VCS Providers
VCS providers enable Scalr to access Terraform configuration files and OPA policies held in a version control system (VCS) such as Github, Gitlab, Bitbucket, and Azure DevOps. VCS providers are required if a GitOps model is desired. There is no extra configuration needed for Scalr to send checks back to VCS providers during the pull request process. VCS providers are created at the account and will be made available to all environments within the account or assigned to specific environments.
To manage VCS providers at the account scope, click on VCS providers:
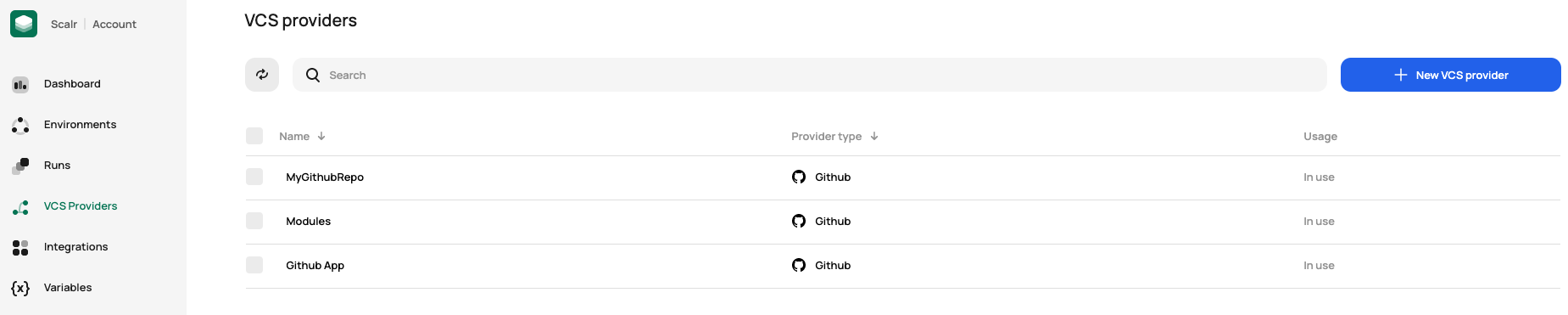
Currently supported VCS providers:
- GitHub SaaS
- GitHub Enterprise
- GitLab SaaS
- GitLab CE/EE
- Azure DevOps Services
- Bitbucket Cloud
- Bitbucket Data Center
To configure new VCS providers go to the “VCS provider” or “VCS” menu option and click “New VCS Provider”
Github
A Github VCS Provider is authenticated as a Github App.
-
Click Github, enter the provider name, and click create.
-
Select the Github organization to use after being redirected.

- Select which repositories should be used then click install and authorize.
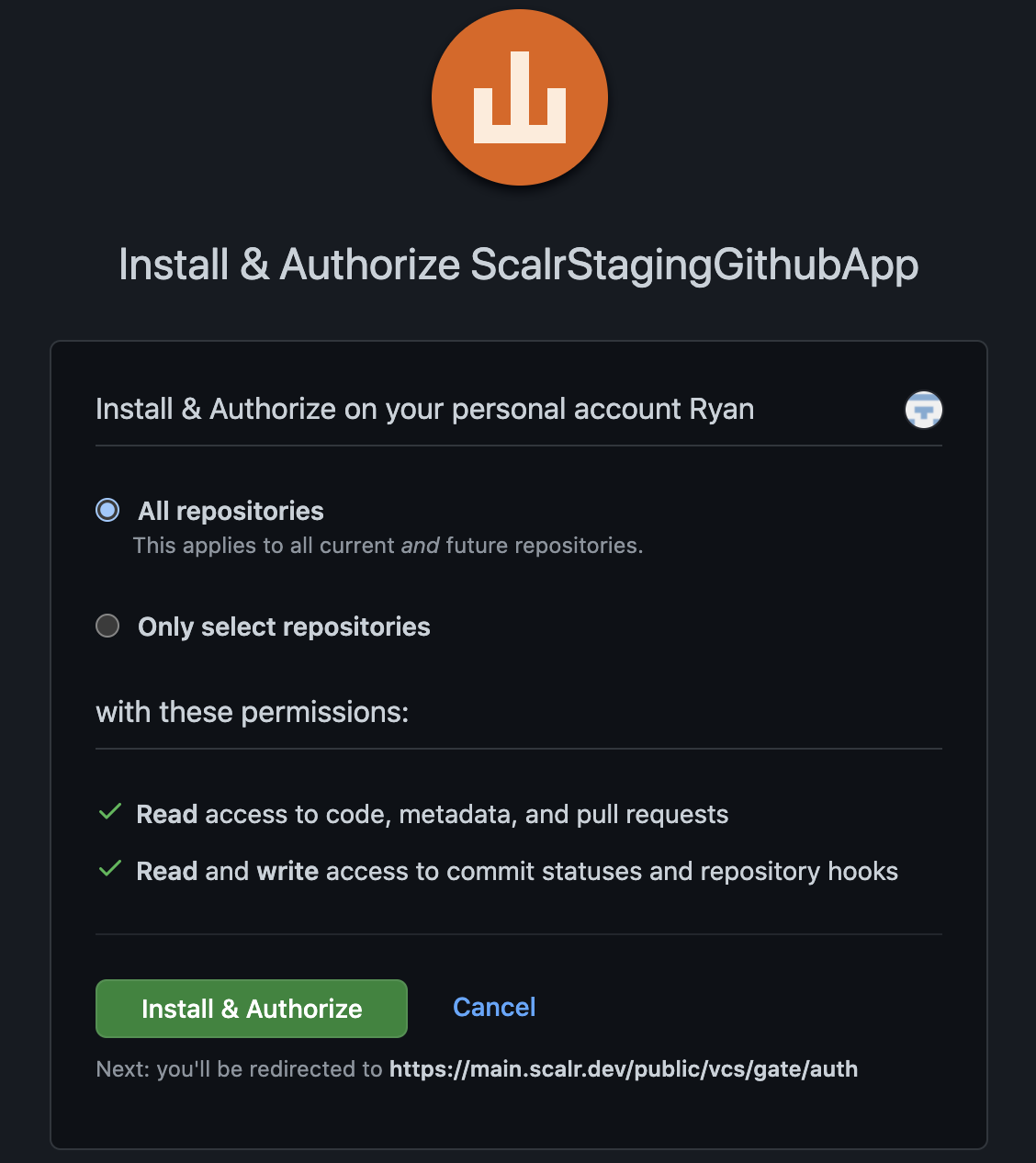
- After authorizing, Github will automatically redirect back to Scalr.
Gitlab
A Gitlab VCS provider is authenticated against an OAuth application.
-
Click Gitlab or Gitlab Enterprise and enter the provider name and, for Enterprise, the URL.
-
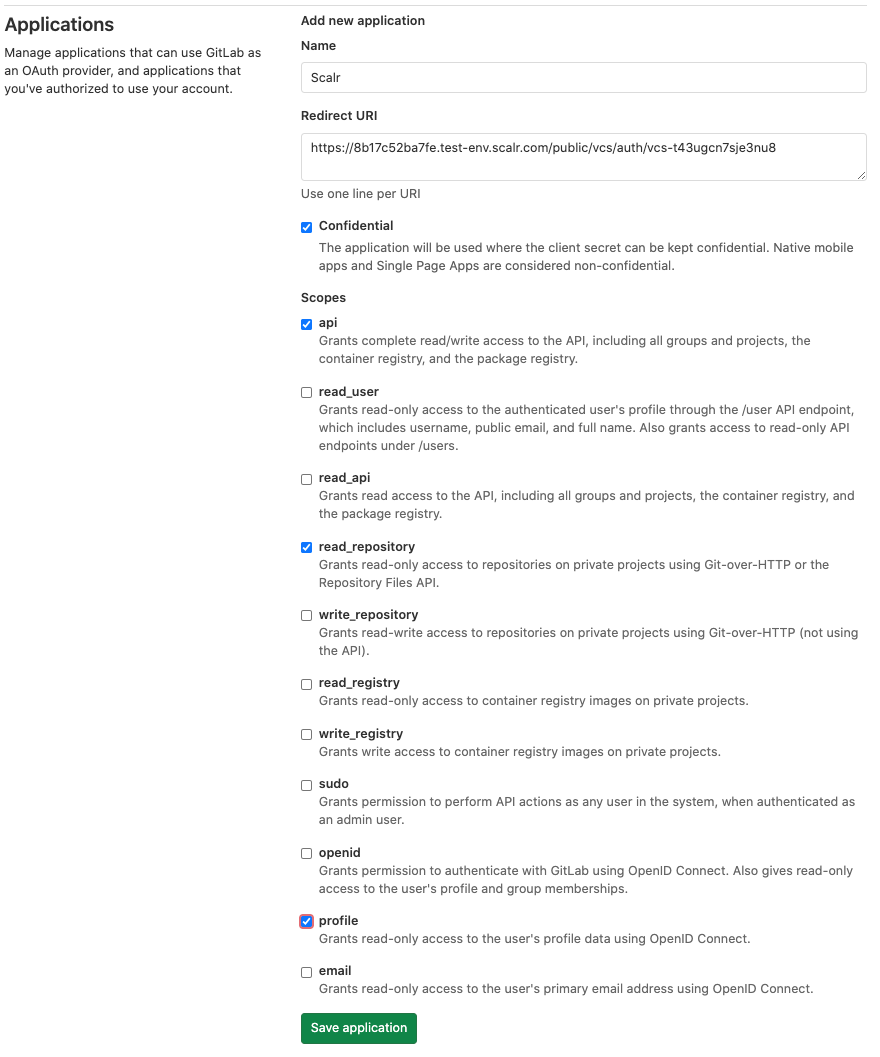
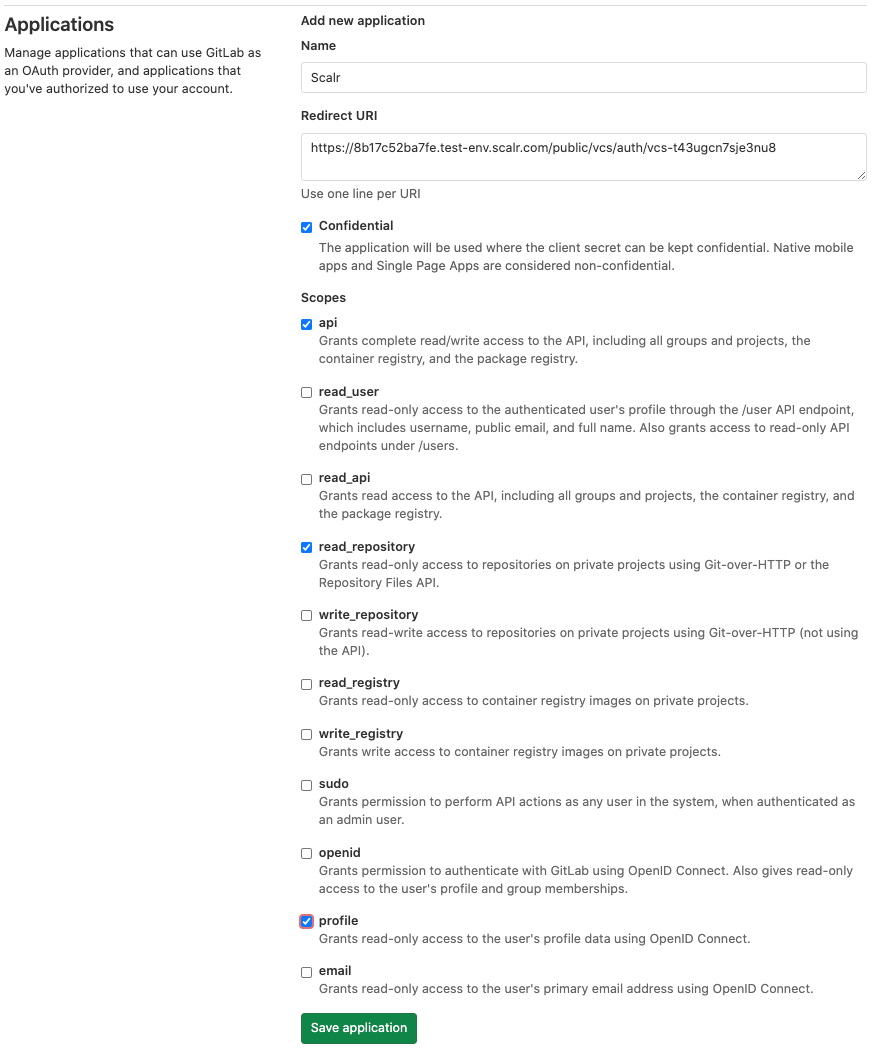
Copy the callback URL, click the “register a new OAuth application” link and register a new OAuth app in Gitlab.
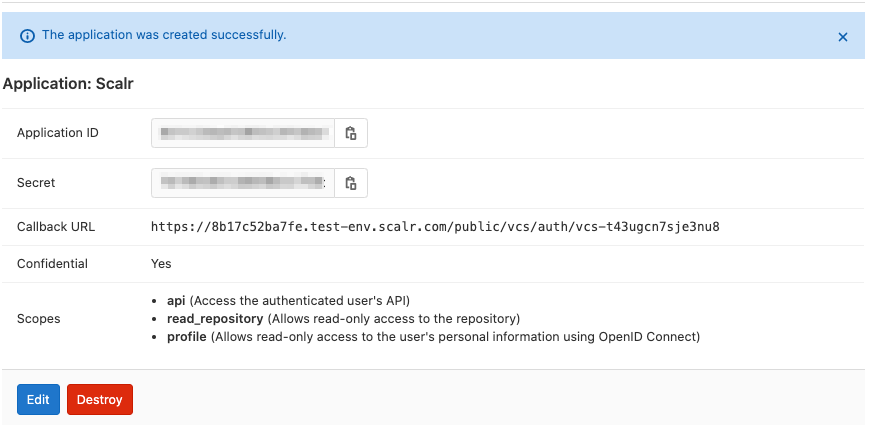
Enable the following permissions in the application configuration:- Confidential
- api
- read_repository
- profile
For Gitlab Enterprise check these options in the network settings (Admin Area):
- Allow requests to the local network from web hooks and services
- Allow requests to the local network from system hooks
- Save and then copy Application ID and Secret.
-
Go back to Scalr, enter the Id and secret.
-
On clicking “create” a redirection back to Gitlab occurs to complete the authorization.
Azure Devops Services
Azure Project Level PermissionsThe user who performs the actions below to connect to Azure DevOps must have project administrator permissions in Azure.
An Azure Devops Services VCS provider is authenticated against an OAuth application.
-
Click Azure Devops Services and enter the provider name.
-
Copy the callback URL, click the “register a new OAuth application” link and register a new OAuth app in Azure Devops.
- Below is an example app configuration
- Only two scopes are required for Scalr, Code (read) and Code (status)
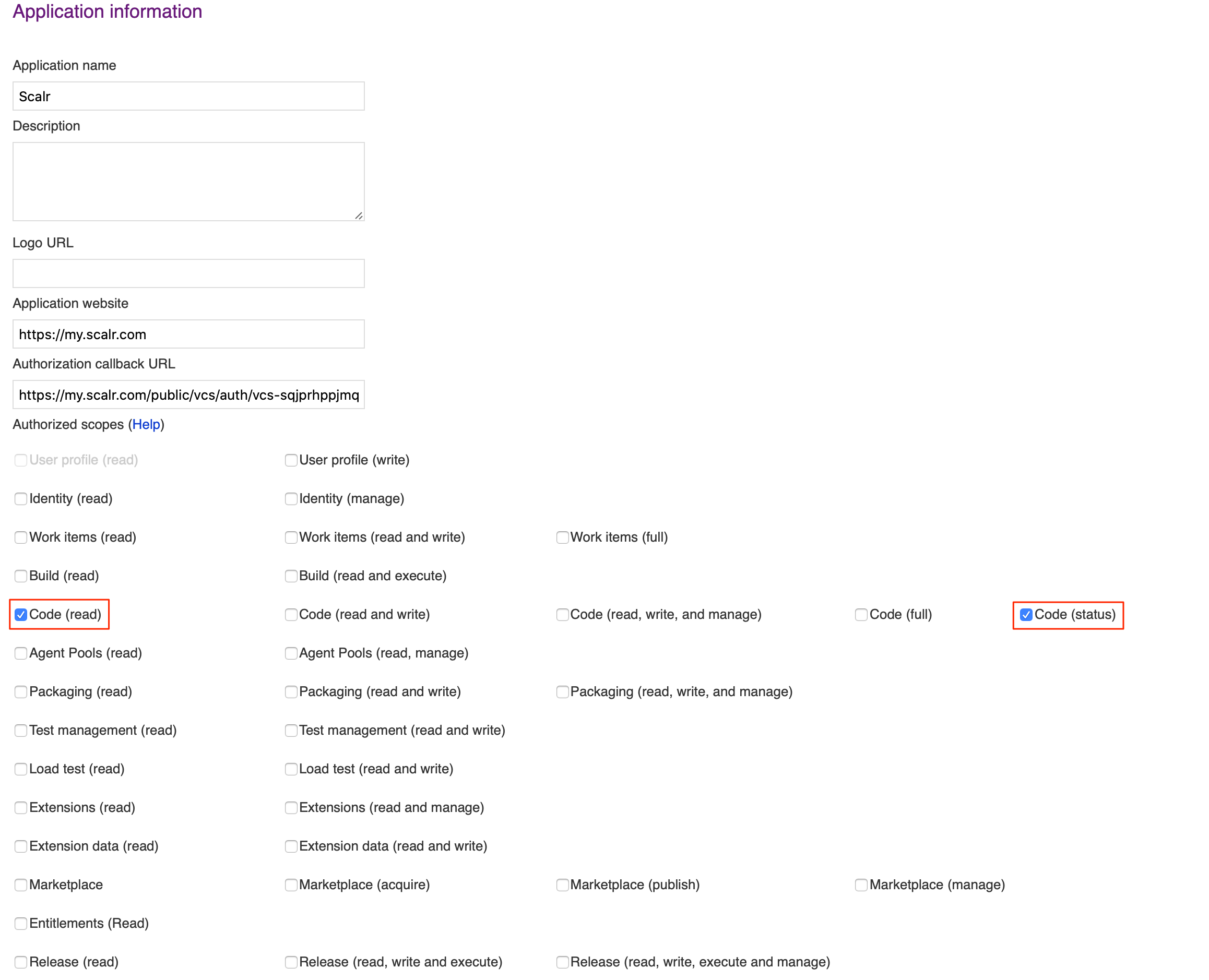
- Click Create and then copy the Application ID and Client Secret.
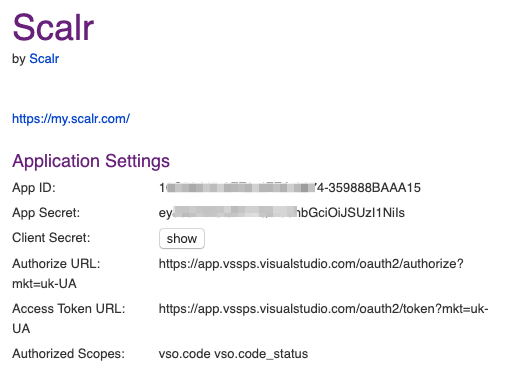
-
Go back to Scalr, enter the Id and secret.
-
On clicking “create” a redirection back to Azure Devops occurs to complete the authorization.
Bitbucket Cloud
A Bitbucket Cloud VCS provider is authenticated against an OAuth application.
-
Click Bitbucket and enter the provider name.
-
Copy the callback URL.
-
Login to Bitbucket in a new window and register a new OAuth consumer (Settings –> OAuth).
- Copy in the call back URL
- Set the permissions as shown below
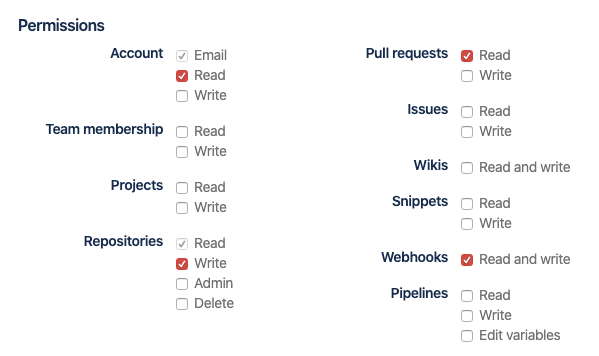
- Click Save and then copy the Application ID and Client Secret.
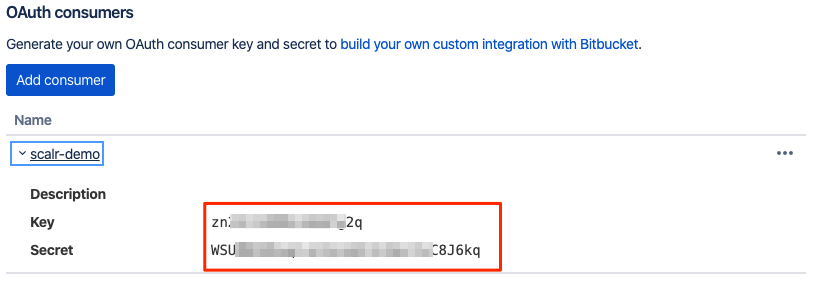
-
Go back to Scalr, enter the Id and secret.
-
On clicking “create” a redirection back to Bitbucket occurs to complete the authorization.
Bitbucket Data Center
A Bitbucket Data Center VCS provider is authenticated using a personal access token.
-
Click Bitbucket Data Center and enter the provider name and URL of Bitbucket.
-
Login to Bitbucket Data Center by clicking on the link provided and create a new personal access token.
- Set the permissions as shown below
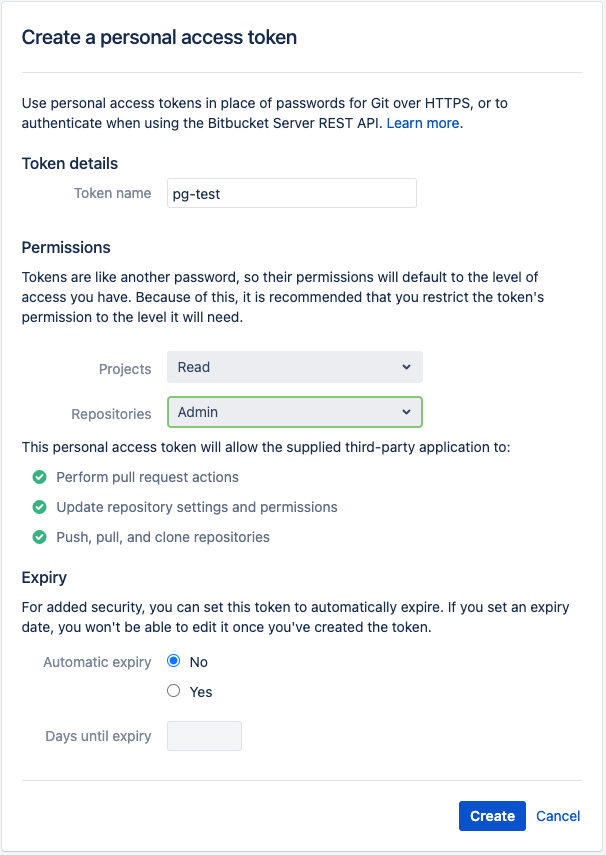
- Click Create and then copy the token.
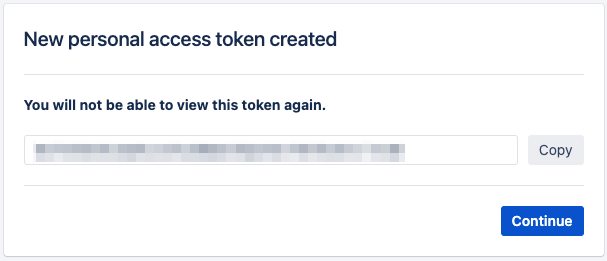
- Go back to Scalr, enter the token and click “Create”.
Github Enterprise
-
Click Github Enterprise and enter the provider name and URL.
-
Copy the callback URL, click the “register a new OAuth application” link and register a new OAuth app in Github.
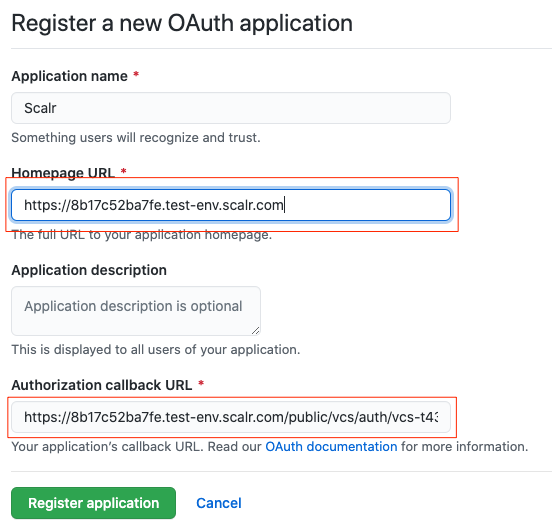
- Click on “Generate a new client secret and copy the client ID and client secret.
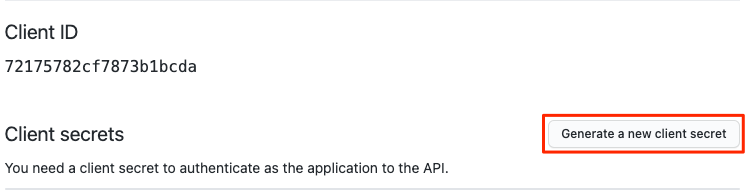
- Go back to Scalr and paste the values into the form.
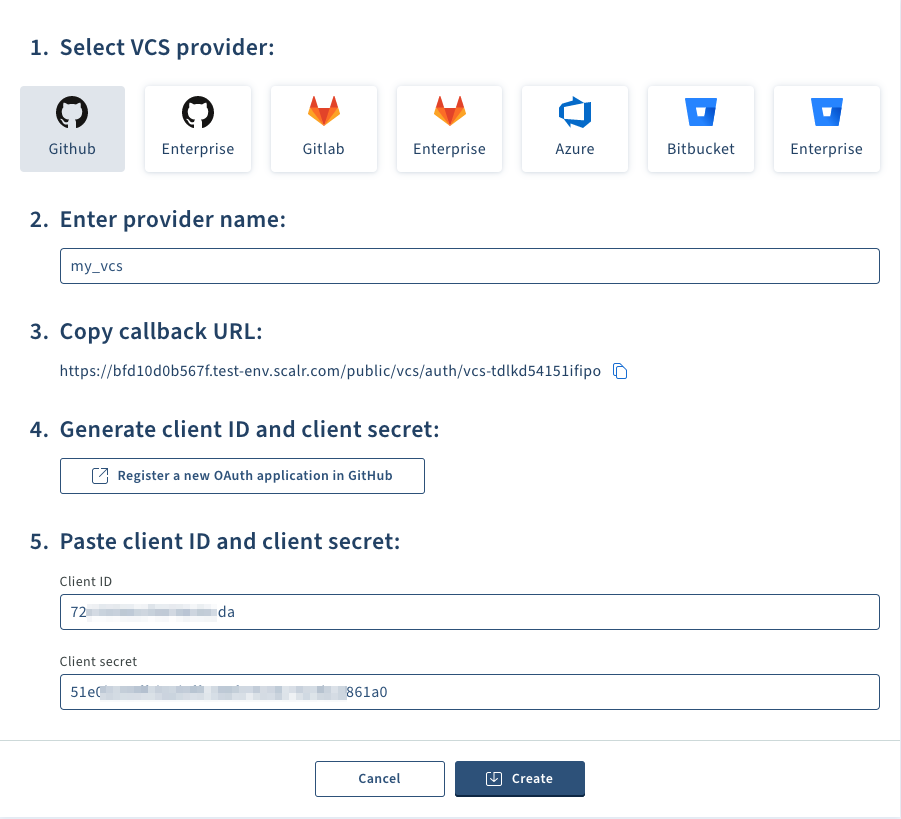
- On clicking “create” a redirection back to Github occurs to complete the authorization.
Updated 7 months ago
