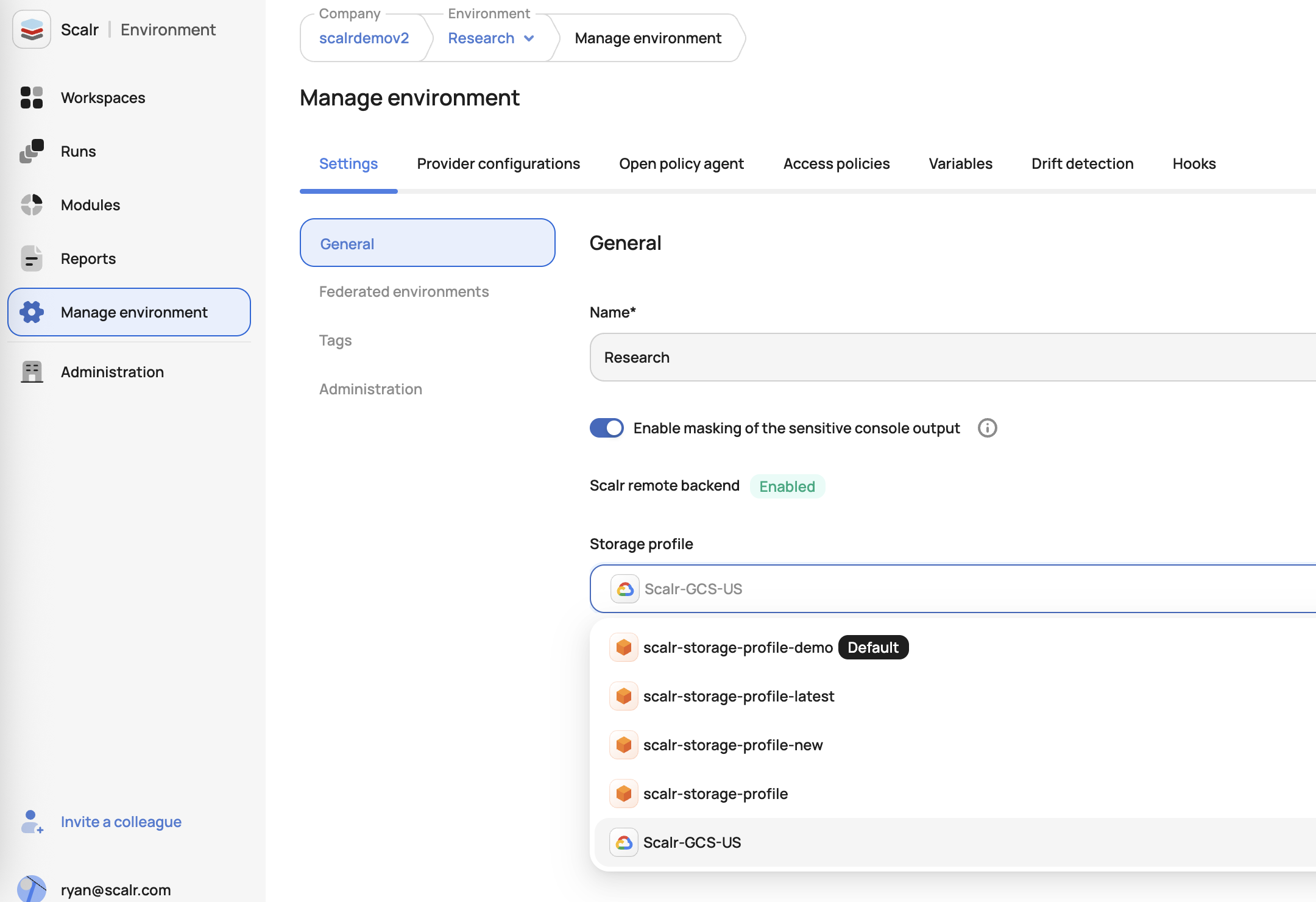
Sample API call:
PATCH {{host}}/api/iacp/v3/environments/<environment-id>
{
"data": {
"attributes": {
"mask-sensitive-output": true,
"remote-backend": true,
"remote-backend-overridable": true
},
"relationships": {
"storage-profile": {
"data": {
"type": "storage-profiles",
"id": "<storage-profile-id>"
}
}
},
"type": "environments"
}
}Important Limitations
Profile Updates
- After creating blob objects in a profile, only the profile name and credentials can be updated
- Other fields cannot be modified
Profile Migration
- After the new profile is created, operations that create or modify blobs will use the new default profile.
- After creating a profile and marking it as default, all new objects will use it going forward.
- Scalr will know where to look for blobs in both the old and new profiles. You do not need to re-import the state or do any manipulation.
Profile Deletion
- A storage profile cannot be deleted if it contains blob objects
- All objects must be removed before deletion
Updated 24 days ago
