Identity and Access Management
Getting Started
The Scalr IAM model was built with flexibility in mind to fit any type of organization. There are a few key components to think about when building IAM in Scalr:
- Roles - A collection of permissions that can be assigned to a user or team.
- Teams and Users - Teams and users must be assigned a role to be able to do anything in Scalr.
- Access Policies - The component that links a role to a team/user.
- Scope - Access policies can be assigned at the account, environment, or workspace scope.
To manage IAM, go to the account scope, then security, and click on IAM:
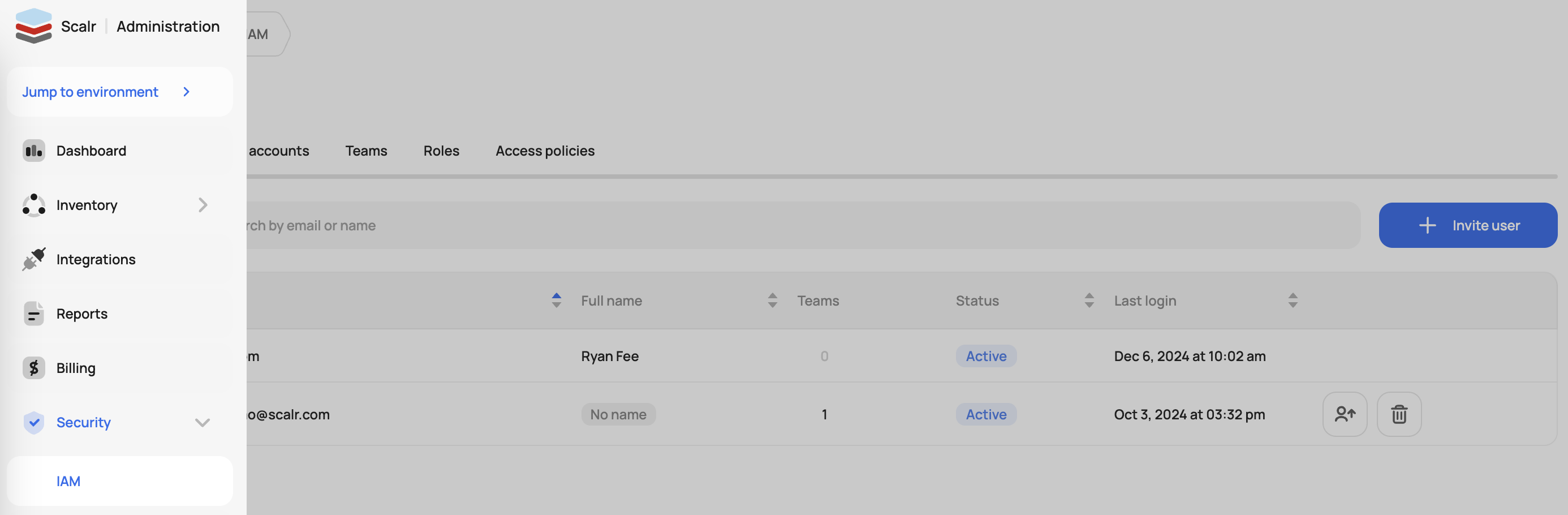
Roles
Roles are collections of permissions. You will find that you can use two types of roles:
- System roles - A set of permissions that have been pre-created for common use cases.
- Custom roles - Roles that can be created by someone in the account who has permission to do so.
When creating a role, keep in mind where the object permissions need to be set. For example, the variable object exists at the account, environment, and workspace scope. When building a role, you only see the variable:* permission as the scope of the permission is set with access policies.
Users and Teams
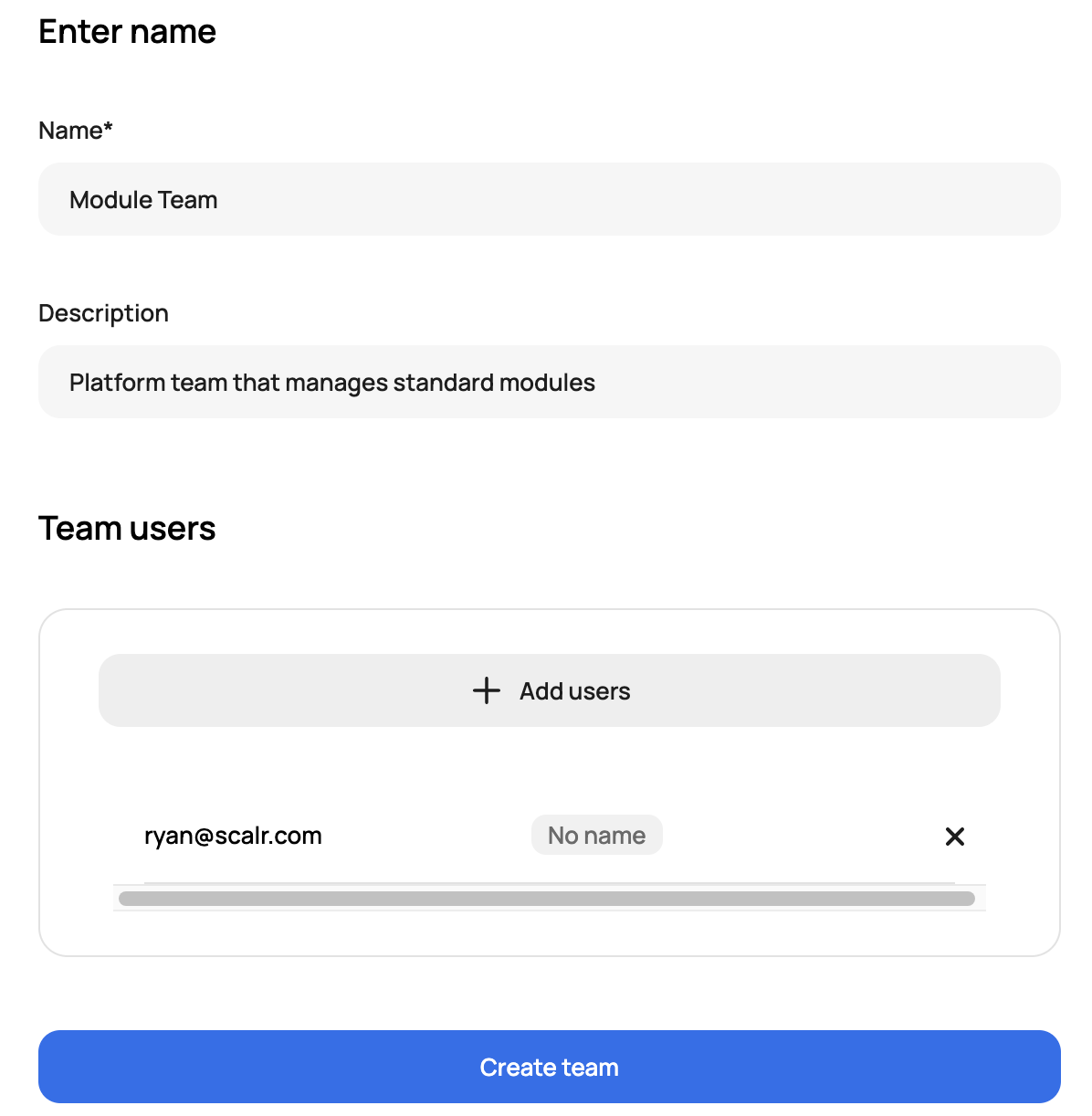
An individual user or team can be granted access to Scalr. Users and Teams can be managed locally in Scalr or by using an external identity provider, which is free on all plans in Scalr. See more on the SSO integration here.
A user or team must have an access policy assigned to it for them to be able to do anything in Scalr. Just inviting a user does not provide enough access to log into a Scalr account.
Access Policies
Access policies are the combination of a user, team, or service account and a role. When linked, access policies are what give users the ability to do anything in Scalr. The policies can be set at three scopes:
- Account - Account policies grant access to the account in general and to any object within the account scope.
- Environment - Environment access policies can grant permissions to a specific environment.
- Workspace - Workspace access policies can grant permissions to the specific environment.
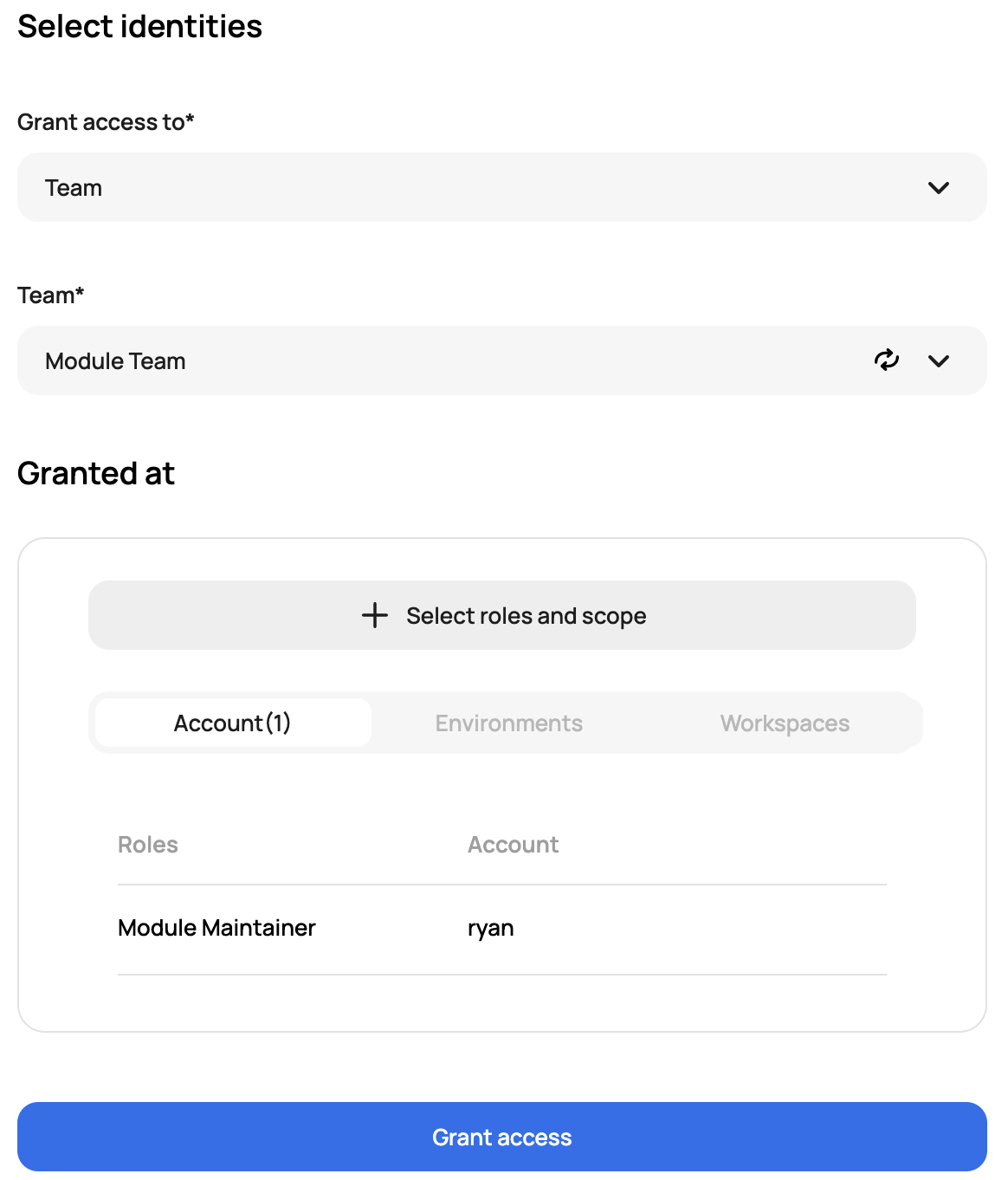
Access policies in conjunction with the Scalr scope are what make Scalr extremely flexible. For example, let's say your Scalr environments have a one-to-one mapping with application teams. Every time an application is onboarded into Scalr, an environment is created, and an initial workspace containing the core infrastructure for the application is deployed. In this case, there is the ability to give full admin access to the core infrastructure workspace to the central IT team. Then the app team will have read-only to that workspace to be able to get output information or be able to do remote state data lookups as needed. The app team then has full admin access to all other objects within the environment and all new workspaces.
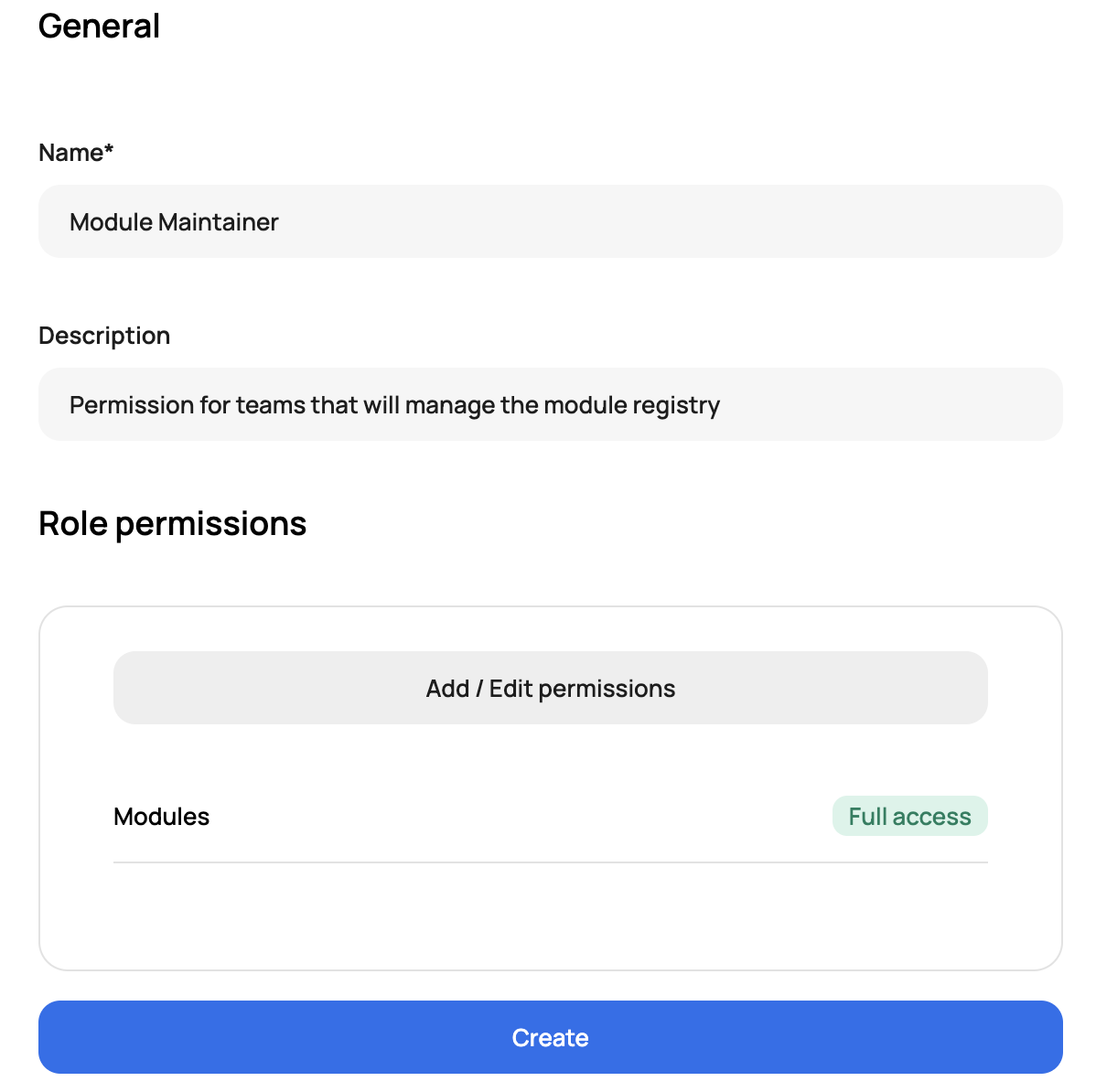
Another example is module management. Modules can be managed at the account of environment scope. It is common for a platform team to manage all shared modules at the account scope, which can be used by all environments and teams. In this case, the platform team will have an access policy that only gives them access to the module registry at the account scope and no access to an environment. The app teams will then have the ability to use the modules within their environment and can have an access policy assigned to them to allow them to create app-specific modules only in their environment. This will give a cumulative approach of modules from the account and environment scope without having to worry about users deleting any shared modules.
Examples
Here are a couple of examples of how to use roles and access policies:
Scenario | How To |
|---|---|
A team requires full access to a specific environment. | Create an environment access policy with the system |
A team only needs to manage modules at the account scope. | Create a custom role with Assign the above role to a team using an access policy at the account scope. |
A team requires access to one workspace to read plan outputs and state files. | Assign the system role Create a custom role with permissions Assign the above role to a team using an access policy at the workspace scope. |
A team requires read-only access to all environments in the account. | Create an account access policy with the system role |
Scalr OIDC
Scalr supports the ability to connect to the Scalr API using OpenID Connect (OIDC) to eliminate the need for static credentials. This guide provides a step-by-step process to configure OIDC authentication using Scalr's public API, along with detailed explanations of each request and its parameters. The example below uses GitHub Actions; please open a ticket if you have questions about a different third-party connection.
Register a Workload Identity Provider
A workload identity provider allows Scalr to verify identity tokens issued by an external OIDC provider. In Scalr, go to Security -> IAM -> Workload Identity Providers to add a provider. In this case, GitHub Actions is going to be added as the provider:
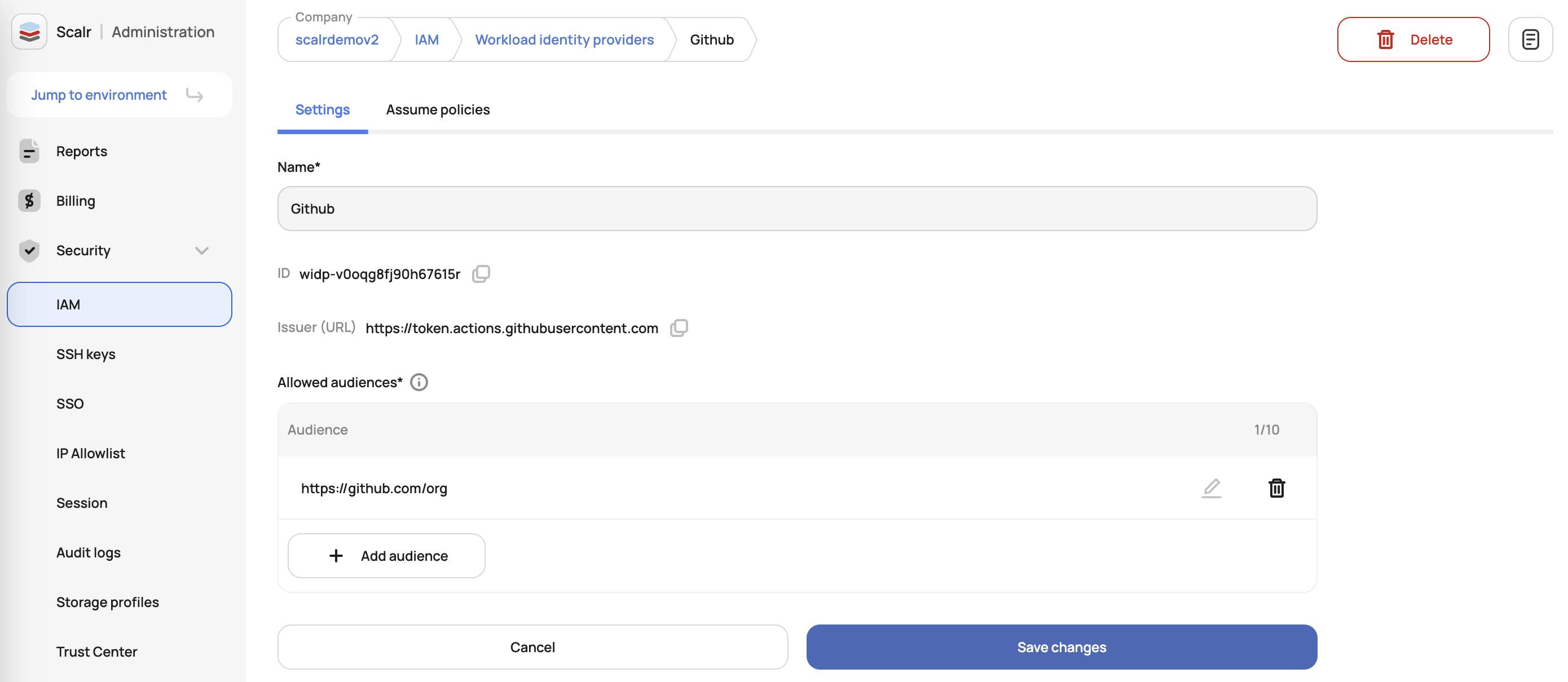
The audience must be updated to your username or org.
- Name: A unique identifier for this identity provider within Scalr.
- Issuer (URL): The OIDC provider's token endpoint (GitHub Actions in this case).
- Allowed-audiences: A list of trusted audience values that the provider is allowed to provide. For GitHub, this should be your actual org.
Configure Assume Policy for a Service Account
After registering the workload identity provider, an assume policy definition must be defined. This allows the provider to obtain a temporary access token for the specific service account.

- maximum-session-duration: Sets the session duration in seconds. Default: 3600 (1 hour) (Optional).
- claim-conditions: Defines the conditions under which the identity provider can assume this service account.
- repository: Restricts access to a specific GitHub repository. (This should be the actual name of your org/respository)
Update Third Party
The following script can be used in the GitHub Action to authenticate OIDC and execute a run in a workspace:
name: Test Scalr OIDC
on:
push:
branches:
- main
env:
SCALR_HOSTNAME: <account>.scalr.io
SCALR_ENVIRONMENT: <your-environment>
SCALR_WORKSPACE: <your-workspace-name>
SCALR_SA_EMAIL: <the email created in Scalr for the service account>
jobs:
run-opentofu:
runs-on: ubuntu-latest
environment: development
permissions:
id-token: write
contents: read
steps:
- name: Checkout Repository
uses: actions/checkout@v3
- name: Generate GitHub Actions OIDC ID Token
id: generate-oidc-token
run: |
RESPONSE=$(curl -s -X POST -H "Authorization: Bearer $ACTIONS_ID_TOKEN_REQUEST_TOKEN" "$ACTIONS_ID_TOKEN_REQUEST_URL")
OIDC_ID_TOKEN=$(echo $RESPONSE | jq -r '.value')
if [ -z "$OIDC_ID_TOKEN" ] || [ "$OIDC_ID_TOKEN" == "null" ]; then
echo "Error: Failed to retrieve OIDC token."
exit 1
fi
echo "OIDC_ID_TOKEN=$OIDC_ID_TOKEN" >> $GITHUB_ENV
echo "OIDC_ID_TOKEN extracted successfully."
- name: Exchange OIDC ID Token for Scalr Token
id: exchange-token
run: |
wget -O scalr.zip https://github.com/Scalr/scalr-cli/releases/download/v0.17.1/scalr-cli_0.17.1_linux_amd64.zip
unzip scalr.zip
chmod +x ./scalr && mv ./scalr /usr/local/bin
echo "Exchanging ID token to assume temporary access token.."
scalr -quiet assume-service-account -id-token="$OIDC_ID_TOKEN" -service-account-email="${{ env.SCALR_SA_EMAIL }}"
echo "Scalr token saved successfully."
- name: Install OpenTofu
uses: opentofu/setup-opentofu@v1
- name: Generate Override Configuration
run: |
cat <<EOF > override.tf
terraform {
backend "remote" {
hostname = "${{ env.SCALR_HOSTNAME }}"
organization = "${{ env.SCALR_ENVIRONMENT }}"
workspaces {
name = "${{ env.SCALR_WORKSPACE }}"
}
}
}
EOF
echo "override.tf configuration generated successfully."
- name: Initialize and Run OpenTofu
run: |
tofu init
tofu planMake sure to update the following lines accordingly:
- SCALR_HOSTNAME:
<account>.scalr.io - SCALR_ENVIRONMENT:
<your-environment> - SCALR_WORKSPACE:
<your-workspace-name> - SCALR_SA_EMAIL:
<the email created in Scalr for the service account>
More Examples
See more examples of using OIDC here.
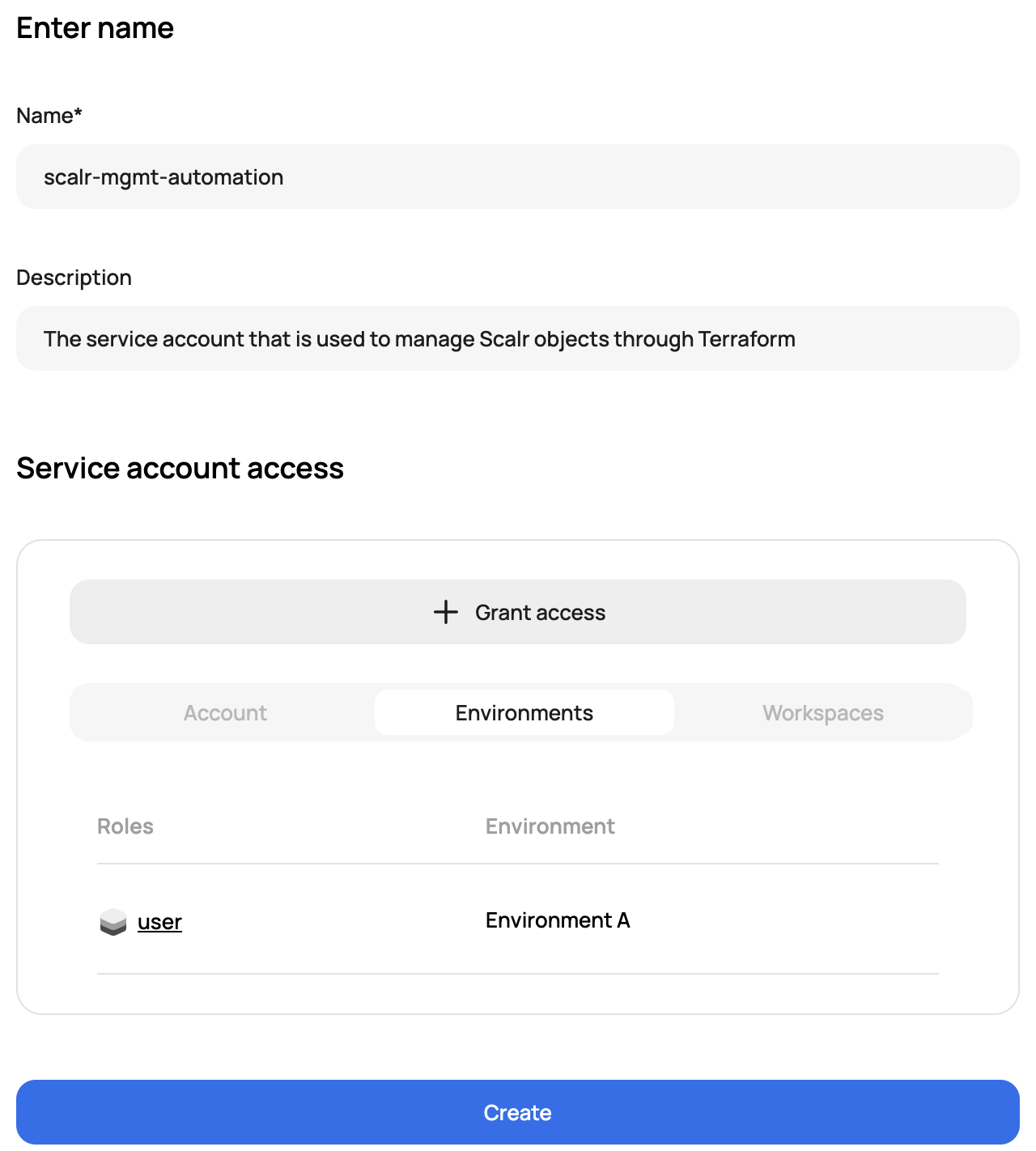
Service Accounts
A service account in Scalr is a local user that can be created, even if LDAP or SAML is enabled, to allow external services to call Scalr without the API token being linked to a named account. It is best practice to avoid using an employee or user API token to integrate with Scalr in the event the employee or user leaves the company. The service account will always remain active unless updated by an administrator. The permissions for a service account are granted the same way permissions are granted for users and teams through access policies.
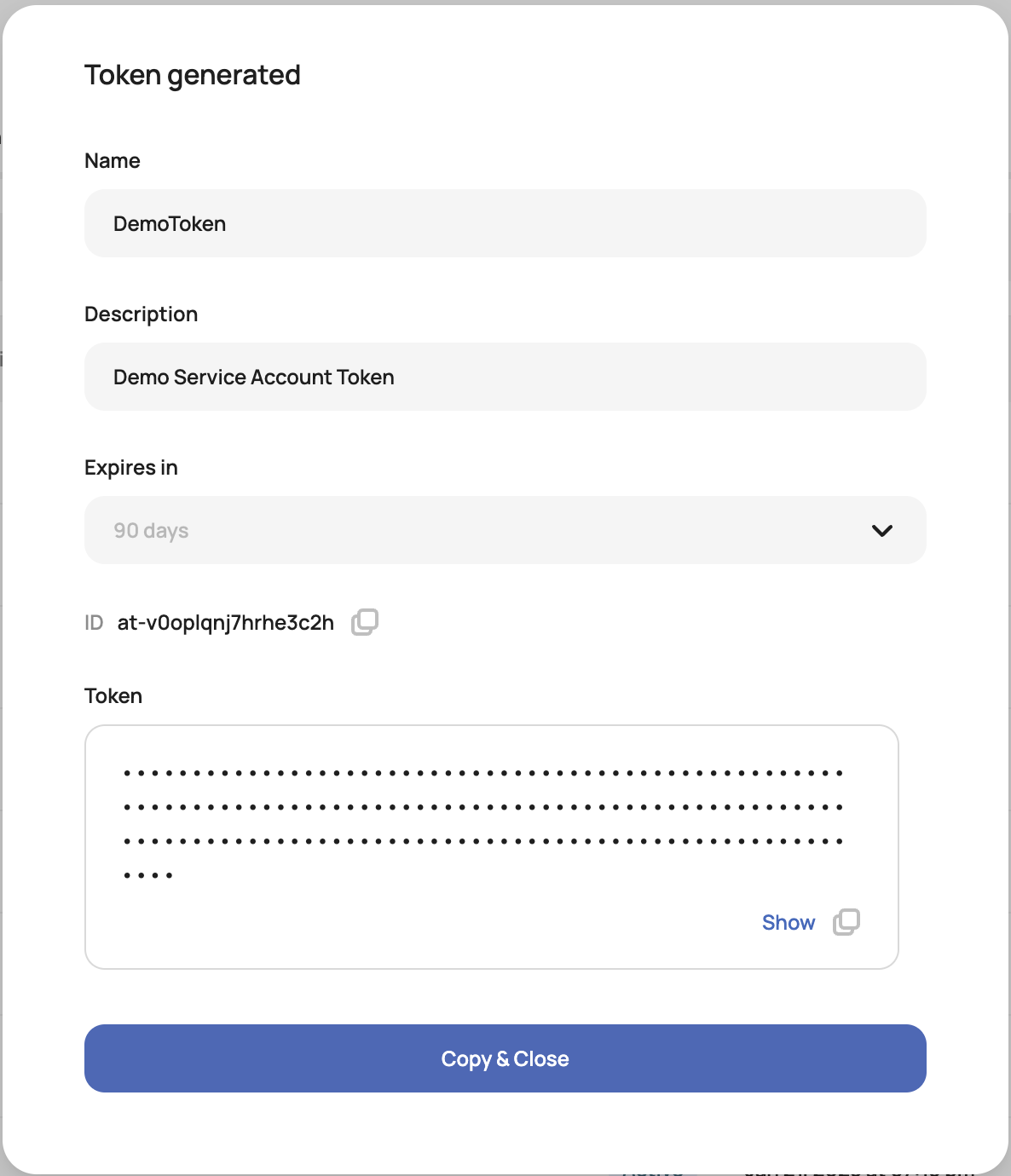
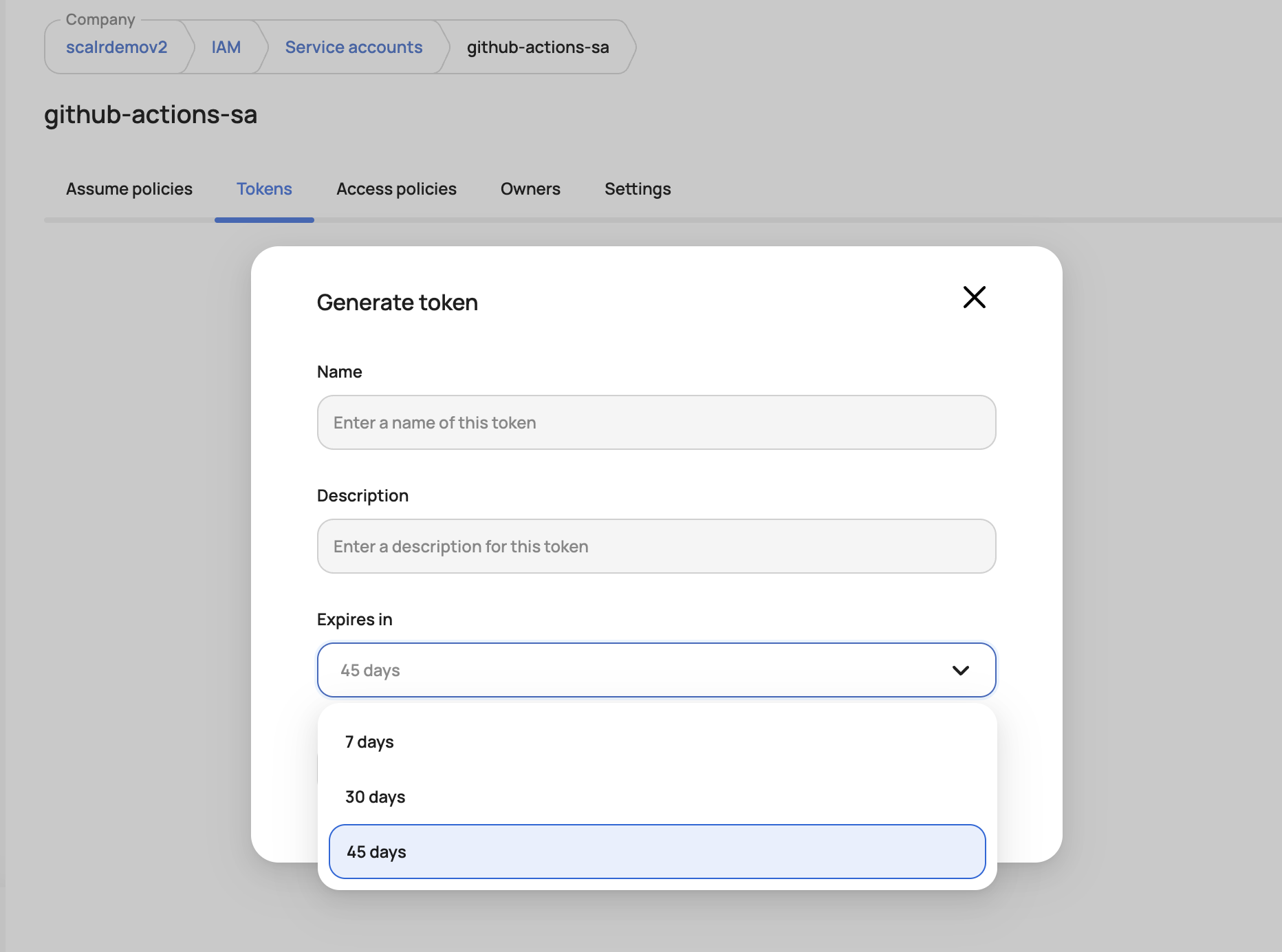
When a service account is created, an API token can be created with an expiration date to ensure tokens are rotated regularly:
Ownership
Team ownership can be assigned to service accounts, allowing teams to independently create and manage their own service accounts and assign them to specific environments.
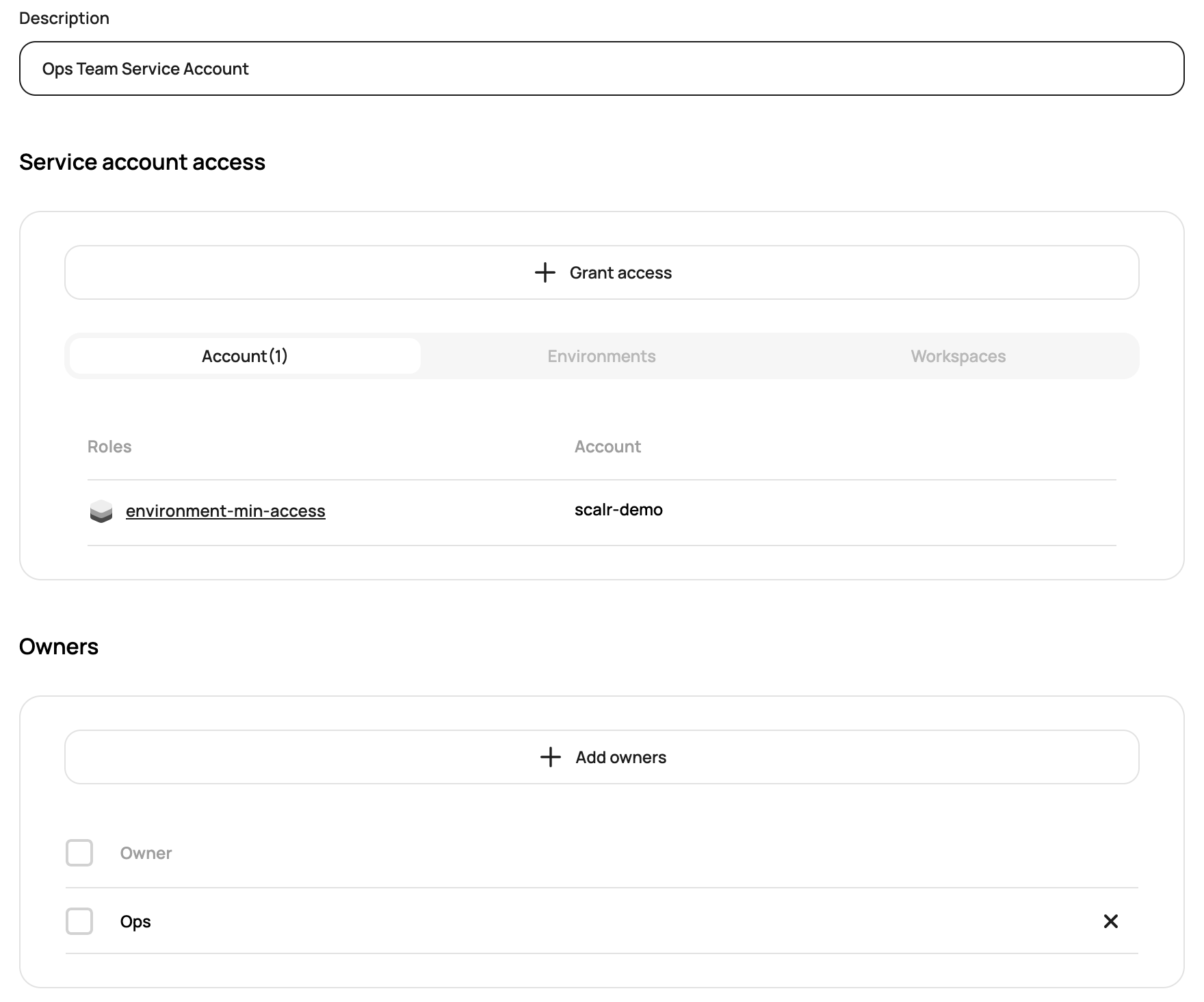
The following Terraform resource allows you to configure the IAM role needed to manage service accounts and assign owners.
resource "scalr_role" "owner" {
name = "service-account-owners"
description = "Allows user to manage service accounts and assign ownership"
permissions = [
"accounts:read",
"roles:read",
"service-accounts:create",
"service-accounts:delete",
"service-accounts:read",
"service-accounts:update",
"teams:read"
]
}The role must be granted to a team at the account scope.
WARNING: If a service account is created without team ownership, then anyone with the above permissions will be able to update, read, or delete it.
Admin users can be granted the ownership:bypass permission at the account level to bypass team ownership if they are not part of the team that owns the service account, but need to manage it.
Forcing Service Account Ownership
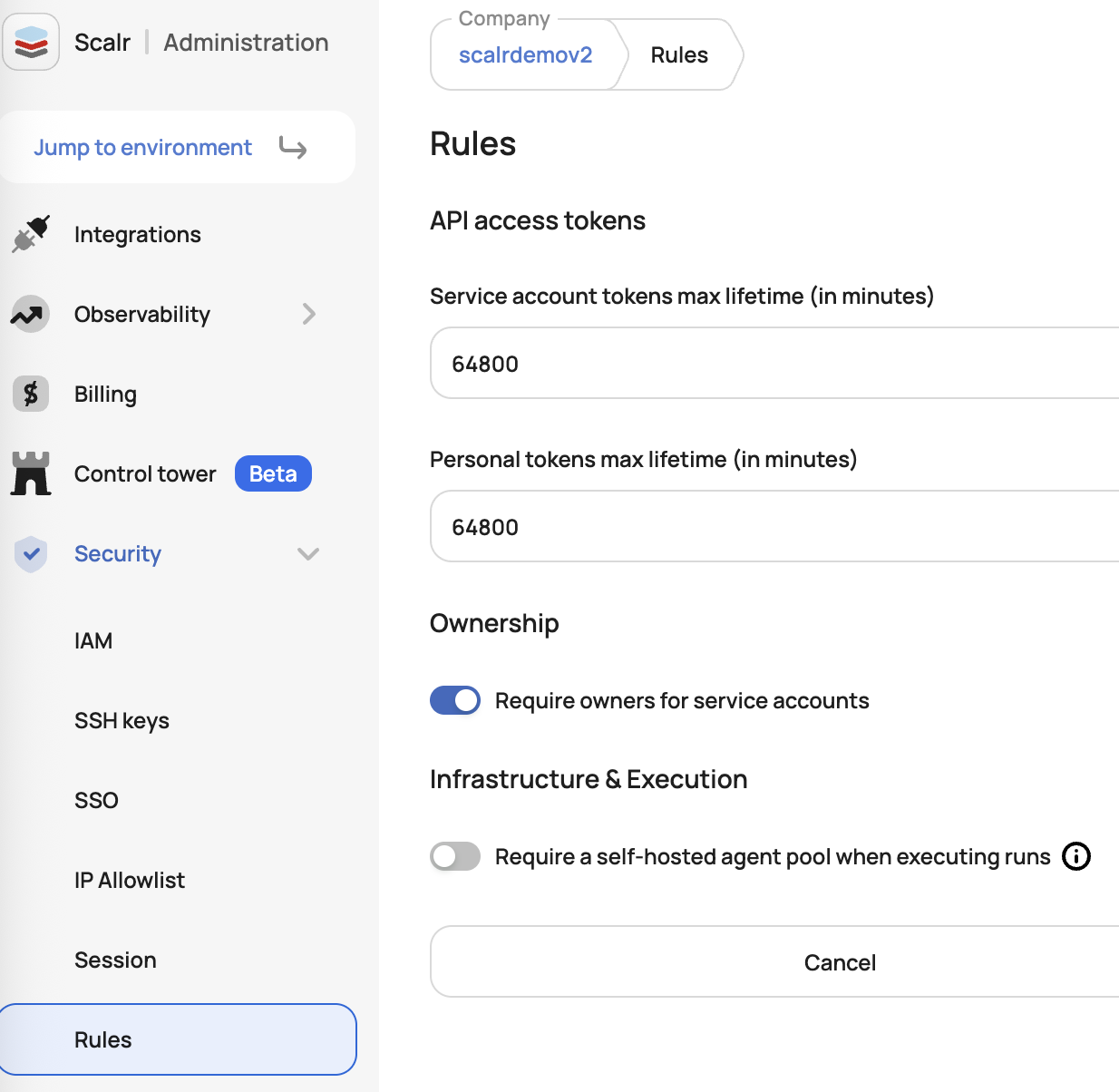
Forcing service account owners helps reduce the risks of orphaned API tokens or unauthorized access. When enabled, this rule requires at least one owner team to be assigned during service account creation or updates, with validation preventing operations without proper ownership assignment. Account admins can activate this feature through the "Require service account owners" toggle at the Scalr admin scope, under the securty rules page:
User Impersonation
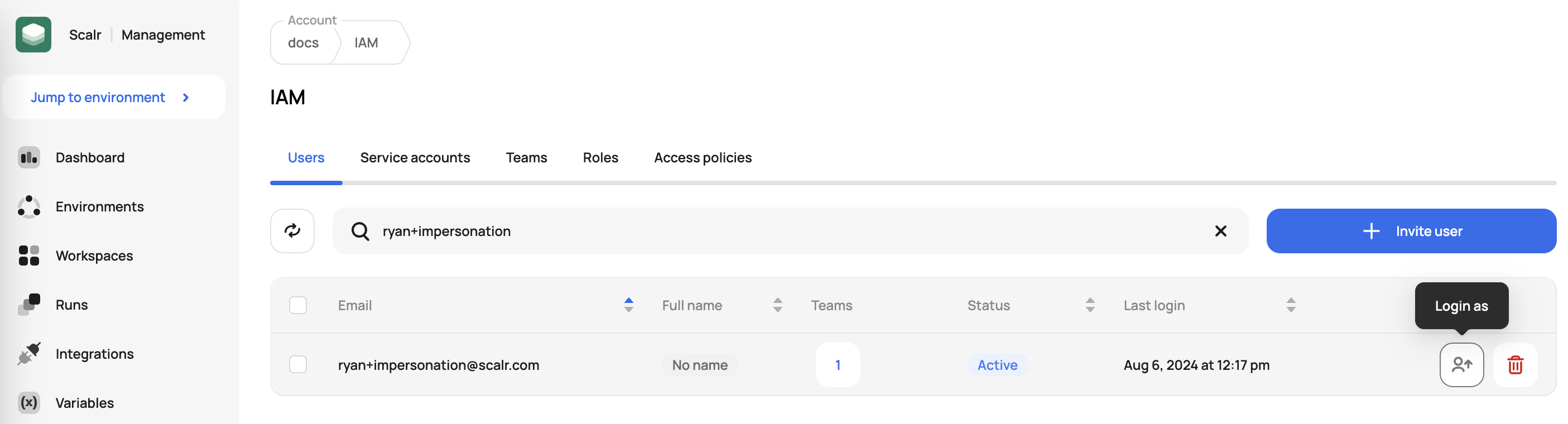
User impersonation enables administrators who manage team and user permissions to test the permissions they have assigned to users. To do this, the user attempting the impersonation must have the accounts:impersonate-users permission. Once given the correct permission, the impersonation can be done on the IAM->Users page by clicking "Login As" next to the user that should be impersonated:
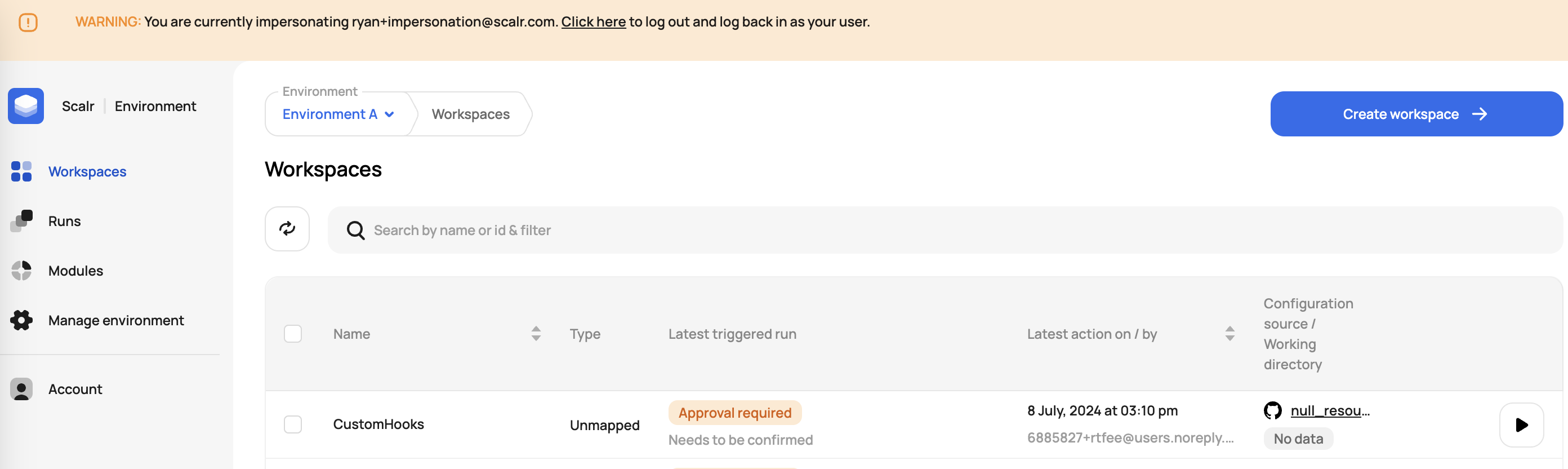
Once logged in as the user, the impersonator will be warned about the user they are logged in as and will be given the ability to switch back to their own user:
API Token Reports
The API token report in the reporting section of Scalr will help administrators identify Scalr API tokens that have not been rotated in a while or ever used to reduce the risk of unauthorized access. See more in the reporting section of the docs.
API Tokens Max Lifetime
Account admins can set maximum lifetimes for personal or service account tokens through the account security rules. The max lifetime is set in minutes and can be up to one year (525,600 minutes)
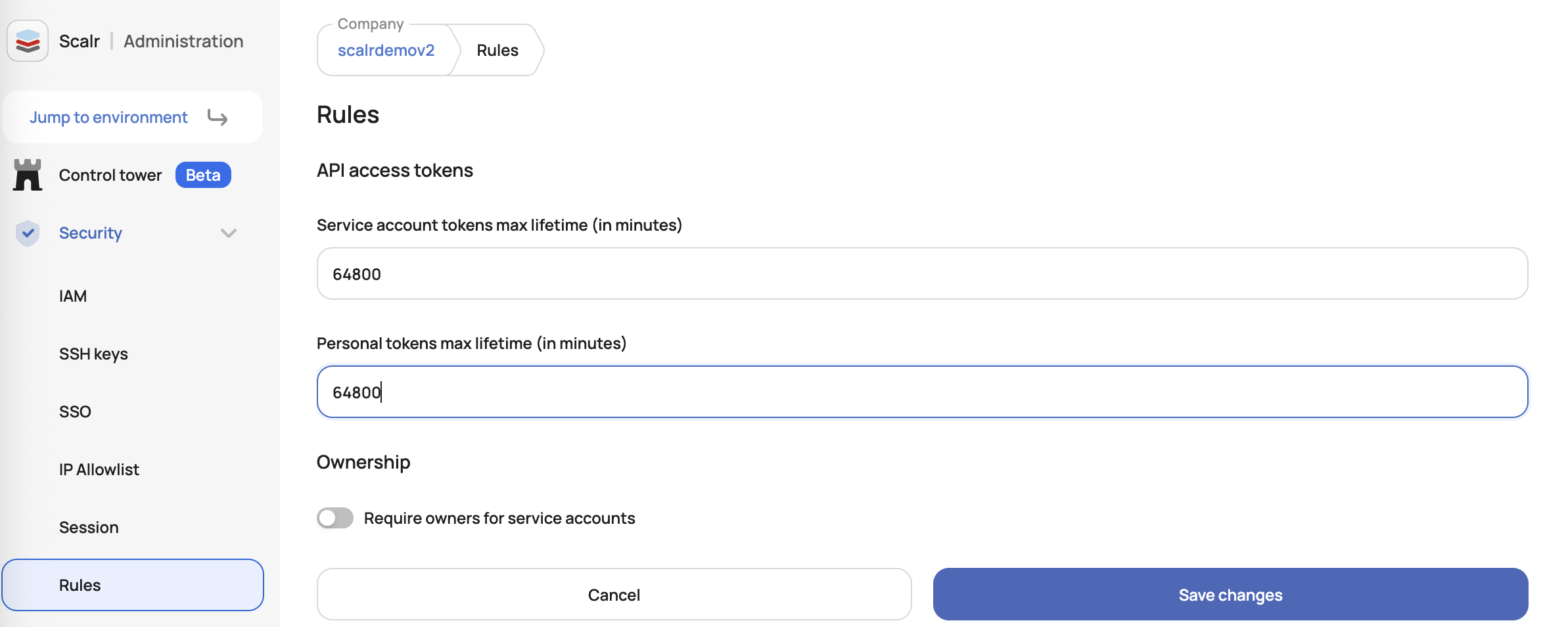
After it is set, users will not be able to set an API token lifetime higher than the limit specified:
Updated 4 months ago
