AWS Credentials
Scalr support credentials based on Access Keys or IAM Role Delegation.
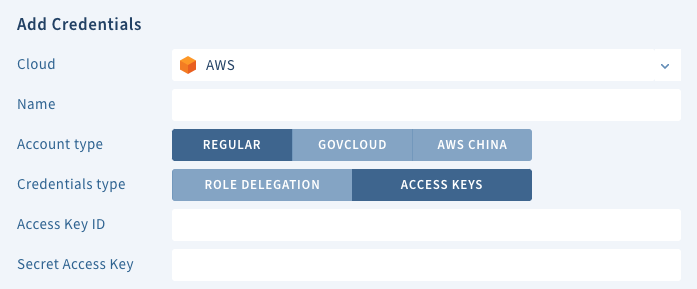
Access Key
For access key credentials an IAM user is required along with a suitable Role to grant permissions.
For information on creating an AWS user and the required policy please refer to AWS Identity and Access Management Documentation.
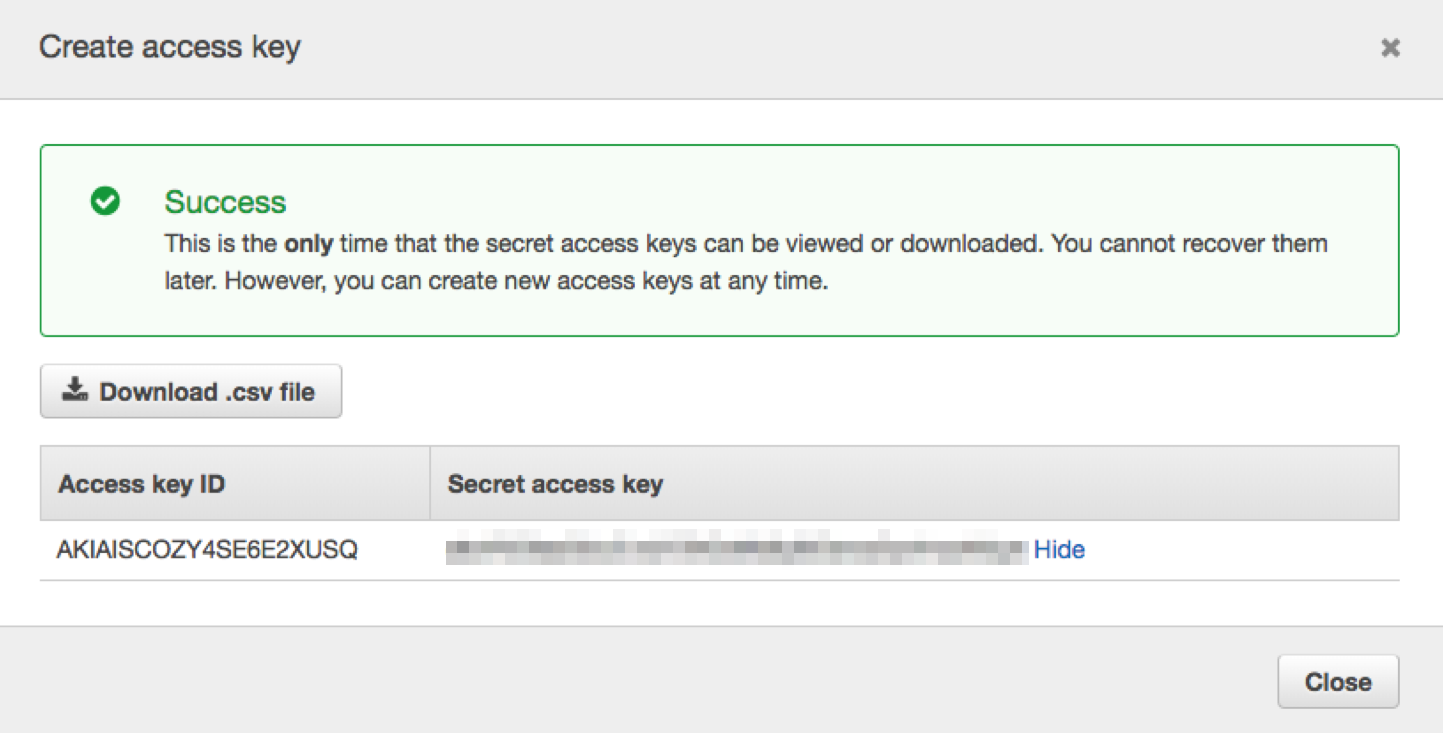
- In the EC2 console navigate to IAM -> Users -> Select a user -> Security Credentials -> Create Access Key
- Save the Access Key and Secret Key
- In Scalr in the “Add Credentials” dialogue select AWS, Click the “Access Keys” option and enter a name, the two keys and save.
IAM Role Delegation
NoteUsers on the SaaS system (scalr.io) will be creating a trusted relationship to a pre-configured role used by Scalr for all accounts.
For on-prem/self-hosted customers the role_delegation configuration must be added first. See IAM Role Delegation Configuration for more details.
For role delegation credentials the role must be created in AWS and the ARN of the role entered on the credentials screen in Scalr.
Please refer to IAM Role Delegation or details of setting up the role with a trusted relationship to the Principal account shown on the credentials screen. The external ID shown must be used in the role configuration.
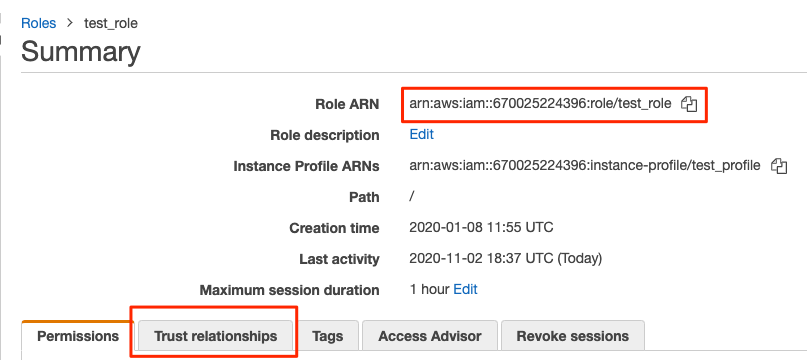
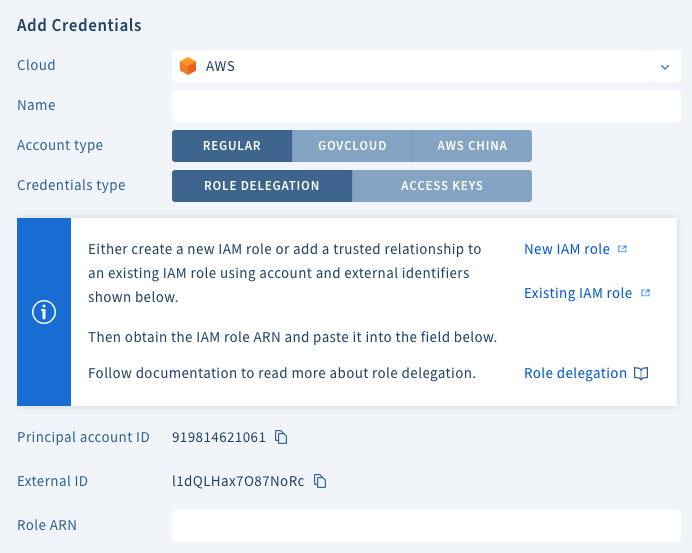
If you use the “New IAM Role” option to create the AWS role, you will see that it creates it with a root user as the trusted principal:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::919814621061:user/scalr-saas"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "<external-id>"
}
}
}
]
}This was done for backwards compatibility reasons, root is not required. You can update the user as needed: "AWS": "arn:aws:iam::919814621061:<some_user>"
Updated 5 months ago
